Ross Anderson - Security Engineering
Здесь есть возможность читать онлайн «Ross Anderson - Security Engineering» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Security Engineering
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:3 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
Security Engineering: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Security Engineering»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
secure? Understand how to engineer dependable systems with this newly updated classic
In
Cambridge University professor Ross Anderson updates his classic textbook and teaches readers how to design, implement, and test systems to withstand both error and attack.
This book became a best-seller in 2001 and helped establish the discipline of security engineering. By the second edition in 2008, underground dark markets had let the bad guys specialize and scale up; attacks were increasingly on users rather than on technology. The book repeated its success by showing how security engineers can focus on usability.
Now the third edition brings it up to date for 2020. As people now go online from phones more than laptops, most servers are in the cloud, online advertising drives the Internet and social networks have taken over much human interaction, many patterns of crime and abuse are the same, but the methods have evolved. Ross Anderson explores what security engineering means in 2020, including:
How the basic elements of cryptography, protocols, and access control translate to the new world of phones, cloud services, social media and the Internet of Things Who the attackers are – from nation states and business competitors through criminal gangs to stalkers and playground bullies What they do – from phishing and carding through SIM swapping and software exploits to DDoS and fake news Security psychology, from privacy through ease-of-use to deception The economics of security and dependability – why companies build vulnerable systems and governments look the other way How dozens of industries went online – well or badly <l

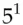
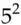 =
= 4
4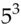

 6
6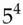

 2
2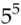

 3
3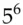

 1
1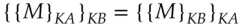 . Alice can take the message
. Alice can take the message 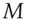 and encrypt it with her key
and encrypt it with her key  to get
to get 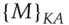 which she sends to Bob. Bob encrypts it again with his key
which she sends to Bob. Bob encrypts it again with his key 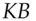 getting
getting 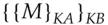 . But the commutativity property means that this is just
. But the commutativity property means that this is just 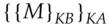 , so Alice can decrypt it using her key
, so Alice can decrypt it using her key 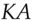 getting
getting 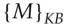 . She sends this to Bob and he can decrypt it with
. She sends this to Bob and he can decrypt it with 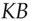 , finally recovering the message
, finally recovering the message 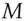 .
.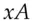 and sends Bob
and sends Bob 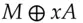 while Bob returns
while Bob returns 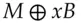 and Alice finally sends him
and Alice finally sends him 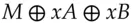 , then an attacker can simply exclusive-or these three messages together; as
, then an attacker can simply exclusive-or these three messages together; as  = 0 for all
= 0 for all 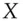 , the two values of
, the two values of 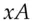 and
and 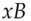 both cancel out, leaving the plaintext
both cancel out, leaving the plaintext 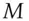 .
.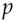 is hard, then we can use discrete exponentiation as our encryption function. For example, Alice encodes her message as the primitive root
is hard, then we can use discrete exponentiation as our encryption function. For example, Alice encodes her message as the primitive root 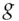 , chooses a random number
, chooses a random number 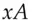 , calculates
, calculates 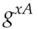 modulo
modulo 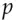 and sends it, together with
and sends it, together with 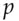 , to Bob. Bob likewise chooses a random number
, to Bob. Bob likewise chooses a random number 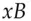 and forms
and forms 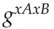 modulo p, which he passes back to Alice. Alice can now remove her exponentiation: using Fermat's theorem, she calculates
modulo p, which he passes back to Alice. Alice can now remove her exponentiation: using Fermat's theorem, she calculates 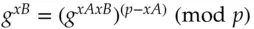 and sends it to Bob. Bob can now remove his exponentiation, too, and so finally gets hold of
and sends it to Bob. Bob can now remove his exponentiation, too, and so finally gets hold of 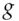 . The security of this scheme depends on the difficulty of the discrete logarithm problem. In practice, it can be tricky to encode a message as a primitive root; but there's a simpler way to achieve the same effect.
. The security of this scheme depends on the difficulty of the discrete logarithm problem. In practice, it can be tricky to encode a message as a primitive root; but there's a simpler way to achieve the same effect.









