Another concern regarding IoT technologies pertains to the environmental impacts of the manufacture, use, and eventual disposal of all these semiconductor‐rich devices. Modern electronics are replete with a wide variety of heavy metals and rare earth metals, as well as highly toxic synthetic chemicals. This makes them extremely difficult to recycle properly. Electronic components are often simply incinerated or dumped in regular landfills, thereby polluting soil, groundwater, surface water, and air.
However, the next evolutionary stage of the IoT is touted by the IoE technology.
2.1.2 Internet of Everything (IoE)
The Internet of Everything is a technology concept that sees previously unconnected objects and processes converging with the ones that are digital first by their nature. This all‐encompassing convergence of physical and digital domains is set to disrupt individual organizations and entire industries like nothing before [ABI Research 2015b]. ABI Research defines the IoE market as a combination of the IoT, Internet of Digital, and Internet of Humans. Value at stake drives in the connection of everything.
Figure 2.3represents an infographic of IoE components and subcomponents as perceived by the markets a few years ago. According to [ABI Research 2015b], the market is expected to grow more than 40 billion devices on the IoE by 2020.
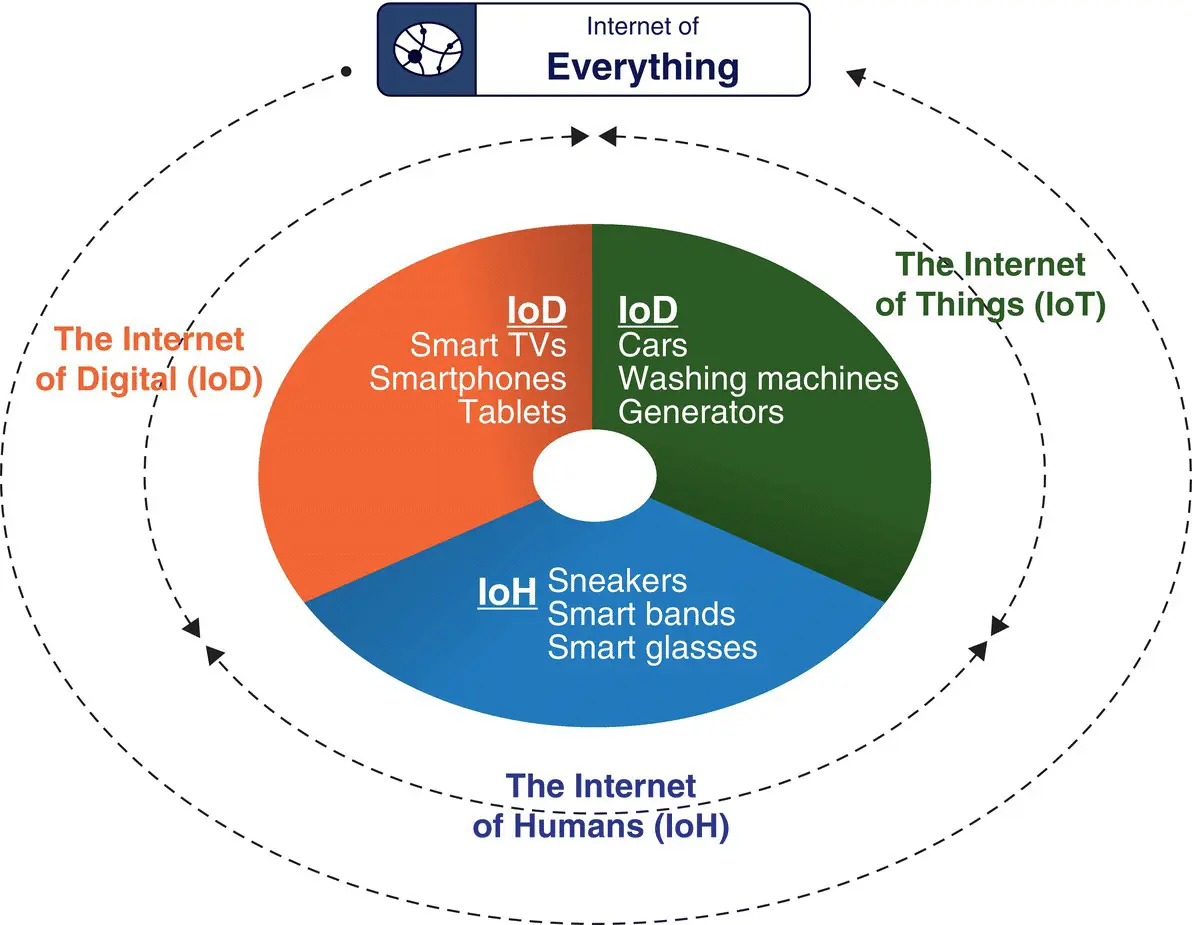
Figure 2.3 Infographic of Internet of Everything.
Source : [ABI Research 2015a]. Printed based on courtesy of ABI Research Internet of Everything Market.
According to ABI Research market tracker of 2019 for IoE, the forecast for 2023 is that IoT will represent 54% of IoE, a higher percentage than Internet of Digital evaluated at 43%.
Figure 2.4shows a chart representing the ABI Research market forecast of IoE for 2023 year, where:
Internet of Digital includes PCs and digital home and mobile devices.
Internet of Humans includes wearable computing.
IoT includes utilities and industrial IoT, smart cities and buildings, retail advertising and supply chain, connected car, and smart home.
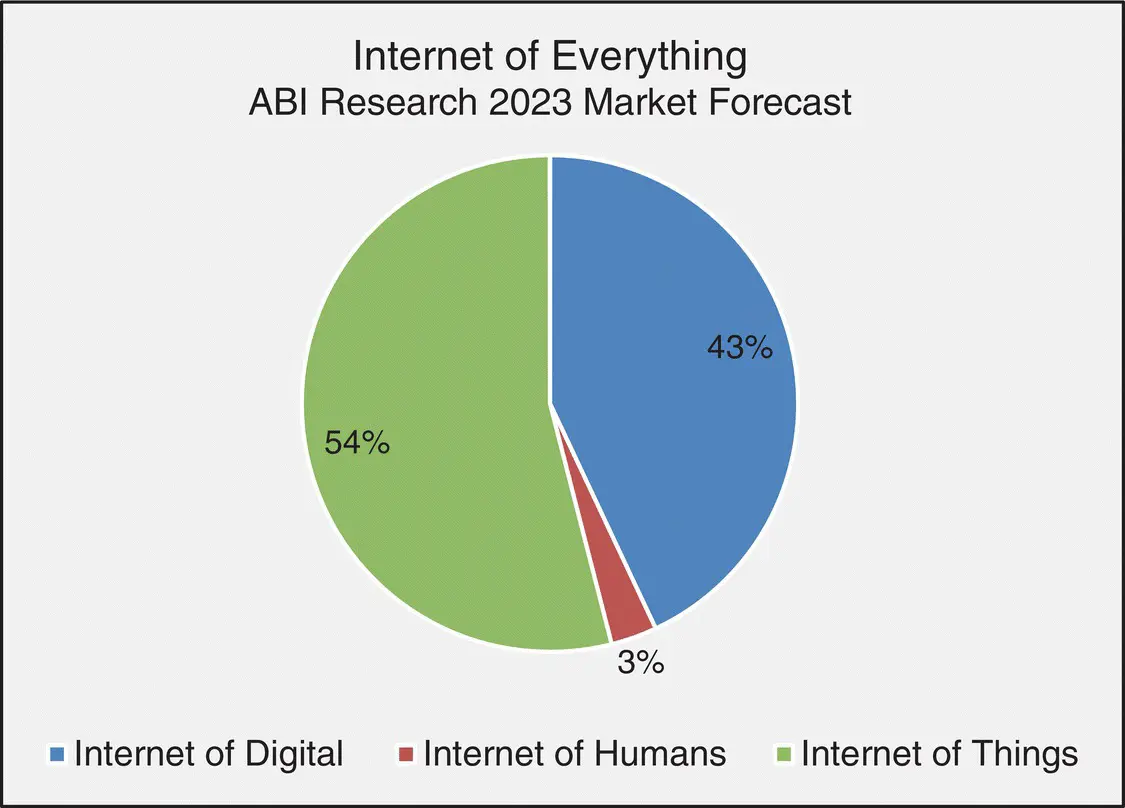
Figure 2.4 ABI Research Market Forecast for Internet of Everything.
Source: Based on courtesy of ABI Research Internet of Everything Market Tracker, 2019.
Figure 2.5shows the overall concept of IoE, a networked connection of people, processes, data, and things. Examples of things include devices, cars, generators, and washing machines. In the context of IoE, cybersecurity is moving away from the traditional centralized view to a decentralized approach whereby security happens as close as possible to the endpoint. Specifically, in IoE, identity must extend beyond conventional identity. However, creating a unified identity that addresses users in both physical world and virtual world is still a challenge.
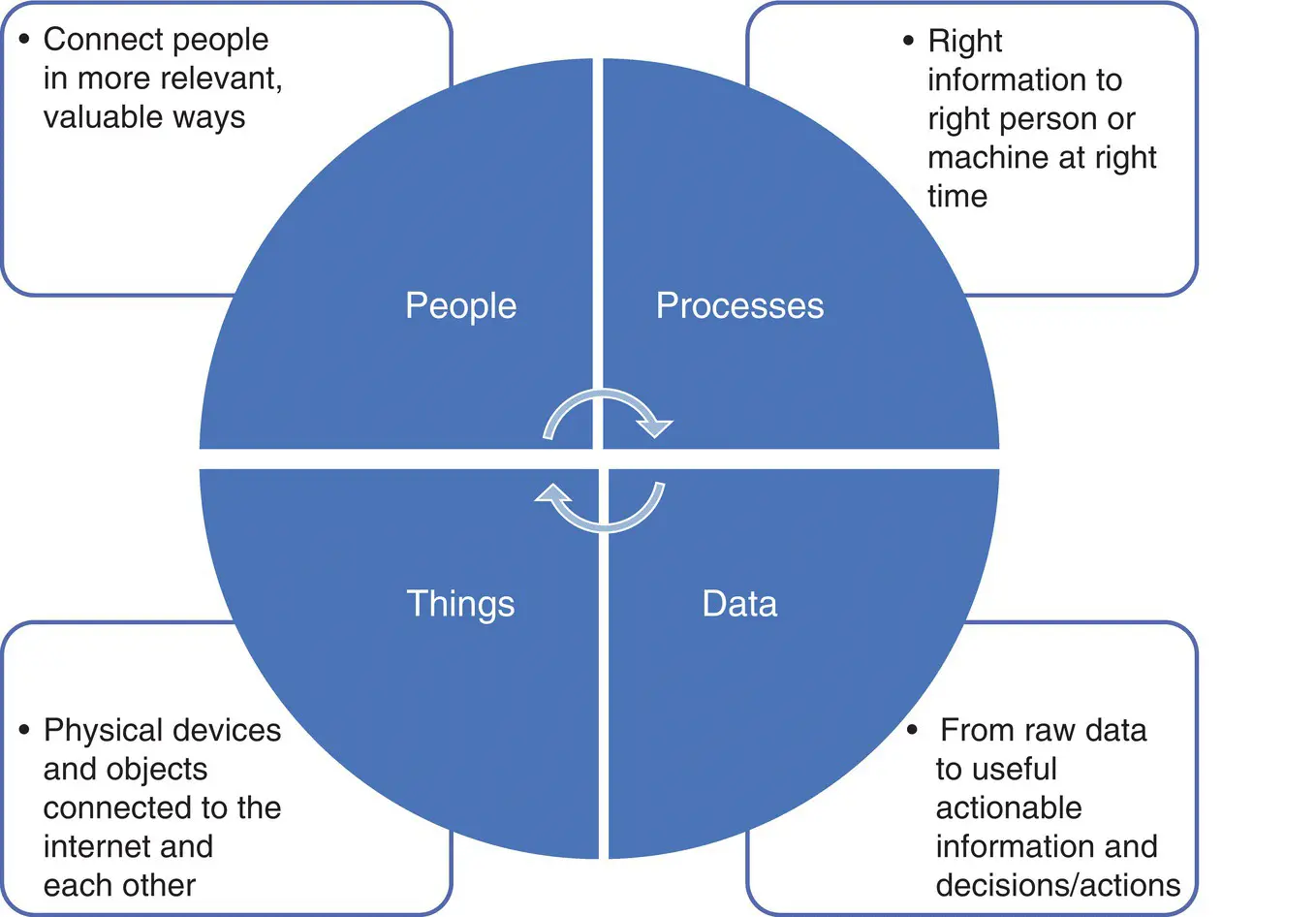
Figure 2.5 Internet of Everything connected in a large distributed network.
On one hand, the IoE is being enabled by advancements with standardized, ultra‐low‐power wireless technologies (see Figure 2.6). The likes of Bluetooth and ZigBee have proven instrumental in driving sensor and node implementations, while Wi‐Fi technology and cellular connectivity serve as a backbone for transferring the collected data to the cloud.
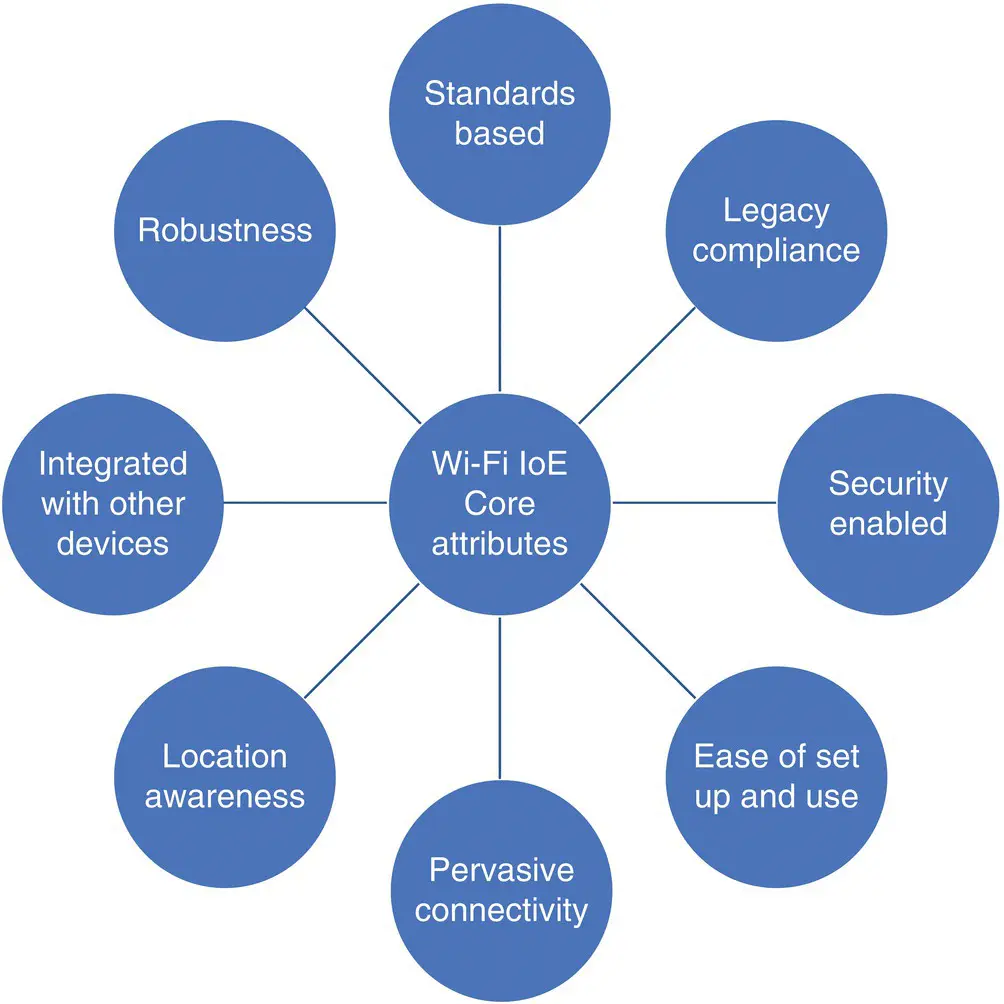
Figure 2.6 A perspective of the Wi‐Fi Internet of Everything – core attributes.
Consumers in particular expect to integrate all connected devices on a single home network – specifically on Wi‐Fi networks. They may embrace a range of connected applications such as home security, smart energy, and in‐vehicle infotainment. Wi‐Fi enables human interaction with the IoE [Wi‐Fi 2014].
An enormous range of device manufacturers, service providers, and software makers stand to build entirely new businesses addressing the IoE opportunity. However, this opportunity brings more security and privacy concerns for the consumers and businesses that support various applications.
Networked embedded systems have emerged under various names such as Internet/Web of Things/Objects, Internet of Everything, smart objects, Cooperating Objects, Industry 4.0, the Industrial Internet, cyber–physical systems, M2M, the Internet of Everything, the Smarter Planet, TSensors (Trillion Sensors), or the Fog (like the cloud, but closer to the ground). The vision is of a technology that deeply connects our physical world with our information world, although one may argue on the differences and their focus. In this research paper [Karnouskos 2011], the author argues that does not really differentiate when it refers to them as an amalgamation of computational and physical properties.
However, the trend is toward integration and interaction of the physical world with the information world. Recently, the community has come to understand that the principal challenges in embedded systems stem from their interaction with physical processes, and not from their limited resources. Since CPS emerge as a distinct category, the following section is an overview of this concept.
2.1.3 Cyber–Physical Systems
The term cyber–physical systems was coined by Helen Gill at the National Science Foundation in the United States in 2006 [CPS 2006]. CPS comprise interacting digital, analog, physical, and human components engineered for function through integrated physics and logic [NIST CPS].
A CPS is an integration of computation with physical processes whose behavior is defined by both cyber and physical parts of the system [Lee 2015a]. The authors argue that it is not sufficient only to separately understand the physical components and the computational components, but we must also understand their interaction. CPS is about the intersection, not the union, of the physical and the cyber [Lee 2010], [Lee 2015a], [Lee 2015b]. The embedded computers and networks monitor and control the physical processes, usually with feedback loops where physical processes affect computations and vice versa. This work [Lee 2015a] provides methodology and techniques for designing CPS. Figure 2.7is a simple representation of a CPS with the components, computation, communication, and control that interact continuously.
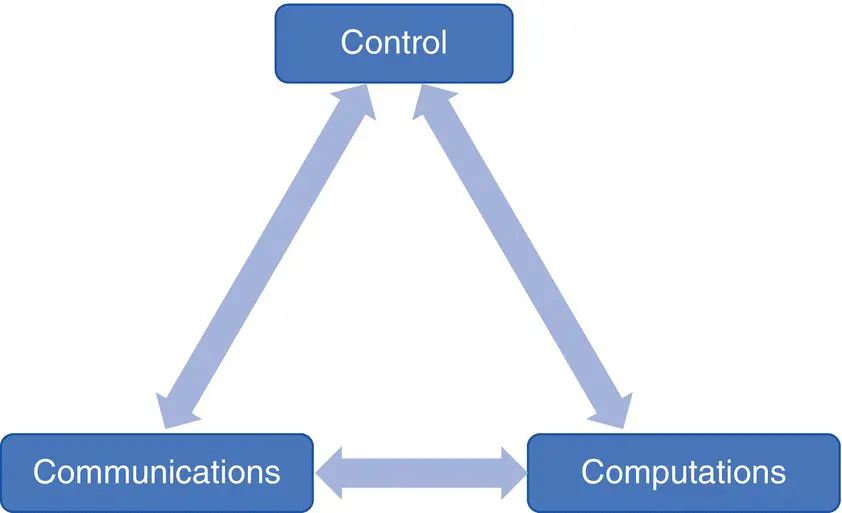
Figure 2.7 Simple cyber‐physical representation.
CPS are heterogeneous blends by nature. They combine computation, communication, and physical dynamics [Lee 2015a]. The authors envision that several CPS applications may be based on a structure to include three main parts:
First, the physical plant is the physical part of a CPS, not realized with computers or digital networks; it can include mechanical parts, biological or chemical processes and human operators.
Second, there are one or more computational platforms, which consist of sensors, actuators, one or more computers, and (possibly) one or more operating systems (OS).
Читать дальше

















