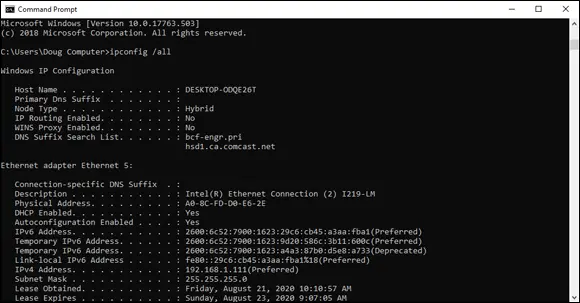
FIGURE 1-2:Display the MAC address of a network adapter.
Two types of data link layer devices are commonly used on networks:
Bridge: An intelligent repeater that's aware of the MAC addresses of the nodes on either side of the bridge and can forward packets accordingly.
Switch: An intelligent hub that examines the MAC address of arriving packets to determine which port to forward the packet to.
Another important layer 2 concept is the idea of virtual local area networks (VLANs). VLANs allow you to create separate isolated networks that share devices. For example, you can create separate VLANs for your accounting and sales departments, but use the same switch to connect computers in each VLAN. Computers in the account VLAN won't be able to communicate with computers in the sales VLAN, even though the computers are on the same switch.
The network layer handles the task of routing network messages from one computer to another. The two most popular layer 3 protocols are IP (which is usually paired with TCP) and IPX (typically paired with SPX for use with Novell and Windows networks).
Network layer protocols provide two important functions: logical addressing and routing. The following sections describe these functions.
An important function of the data link layer is to make sure that two computers don’t try to send packets over the network at the same time. If they do, the signals will collide with each other, and the transmission will be garbled. Ethernet accomplishes this feat by using CSMA/CD. This phrase is a mouthful, but if you take it apart piece by piece, you’ll get an idea of how it works.
Carrier Sense means that whenever a device wants to send a packet over the network media, it first listens to the network media to see whether anyone else is already sending a packet. If it doesn’t hear any other signals on the media, the computer assumes that the network is free, so it sends the packet.
Multiple Access means that nothing prevents two or more devices from trying to send a message at the same time. Sure, each device listens before sending. However, suppose that two devices listen, hear nothing, and then proceed to send their packets at the same time? Picture what happens when you and someone else arrive at a four-way stop sign at the same time. You wave the other driver on, he or she waves you on, you wave, he or she waves, you both wave, and then you both go at the same time.
Collision Detection means that after a device sends a packet, it listens carefully to see whether the packet crashes into another packet. This is kind of like listening for the screeching of brakes at the four-way stop. If the device hears the screeching of brakes, it waits a random period of time and then tries to send the packet again. Because the delay is random, two packets that collide are sent again after different delay periods, so a second collision is unlikely.
CSMA/CD works pretty well for smaller networks. After a network hits about 30 computers, however, packets start to collide like crazy, and the network slows to a crawl. When that happens, the network should be divided into two or more separate sections that are sometimes called collision domains.
As I mention earlier, every network device has a physical address — a MAC address — assigned to the device at the factory. When you buy a network interface card to install into a computer, the MAC address of that card is fixed and can’t be changed. So what happens if you want to use some other addressing scheme to refer to the computers and other devices on your network? This is where the concept of logical addressing comes in; with a logical address, you can access a network device by using an address that you assign.
Logical addresses are created and used by network layer protocols such as IP. The network layer protocol translates logical addresses to MAC addresses. For example, if you use IP as the network layer protocol, devices on the network are assigned IP addresses, such as 207.120.67.30. Because the IP protocol must use a data link layer protocol to send packets to devices, IP must know how to translate the IP address of a device to the device’s MAC address.
 You can use the
You can use the ipconfigcommand (refer to Figure 1-2) to see the IP address of your computer. The IP address shown in that figure is 192.168.1.111. Another way to display this information is to use the System Information command, best found by pressing the Windows key and searching for “System Information.” The IP address is highlighted in Figure 1-3. Notice that the System Information program displays a lot of other useful information about the network besides the IP address. For example, you can also see the MAC address and what protocols are being used.
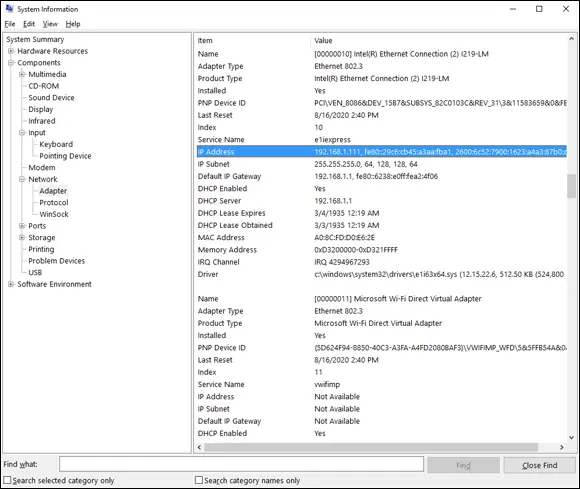
FIGURE 1-3:Find network information from System Information.
Although the exact format of logical addresses varies depending on the protocol being used, most protocols divide the logical address into two parts:
Network address: Identifies which network the device resides on
Device address: Identifies the device on that network
In a typical IP address — say, 192.168.1.102 — the network address is 192.168.1, and the device address (called a host address in IP) is 102.
Routing comes into play when a computer on one network needs to send a packet to a computer on another network. In this case, a router is used to forward the packet to the destination network. In some cases, a packet may have to travel through several intermediate networks in order to reach its final destination network. You can find out more about routers in Chapter 4of this minibook.
An important feature of routers is that you can use them to connect networks that use different layer 2 protocols. For example, a router can be used to send a packet from an Ethernet to a token ring network. As long as both networks support the same layer 3 protocol, it doesn’t matter whether their layer 1 and layer 2 protocols are different.
 A protocol is considered routable if it uses addresses that include a network part and a host part. Any protocol that uses physical addresses isn’t routable because physical addresses don’t indicate to which network a device belongs.
A protocol is considered routable if it uses addresses that include a network part and a host part. Any protocol that uses physical addresses isn’t routable because physical addresses don’t indicate to which network a device belongs.
The transport layer is where you find two of the most well-known networking protocols: TCP (typically paired with IP) and SPX (typically paired with IPX). As its name implies, the transport layer is concerned with the transportation of information from one computer to another.
The main purpose of the transport layer is to ensure that packets are transported reliably and without errors. The transport layer does this task by establishing connections between network devices, acknowledging the receipt of packets, and resending packets that aren’t received or are corrupted when they arrive.
Читать дальше


 You can use the
You can use the 
 A protocol is considered routable if it uses addresses that include a network part and a host part. Any protocol that uses physical addresses isn’t routable because physical addresses don’t indicate to which network a device belongs.
A protocol is considered routable if it uses addresses that include a network part and a host part. Any protocol that uses physical addresses isn’t routable because physical addresses don’t indicate to which network a device belongs.










