Another example is the home area network (HAN), which is enabled by open and interoperable standards. The use of open and interoperable standards is key to accessibility, availability, innovation, and widespread adoption. Standards provide:
Cybersecurity that protects systems and data.
Interoperable components that protect investments in technology and enable growth in the HAN ecosystem.
Competition among consumer products companies, which drives down costs while increasing choices for consumers.
Reduced maintenance and support costs caused by proprietary solutions.
A common understanding of information exchange.
Interoperability of DERs with HAN is key to advancing Smart Grid applications. For purposes of the HAN specifications, a DER is a HAN device with functionality that measures and communicates its full energy production. DERs generate electricity, which may provide for all or a portion of the premises' electrical needs. A DER may be interconnected to the utility electric distribution system, and any net energy flowing on to the electric grid may be recorded in a separate channel on the AMI meter. Additional information about AMI components and open Smart Grid can be found in [UCAIUG], [NETL 2008].
The DER production may also be managed by an EMS that optimizes the premises energy consumption. Also, open standards are key enablers for the success of the IoT, as it is for any kind of M2M communication.
One crucial aspect is how to protect privacy in open systems. Personal privacy can also be compromised when information is disclosed in open systems. Solutions require analysis of several factors. Compelling goals such as accountability, economic growth, free speech, and privacy should be included in any overall decision about whether to disclose information [Swire 2004].
In addition, a designer has to consider regulations on privacy policy, corporate responsibility, and user trust because compliance is required by several committees (e.g. UN Human Rights Watch Group). A committee established in the United States in August 2013 has the task to review policies and regulations on Intelligence and Communications Technologies to support commitment to privacy and civil liberties and maintain the public trust in the United States.
2.4 Smart Grid Cybersecurity: A Perspective on Comprehensive Characterization
Two major views of Smart Grid security include cybersecurity and physical security [P2030 2011], [DOE 2015a]. Although there are differences on these views, there are common aspects and many interdependencies between these views that require a unified view of security. Another perspective is that power grid information security and protection has aspects of both ICS and IT systems. Although both ICS and IT systems require information security services to combat malicious attacks, the specifics of how these services are used for the power grid depend upon appropriate risk assessment and risk control. Distinct types of attacks targeting ICS and IT systems as well as different performance requirements of these systems determine a specific priority order of the security services implemented for each system. In addition, the Smart Grid trends toward the integration of the operational and business systems require a unified view of security based on risk management instead of applying the old approach of separate techniques for IT and ICS systems. A unified approach based on risk management techniques is described in [Ray 2010].
Therefore, solutions for designing cybersecurity into the Smart Grid with the vision of surviving a cyber incident while sustaining critical energy delivery functions must be carefully engineered and require novel solutions [Hawk 2014], [Ray 2010].
2.4.1 Forces Shaping Cybersecurity
Cybersecurity progress requires understanding of all its aspects as a vector quantity including the forces shaping its evolution as identified in [Agresti 2010]:
Rebranding exercise means cybersecurity is replacing information security and information assurance as the term of choice; this move promises an engagement with the public.
Organizational imperative means that offering information assurance in cyberspace, although infeasible, might be required because of assets ownership changes in contracts and service agreements with outside parties.
Cyberspace domain redefinition means becoming part of a virtual world that:Refers to the virtual environment of information and interactions between people [FERC 2009]Includes the physical world such as CPS and IoT [NSF 2014], [Lee 2010], [IoT], [EC‐EPoSS 2008]In this context, the Smart Grid and process control systems are types of CPS [CPS 2014], and smart meters and home automation are examples of the IoT applications.
National defense priority requires securing cyberspace, which is a matter of survival for any nation; one strategy is providing new interaction models such as engaging the public and private sectors to collaborate on the protection of critical infrastructures.
Figure 2.13is a view of these forces categorized as style (rebranding) and substance (organizational imperative, cyberspace domain, and national defense priority). These forces require us to consider new tasks to include engaging the public, externalizing (globalization) the organization, understanding the virtual domain, and establishing protection strategies for critical infrastructures. Due to cyberspace prominence and collaboration, securing cyberspace must be a personal, organizational, national, and global priority.
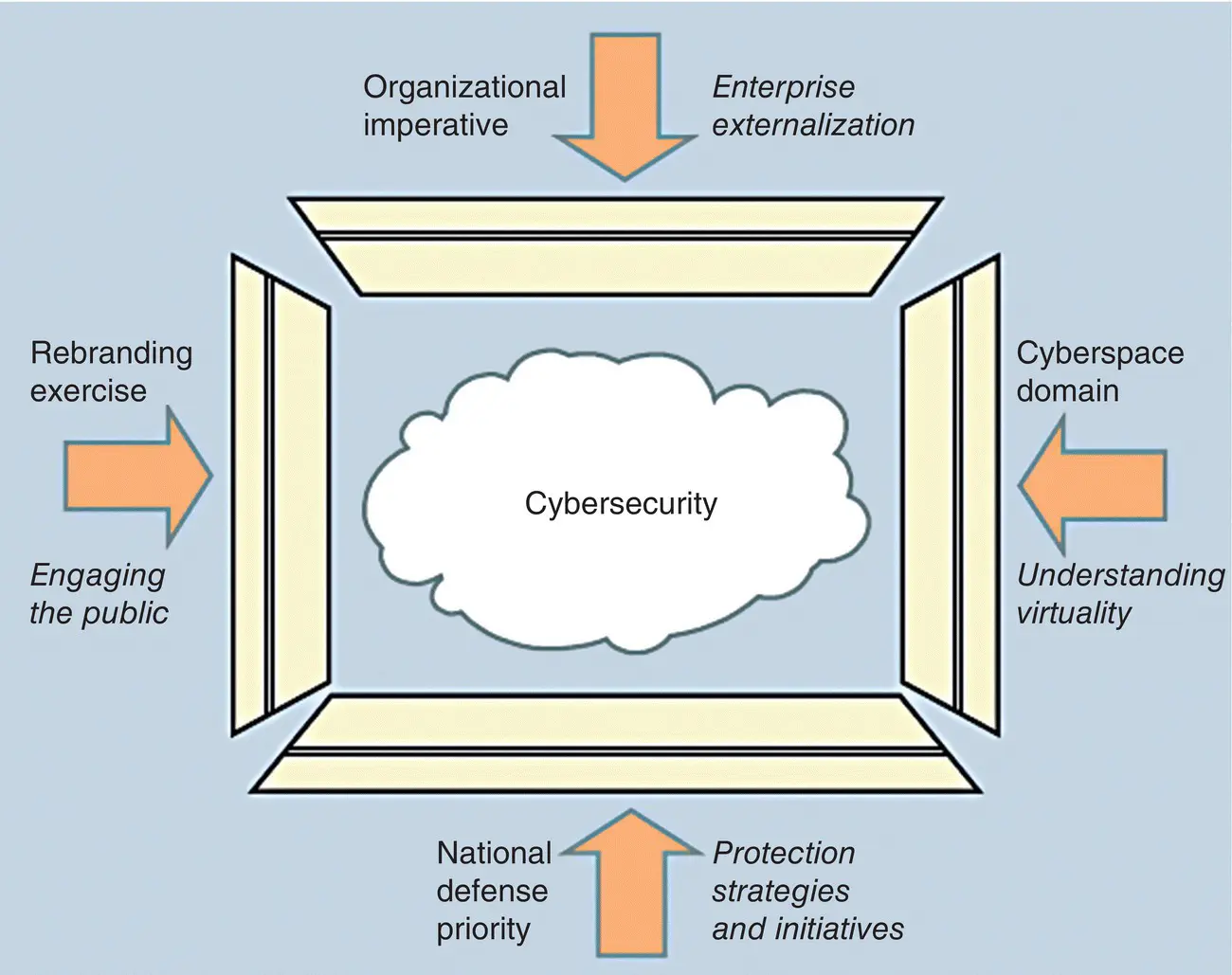
Figure 2.13 Forces shaping cybersecurity.
Source: [Agresti 2010]. © 2010, IEEE.
Energy sector users and organizations need to succeed in understanding these forces including disturbances created by emerging technologies and trends.
Examples of trends that impact Smart Grid cybersecurity include the following:
Mobile computing refers to workforce dependence on being mobile and pervasive computing that has generated several devices that assist with this mobility. Forrester Research referred to mobile computing as the empowered movement, since companies are empowering their employees with modern consumer‐oriented technologies to better serve their customers [Forrester 2010]. Due to the decreasing cost of computing and the ubiquity of smartphone usage, applications have been developed to be used in home automation to control or remotely monitor a thermostat for air conditioning or a switch for lights.
Future Internet and its services are driven by users' needs, and new technologies enable these services. Examples of future Internet services for Smart Grid include:Energy consumer demand and responseDistributed energy storage with guaranteesPersonalized energy consumer profileControl of consumer's appliances
Web as ubiquitous computer refers to the convergence of mobile smart devices, cloud computing, and software as a service, which enables Web with anytime and anywhere computing capabilities [Pendyala 2009]; the applications are moving from the local PC machine to the ubiquitous computer. One issue is that users cannot keep up with frequent software updates and configuring Wi‐Fi security settings.
Embedded systems surround us in many forms from cars to cell phones, video equipment to MP3 players, and dishwashers to home thermostats. However, security for these systems is an open and more difficult problem than security for desktop and enterprise computing. Even a washing machine can be used as a platform to launch distributed denial‐of‐service (DoS) attacks against the public, an organization, or the government.
Читать дальше













