The abundance of definitions for security terms is the result of various aspects and attributes that an interested party may want to emphasize in the definition of a concept. Also, many security‐ and privacy‐related concepts and terms evolved as the security paradigms changed in time, particularly in the way IT security was addressed. Appendix Aincludes a table showing different definitions for common security terms as provided by known standards and glossaries.
This is an indication of the development of a field where a foundation for defining the basic concepts is still evolving. However, it is necessary to have more consistent definitions among related and dependent terms. An appropriate balance between comprehensive and extended definitions is needed also for promoting terms that are useful to users and general public, not only to security experts and researchers. These terms are needed in communicating, writing, and understanding news and documents dealing with security policies, directives, instructions, and guidance.
Often, the lack of knowledge of the definitions or lack of unique definitions prompts for defining these terms in each industry. For example, DOE published a glossary of concepts including a set of cybersecurity terms in [DOE 2014a]. Several terms are taken from other documents, or they are adapted for the energy sector use. There is a problem when these dictionaries are not continuously updated; when new terms may appear, some terms could become obsolete or be changed in the referenced glossary. Therefore, one solution is to check the definitions and their maintenance status of these terms. The security team needs to agree on the basic terms to avoid language confusion and avoid rolling out ambiguous activities.
Since some security terms do not have common definitions or new updates emerge, we recommend previewing the definition of the most current dictionaries of security terms and concepts as defined by known standard organizations such as the International Organization for Standardization (ISO)/IEC, the Internet Engineering Task Force (IETF), and International Society of Automation (ISA). Often the glossary adopted by an organization may need to be revised. Definitions of related security terms (cybersecurity, threat, vulnerability, asset, countermeasure, exposure, security service, etc.) are also available in published guides maintained by security professionals such as [Harris 2013], [Krutz 2004]. Figure 2.11shows a visual representation of the relationships among different security concepts (terms). Definitions of the terms are provided in [CC 2.3] (see also Appendix A).
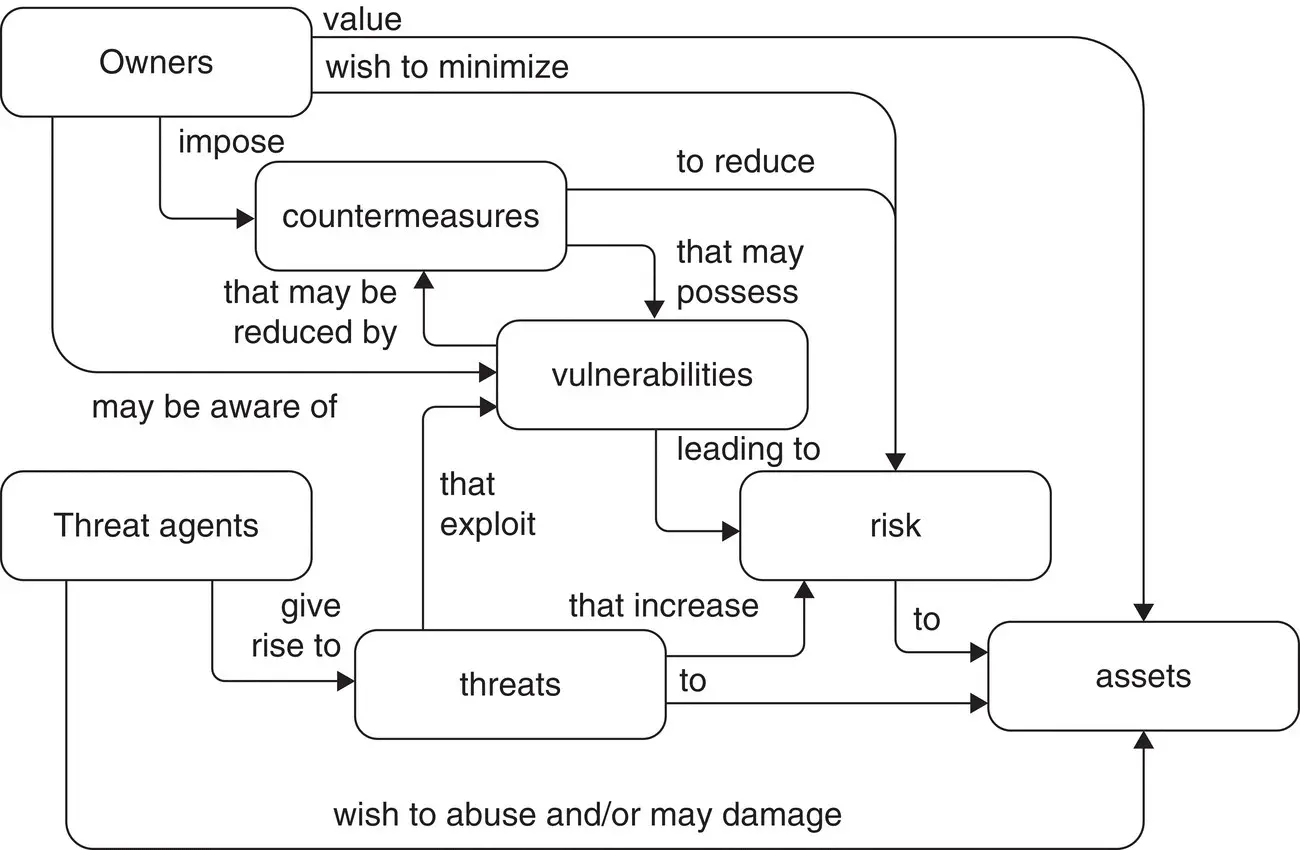
Figure 2.11 Security concepts and relationships.
Source: [CC 2.3]. Public Domain.
In addition, security and privacy concepts have to be understood by users, security designers, and managers; otherwise misunderstanding creates confusion or ambiguity in communication that undermines the successful implementation of security and privacy programs.
The assets may have vulnerabilities that may be exploited by a threat agent leading to risk that can damage the asset. The owner of the assets wants to minimize the risk and uses countermeasures (controls or safeguards). Applying the right countermeasure can eliminate the vulnerability and exposure and thus reduce the risk. One issue is that eliminating the threat agent may not be possible, but it is possible to protect the asset and prevent the threat agent from exploiting vulnerabilities within the asset's environment.
These terms and definitions of security terms continue to change and evolve with technology developments, emerging new technologies, and research trends. This work [Von Solms 2013] discusses the similarities and differences between these terms: cybersecurity, information security, and communications security. The authors argue that cybersecurity goes beyond the boundaries of traditional information security to include not only the protection of information resources but also that of other assets, including the reference to the human factor. Figure 2.12illustrates graphically the relationships among these concepts.
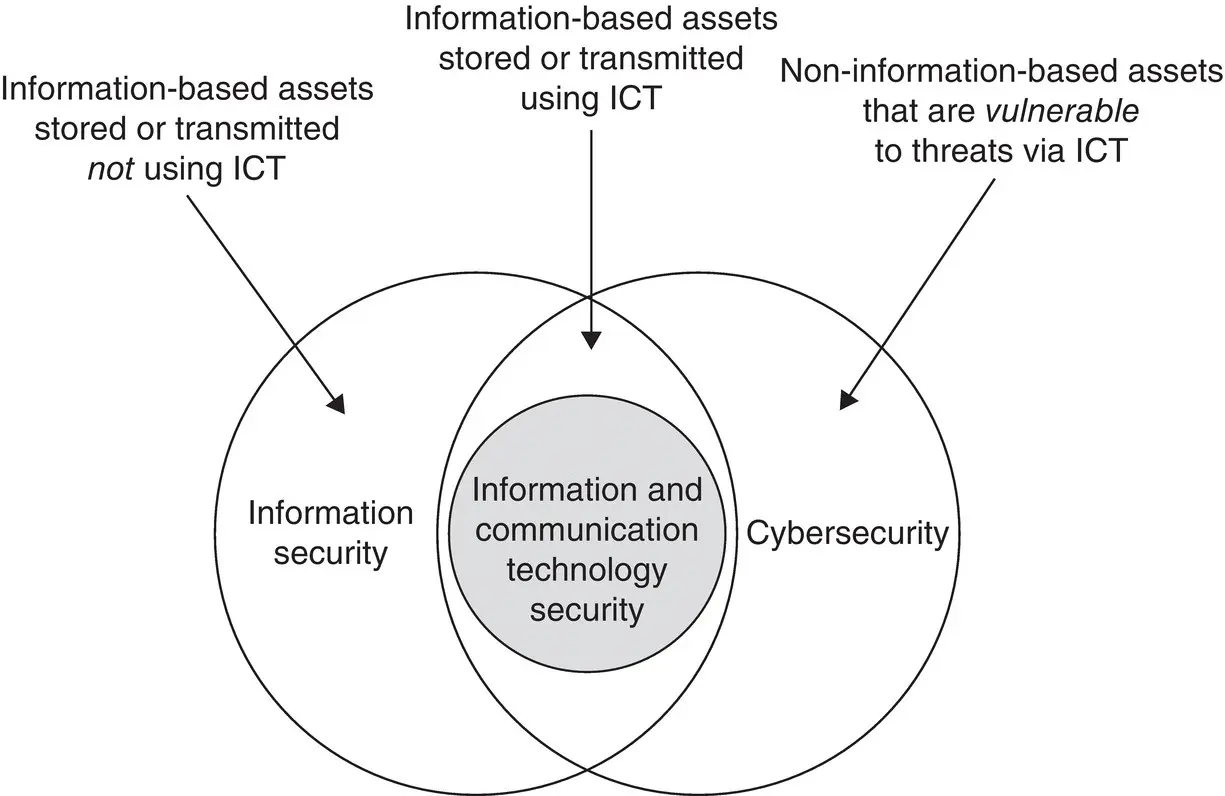
Figure 2.12 Information security and cybersecurity relationship.
Source: [Von Solms 2013]. © 2013, Elsevier.
This work [Craigen 2014] is another attempt to provide a new definition for the term cybersecurity from a multidisciplinary perspective as follows:
Cybersecurity is the organization and collection of resources, processes, and structures used to protect cyberspace and cyberspace‐enabled systems from occurrences
that misalign de jure from de facto property rights.
However, the definition is missing the point that cybersecurity is a field of research, an industry, and a societal issue. There are many different theoretical and interpretational aspects that could or even should be considered when discussing cybersecurity as a concept and a term.
Appendix A includes several definitions promoted by organizations and glossaries including DOE. Although there is no universally accepted nor straightforward definition of cybersecurity and other related terms, we need to understand these definitions and views.
2.2.3 Cybersecurity Evolution
In the past, before Internet technologies became the mainstream technology, there were few risks and limited definitions for security and security expertise. Security evolved from protecting a file, an application, or a computer to protecting a larger area that comprises many computers, networks, organizations, and people.
The security field evolved from an obscure term known initially only to military and governments to include organizations of all kinds, the public, and the globe. For some time, few professionals were involved in security matters. Today organizations and governments are continuously searching for better security professionals to protect their information and their other resources. A review of the terms and definitions for cybersecurity is well documented in [Bay 2016].
Security definitions evolved from simple terms like computer security, IT security, and information security to more recent terms identified as cyber security or cybersecurity, the last term winning, although the cyber security term is still used in some publications [Franscella 2013].
As we observed earlier, security terms are differently defined in many books and guidances; therefore we use the terms security, cybersecurity, and information security in this book based on the well‐known standards. We acknowledge that there are subtleties in these definitions. NIST guidelines for the Smart Grid use the term cybersecurity (e.g. [NISTIR 7628], [NISTIR 7628r1]). However, we discuss the information security based on definitions included in standards. The ISO/IEC definition is as preservation of information attributes such as confidentiality, integrity, availability, authenticity, accountability, non‐repudiation, and reliability [ISO/IEC 27000]. Another defines security as a property of a system by which confidentiality, integrity, availability, accountability, authenticity, and reliability are achieved [ISO 15443].
We also discuss security in the context of an environment determining the setting and circumstances of all interactions and influences with the system of interest [ISO/IEC 42010]. Other issues that need to be understood and managed include the interdependence of cybersecurity and reliability of the power grid.
Читать дальше














