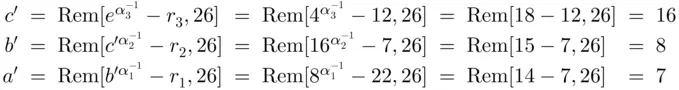
Therefore, the first cipher text character corresponds to 7, and is thus is “H.”
Now, we must update the rotor settings: 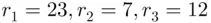 .
.
If the settings were such that 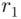 was 25, the updating process would proceed as follows:
was 25, the updating process would proceed as follows: 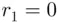 ,
, 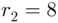 ,
, 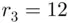 .
.
As mentioned above, an interesting aspect about the Enigma enciphering scheme is the fact that deciphering a message follows the exact same process.
2.8 Modern Enciphering Systems
With the advent and ubiquity of computer‐based encryption systems, cryptanalysis has shifted the emphasis from attacks based purely on the ciphering scheme to attacks on other aspects of cryptosystems, such as authentication, key exchanges, and digital signatures. We will detail some of these techniques later in the book, after the basis for modern ciphers, authentication, and digital signatures are developed.
1 2.1 Encipher the plain text message “encode” using the following Cipher: schemes:Caesar cipher with .Caesar cipher with .(See Solution 2.1.)
2 2.2 Using the Scytale cipher with k = 2, encipher the plain text message “encode”. Compare your results with those from Problem 2.1. (See Solution 2.2.)
3 2.3 Decode the following cipher text, given that it has been produced by a Caesar cipher: JRYYQBAR (See Solution 2.3.)
4 2.4 Is any additional security gained by enciphering a message using two monoalphabetic ciphers with different keys in succession? (See Solution 2.4.)
5 2.5 Encipher the first sentence of Homer's “Odyssey” using a Scytale cipher with key = 7.TELL ME O MUSE, of that ingenious hero who traveled far and wide after he had sacked the famous town of Troy.(See Solution 2.5.)
6 2.6 Explain how frequency distribution can be used to determine if a given entry of cipher text was produced using a substitution cipher or a transposition cipher.(See Solution 2.6.)
7 2.7 Use the Vigenère cipher with keyword “ODYSSEY” to encipher the first sentence of Homer's “Odyssey.” Compare the cipher text with the results obtained from Problem 2.5. (See Solution 2.7.)
8 2.8 Decipher the message below, using the fact that the keyword ‘CIPHER’ was used to encode it.VPXZG ZRTYM JGIHF XFDZT HOZHW CLOEQ EHALV MMNDS IF(See Solution 2.8.)
9 2.9 Suppose Caesar sends a message to one of his generals, and the message contains only one letter. What can you say about the message's security and why? (See Solution 2.9.)
10 2.10 Does the Enigma machine perform substitution enciphering or transposition enciphering? Explain. (See Solution 2.10.)
11 2.11 Ignoring the plugboard, how many possible initial settings are there for the three‐rotor Enigma machine? (See Solution 2.11.)
12 2.12 Using the rotor and reflector permutation sets, along with the initial rotor settings, from the example in Section 2.7, encipher the following message: “move out!”. (See Solution 2.12.)
13 2.13 Find the period of the given cipher text, given that it was enciphered by the Vigenère cipher (see Section 2.6).LVCKO GXKRR ITSKC XIPOG GZLCB GYXFC AYGDI RBMAU CFYAC FIPGM RRXFO JPSIB WELDI QDJPO USORA IHGCX PSFSD MMXEL NEJSX RVIJE GISXA KRZOH MXI (See Solution 2.13.)
14 2.14 Using the results of Problem 2.13, determine the keyword used to encipher the passage above (See Solution 2.14.)
15 2.15 Use the Enigma Machine with initial settings given in Section 2.7to decipher the following message: YDDMYU (See Solution 2.15.)
16 2.16 Take a page of your favorite book and estimate the number of characters on the page. Count the number of times the letters e, t, a, and o appear on that page and calculate their relative frequencies. Compare your results with Table 2.1. (See Solution 2.16.)
1 2.1Encode HQFRGHEncode ZIXJYZ
2 2.2 Since , the number of rows is two. Thus, the message is encoded as follows:ECDECDNOENOE
3 2.3 We use a brute‐force attack, with results shown in the following table. The value corresponds to a Caesar shift of magnitude .kJRYYQBAR1IQXXPAZQ2HPWWOZYP3GOVVNYXO4FNUUMXWN5EMTTLWVM6DLSSKVUL7CKRRJUTK8BJQQITSJ9AIPPHSRI10ZHOOGRQH11YGNNFQPG12XFMMEPOF13WELLDONE14VDKKCNMD15UCJJBMLC16TBIIALKB17SAHHZKJA18RZGGYJIZ19QYFFXIHY20PXEEWHGX21OWDDVGFW22NVCCUFEV23MUBBTEDU24LTAASDCT25KSZZRCBS26JRYYQBARAfter investigating the entries in the table, the only intelligible message exists for . The plain text message is “well done.”
4 2.4 No. For example, if a message is enciphered with a key of 4, and the resulting cipher text is enciphered again using a key of 8, the final cipher text will be the same as if the message was enciphered with a key of 12.
5 2.5 Since the key is 7, we know that we need 7 rows. For the number of columns, count up the total number of characters and check if it is divisible by 7. Since it is not, we must add 4 Zs to the end. Therefore, we have 91 characters, and . Thus, we need 13 columns. Writing the message out in columns, we get the following matrix:TMHNRAFIRAETREUAIOVADHCFOOLSTOWEREEKAWYLEIUHLAAHEMNZMONSOLNFADOOZEFGHTEDTDTUFZOTEERDWESHSTZAfter unwrapping, we obtain the encrypted message:TMHNR AFIRA ETREU AIOVA DHCFO OLSTO WEREE KAWYL EIUHLAAHEM NZMON SOINF ADOOZ EFGHT EDTDT UFZOT EERDW ESHST Z
6 2.6 Transposition ciphering will produce cipher text with roughly the same frequency distribution as the English language. Substitution ciphering, with a polyalphabetic cipher for example, will yield frequencies that can be much different, since the plain text letters are actually changed instead of reordered. Therefore, if the distribution “flattened,” we can assume a substitution cipher was used. If it does not, we can assume that a transposition cipher was used.
7 2.7 The computations for the first few letters are shown.Keyword:ODYSSEYODYPlain text:TellmeomusCipher text:HHJDEIMAXQContinuing the process, the corresponding cipher text isHHJDE IMAXQ WQJRV DRAFK CBHMM KLCFR UZGXP OYBDD IBTDPSFHUW GCSXX CFKCZ SHQOF IWVXF SIYEG YQHRU FGJRF RW
8 2.8 We obtain the plain text by subtracting the cipher text from the keyword:Keyword:CIPHERCIPHCipher text:VPXZGZRTYMPlain text:thiscipherWorking the rest of it out, we obtain the message.“this cipher is easy to break if one knows the keyword”
9 2.9 The message has perfect security, because the message could be any of the 26 letters of the alphabet. That is, knowledge of the cipher text does not give any information regarding the message. Alternatively, one can think intuitively that “the key is as long as the message.”
10 2.10 Substitution enciphering, because each letter of the plain text message is obtained by substituting different cipher text characters. Transposition enciphering is the reordering of the same letters, whereas substitution enciphering doesn't necessarily use the same characters.
11 2.11 Three rotors with 26 possible initial settings each = initial settings = 17 576. Since the three rotors can be interchanged, there are six ways to order them. Therefore, we have a total of different initial settings.
Читать дальше

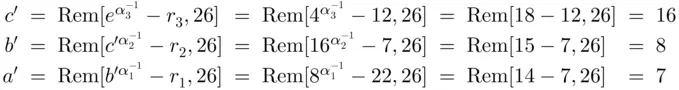
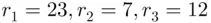 .
.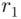 was 25, the updating process would proceed as follows:
was 25, the updating process would proceed as follows: 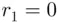 ,
, 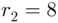 ,
, 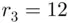 .
.










