Third, there is a network fabric, which provides the mechanisms for the computers to communicate; the platforms and the network fabric form the cyber part of the CPS.
A more detailed and current definition of CPS is provided by NIST [NIST SP1500‐201]:
Cyber–physical systems integrate computation, communication, sensing, and actuation with physical systems to fulfill time‐sensitive functions with varying degrees of interaction with the environment, including human interaction.
A CPS conceptual model is shown in Figure 2.8. This CPS representation highlights the potential interactions of devices and systems in a system of systems (SoS) (e.g. a CPS infrastructure).
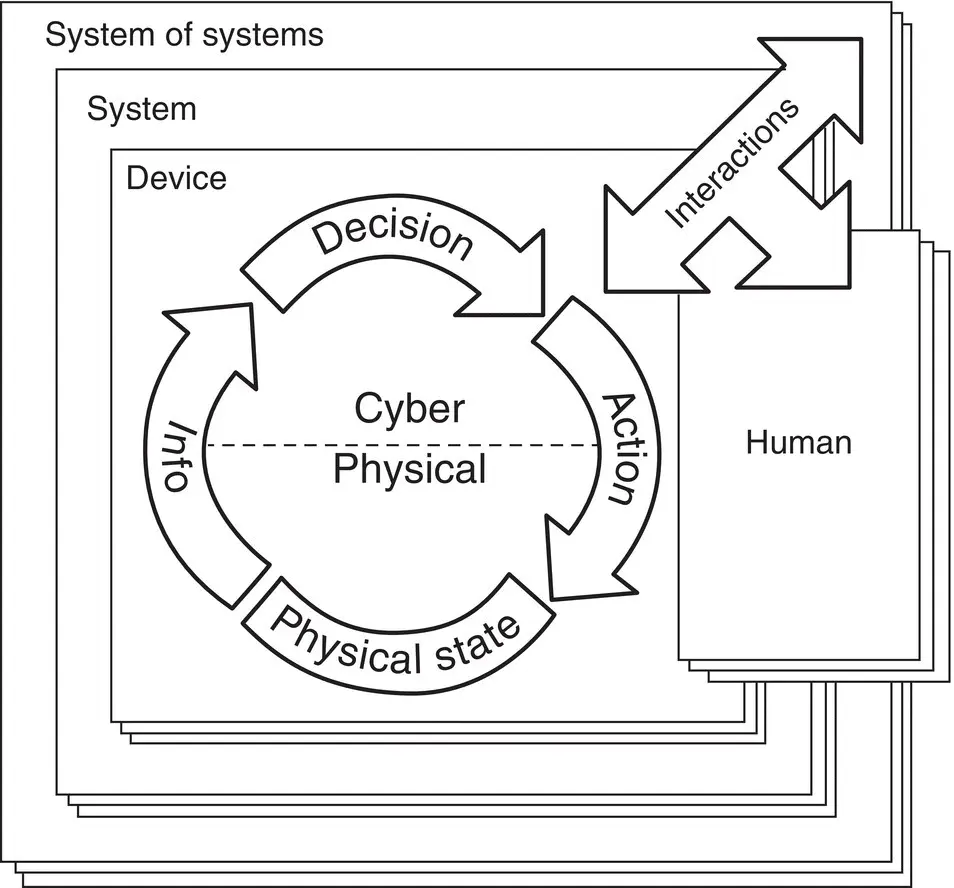
Figure 2.8 NIST CPS conceptual model.
Source: [NIST SP1500‐201]. Public Domain.
As shown in Figure 2.8, CPS may be as simple as an individual device (a device that has an element of computation and interacts with the physical world through sensing and actuation), or a CPS can consist of one or more cyber–physical devices that form a system or can be an SoS, consisting of multiple systems that consist of multiple devices. This pattern is recursive and depends on one's perspective (e.g. a device from one perspective may be a system from another perspective). Ultimately, a CPS must contain the decision flow together with at least one of the flows for information or action. The information flow represents digitally the measurement of the physical state of the physical world, while the action flow impacts the physical state of the physical world. This allows for collaborations from small and medium scale up to city/nation/world scale.
The scope of CPS is very broad by nature; there are large number and variety of domains, services, applications, and devices. Also, CPS controls have a variety of levels of complexity ranging from automatic to autonomic. CPS go beyond conventional product, system, and application design traditionally conducted in the absence of significant or pervasive interconnectedness. There are many differences that characterize CPS from traditional systems. Examples of characteristics are listed in Table 2.1.
Table 2.1 CPS characteristics.
Source: Adapted from [NIST SP1500‐201].
| Characteristic |
Description |
Remarks |
| Cyber and physical |
Combination of cyber and physical components |
|
| Connectedness |
Generally involves sensing, computation and actuation |
Involves combination of IT and OT with associated timing constraints |
| System of systems (SoS) |
May bridge multiple purposes and time and data domains |
Different time domains may reference different time scales or have different granularities or accuracies Time scale: a system of unambiguous ordering of events |
| Emergent behaviors |
Open nature of CPS composition |
Understanding a behavior that cannot be reduced to a single CPS subsystem, but comes about through the interaction of possibly many CPS subsystems |
| Methodology |
A methodology needed to ensuring interoperability, managing evolution, and dealing with emergent effects |
Example: NIST 1500‐201 framework |
| Repurposed |
Other purpose use beyond applications that were their basis of design |
|
| Application enabler |
Enabling cross‐domain applications |
|
| Trustworthiness concern |
Potential impact on the physical world |
Urgent need for emphasis on security, privacy, safety, reliability, resilience, and assurance for pervasive interconnected devices and infrastructures |
| Broad range of platform and algorithm complexity |
Accommodate a variety of computational models |
|
| Variety of modes of communication |
From stand‐alone systems to highly networked systems |
May use legacy protocols or anything up to more object exchange protocols |
| Heterogeneity |
Wide range of heterogeneous devices (sensors, controllers, control schemes, input sources, platforms, etc.) |
Complexity associated with the sensing and control loop(s) with feedback that are central to CPS must be well addressed in any design |
| Co‐design |
Design of the hardware and the software jointly to inform tradeoffs between the cyber and physical components of the system |
|
| Typically a time‐sensitive component |
Timing is a central architectural concern |
A bound may be required on a time interval, e.g. the latency between when a sensor measurement event occurred and the time at which the data was made available to the CPS |
| Interaction with the operating environment |
CPS measure and sense and then calculate and act upon their environment, typically changing one or more of the observed properties (thus providing closed‐loop control) |
|
| Typically a human environment |
CPS environment typically includes humans and humans function |
Architecture must support a variety of modes of human interaction: human as CPS controller or partner in control; human as CPS user; human as the consumer of CPS output; and human as the direct object of CPS to be measured and acted upon |
The CPS will provide the foundation of our critical infrastructure, form the basis of emerging and future smart services, and improve our quality of life in many areas [NIST CPS].
2.1.4 Cyber–Physical Systems Applications
The vision is that CPS could improve many existing systems, such as robotic manufacturing systems; electric power generation and distribution; process control in chemical factories; distributed computer games; transportation of manufactured goods; heating, cooling, and lighting in buildings; people movers such as elevators; and bridges that monitor their own state of health. The impact of such improvements on safety, energy consumption, and the economy is potentially enormous. So modern businesses rely on CPS to accurately sync the real‐world status on backend systems and processes.
CPS can be found extensively in multiple domains including the electricity sector [Parolini 2012]. CPS is seen as an integral part of the Smart Grid as discussed by Karnouskos in [Karnouskos 2011], [Karnouskos 2012]. The perspective of this researcher is that the Smart Grid will have to heavily depend on CPS that are able to monitor, share, and manage information and actions on the business as well as the physical power grid. Many traditional parts of the Smart Grid are increasingly CPS dominated. In generation, CPS control the connection to the network as well as the operational aspects in the electricity generation side such as solar and wind parks, hydro facilities, etc.
CPS involve traditional IT as in the passage of data from sensors to the processing of those data in computation. CPS also involve traditional operational technology (OT) for control aspects and actuation. The combination of these IT and OT worlds along with associated timing constraints is a particularly new feature of CPS.
Figure 2.9depicts the use of CPS for smart transportation [Ling 2015]. The components of the CPS are a collection of computing devices communicating with one another and interacting with the physical world via sensors and actuators in a feedback loop as described in [Lee 2015a].
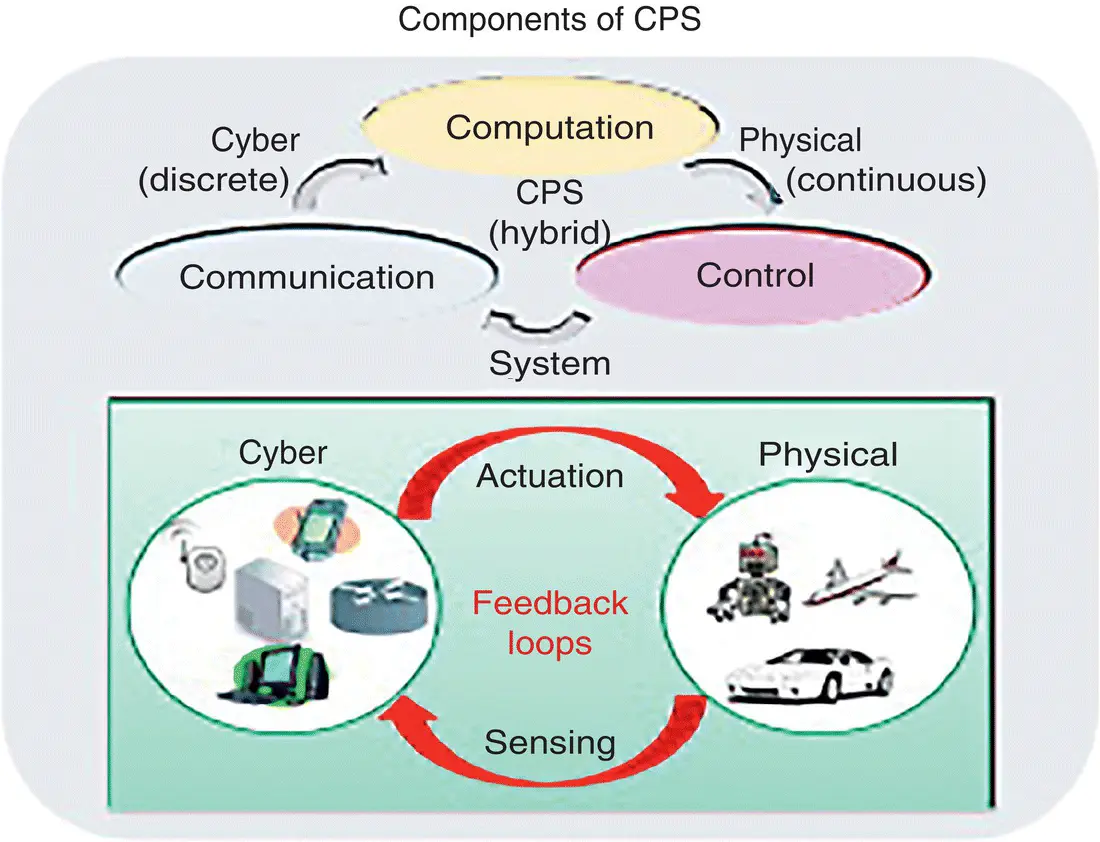
Figure 2.9 Components of CPS for smart transportation.
Читать дальше














