Source: [Ling 2015]. © 2016, IEICE.
Figure 2.10is a simple representation of a CPS with the components, computation, communication, and control that interact with the cyber and physical world.
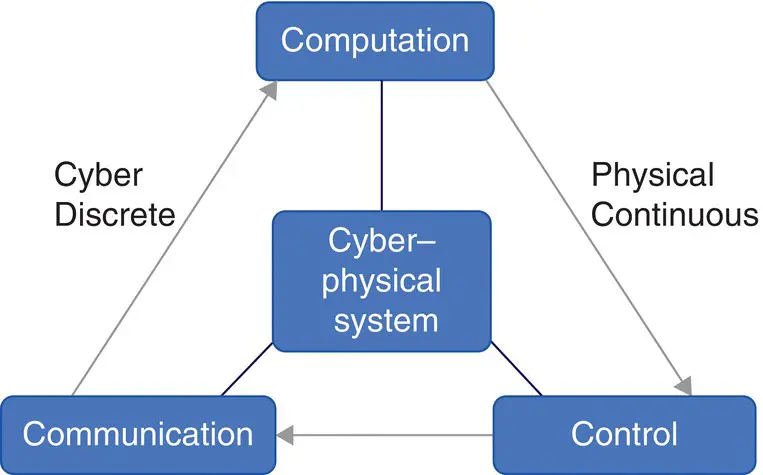
Figure 2.10 Cyber–physical system – simple structure.
Generally, the structure for a CPS includes physical plant, computational platforms, and the network fabric. An application may use two networked platforms with their own sensors and/or actuators. The embedded computers interact with a physical plant through sensors and actuators and with each other through a network fabric. The action taken by the actuators affects the data provided by the sensors through the physical plant.
As described in [Lee 2015b], the design of CPS, therefore, requires understanding the joint dynamics of computers, software, networks, and physical processes. The author argues that it is this study of joint dynamics that sets this CPS discipline apart. CPS is a discipline that combines engineering models and methods from mechanical, environmental, civil, electrical, biomedical, chemical, aeronautical, and industrial engineering with the models and methods of computer science. Therefore, there are theoretical and practical challenges in the design of CPS applications; among them security is an alarming concern that requires imperative investment.
The term cybersecurity is associated with the security of the cyberspace, which was coined in a science fiction novel [Gibson 1984], as a futuristic computer network that people use by plugging their minds into it or the electronic medium of computer networks, in which online communication takes place. However, there are many definitions for cybersecurity and cyberspace that evolved over time. Many cyber terms are coming into vogue, and a few organizations have tried to include significant definitions that allow us to make useful distinctions when compared with existing terms. Thus, when searching for definitions of certain security concepts and terms, we find identical definitions (one glossary references another glossary), similar definitions, or definitions that are too short or too long, or missing.
2.2.1 Cybersecurity Definitions
The following is a sequence of definitions for cybersecurity and cyberspace as provided in known glossaries.
Cybersecurityis the ability to protect or defend the use of cyberspace from cyber attacks [CNSSI 4009].
Cybersecurityis the ability to protect or defend the use of cyberspace from cyber attacks [NISTIR 7298r2].
Cybersecurityis the activity or process, ability or capability, or state whereby information and communication systems and the information contained therein are protected from and/or defended against damage, unauthorized use or modification, or exploitation [NICCS 2016].
Cyberspaceis a global domain within the information environment consisting of interdependent IT infrastructures, telecommunication networks and computer processing systems, and embedded processors and controllers [CNSSI 4009].
Cyberspaceis a global domain within the information environment consisting of interdependent IT infrastructures, telecommunication networks and computer processing systems, and embedded processors and controllers [NISTIR 7298r2].
Cyberspaceis the interdependent network of IT infrastructure that includes the Internet, telecommunication networks, computer systems, and embedded processors and controllers [NICCS 2016].
As shown above, we found identical definitions for both terms in these glossaries [CNSSI 4009], [NISTIR 7298r2] and a similar definition for cyberspace in the glossary [NICCS 2016]. While these terms are not defined in [ISO/IEC 27000], [RFC 4949]], the International Telecommunication Union approved the overview of cybersecurity as described in [ITU‐T 2008], which is not really a concise definition.
In common usage, the term cyberspace refers also to the virtual environment of information and interactions between people [WH 2009]. However, a new term, cyber ecosystem, is encompassing more entities. It is defined as the interconnected information infrastructure of interactions among persons, processes, data, and information and communication technologies, along with the environment and conditions that influence those interactions [NICCS 2016].
2.2.2 Understanding Cybersecurity Terms
Cybersecurity is the ability to protect or defend the use of cyberspace from cyber attacks [CNSSI 4009]. Further, a cybersecurity attack is defined as an attack via cyberspace for the purpose of disrupting, disabling, or destroying a computing environment/infrastructure [CNSSI 4009]. However, this definition excludes the possibility of physical attacks, unintentional human errors, and natural disasters that can also disrupt a computing environment/infrastructure. Physical attacks may be realized without using the cyberspace, but still causing harm to cyberspace. Often two definitions are combined into one definition. For example, the cybersecurity definition [CNSSI 4009] is concatenated with another definition (measures taken to protect a computer or computerized system [IT and OT] against unauthorized access or attack) to make the cybersecurity definition provided by the US Department of Energy (DOE) [DOE 2014a].
However, no unique definition for cybersecurity is available across the Internet [Franscella 2013]. As pointed out in [Vacca 2012], no formal accepted definition of cybersecurity currently exists. On the use of cybersecurity versus cyber security, the communities agreed on using the word cybersecurity [Franscella 2013].
Often the cybersecurity is covering all security dimensions from technology to economic and social, legal, law enforcement, human rights, national security, warfare, international stability, intelligence, and other aspects. The widespread use of this term often masks the broad and complex nature of the subject matter [OECD 2015].
When comparing cybersecurity with information security, some people regard these concepts as overlapping, being the same thing [ENISA 2015a]. Others may view information security as focused on protecting specific individual systems and the information within organizations, while cybersecurity is seen as being focused on protecting the infrastructure and networks of critical information infrastructures.
Information security is defined as measures adopted to prevent the unauthorized use, misuse, modification, or denial of use of knowledge, facts, data, or capabilities [Maiwald 2004]. This term is defined in [NISTIR 7298r2] as the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability. Although this definition may seem more focused (implying security goals such as confidentiality, integrity, and availability), it is still not accurate because protection measures should also provide for non‐repudiation and other attributes of the information.
Although there is no universally accepted nor straightforward definition of cybersecurity or information security [ENISA 2015a], we need to understand the differences among these various definitions and views.
The recommendations of the [OECD 2015] document introduce the concept of digital security risk (see definition in Appendix A) that requires a response fundamentally different in nature from other categories of risk needs to be countered. To that effect, the term cybersecurity and more generally the prefix cyber that helped convey this misleading sense of specificity do not appear in the recommendation. Digital security risk is dynamic in nature. It includes aspects related to the digital and physical environments, the people involved in the activity, and the organizational processes supporting it.
Читать дальше













