The interconnected objects have main characteristics [Roman 2011]:
Existence – Things exist in the physical world with the aid of specific technologies, such as an embedded communication device becoming a virtual persona.
Sense of self – Things have, either implicitly or explicitly, an identity that describes them and can process information, make decisions, and behave autonomously.
Connectivity – Things can initiate communication with other entities and an element in their surroundings; a remote entity can locate and access them.
Interactivity – Things can interoperate and collaborate with a wide range of heterogeneous entities, whether human or machine or real or virtual such that they produce and consume a wide variety of services.
Dynamicity – Things can interact with other things at any time, any place, and in any way; they can enter and leave the network at will, no need to be limited to a single physical location, and can use a range of interface types.
An optional sixth characteristic is environmental awareness. Sensors can enable a thing to perceive physical and virtual data about its environment, such as water radiation or network overhead (this characteristic is optional because not all things will exhibit it, such as an object enhanced with a lower‐end radio‐frequency identification (RFID) tag).
The vision of the IoT has evolved due to a convergence of multiple technologies, ranging from wireless communication to the Internet and from embedded systems to microelectromechanical systems (MEMS). This means that the traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), and others all have made contributions to the development of IoT technology (see technology roadmap; Figure 2.1).
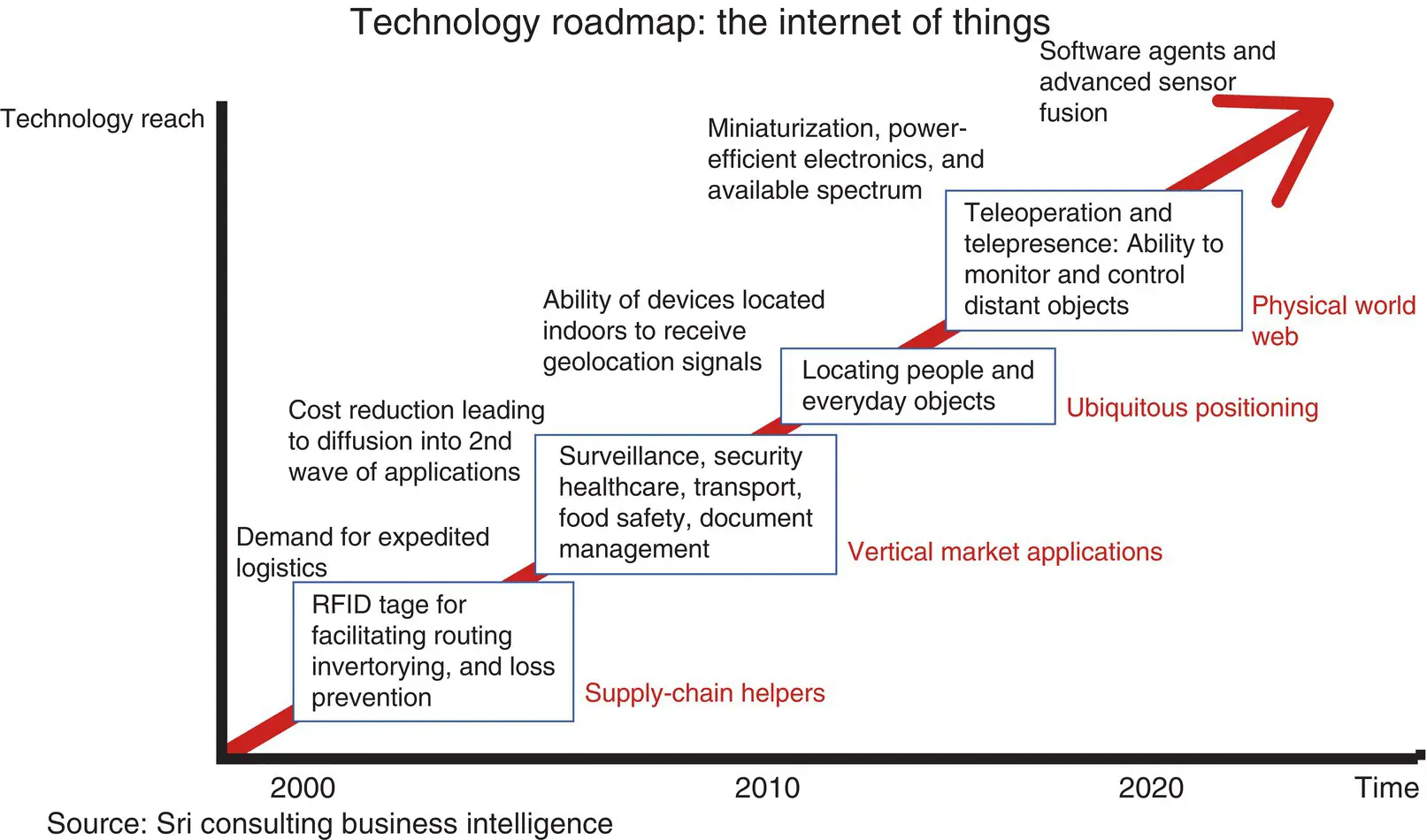
Figure 2.1 Technology road map.
Source: [WikiTech]. Public Domain.
Energy‐efficient microcontrollers act as brains due to objects with embedded intelligence. A sensor is a special device that perceives certain characteristics of the real world and transfers them into a digital representation.
Sensor technology provides objects with sensory receptors, and RFID provides a way for them to distinguish one another, much as people recognize a face. Finally, low‐energy wireless technology, such as specified in the IEEE 802.15.4 standard, supplies the virtual counterparts of voice and hearing. Multiple applications already use these and other technologies, such as machine‐to‐machine (M2M) communication, virtual worlds, and robotics.
The IoT is a vision that encompasses and surmounts several technologies at the confluence of nanotechnology, biotechnology, information technology (IT), and cognitive sciences [Santucci 2010]. However, to be a virtual being, an IoT object needs only enough technology to realize its role and complete its mission.
The combination of various technologies has enabled objects to exhibit these characteristics, allowing them to become virtual beings. IoT technology mixes with social aspects, big data, and cloud computing and as an enabler for CPS. As a result of these technologies and the cross integration of all the technologies, a new level of control and feedback mechanisms is being developed in order to enhance the processes.
IoT technology is expected to offer advanced connectivity of devices, systems, and services that goes beyond M2M communications and covers a variety of protocols, domains, and applications.
By 2025, Internet nodes may reside in everyday things – food packages, furniture, paper documents, and more [SRI BI 2008]. The emergence of various applications includes building and industrial automation and cars that can interconnect millions of objects for sensing things like power quality, tire pressure, and temperature and that can actuate engines and lights. This trend quickly made it of the utmost importance to extend the IP protocol suite for these networks [Borman 2010].
It is predicted that there will be between 20 billion of IoT‐connected devices [Gartner 2015]. The IoT is expected to grow to 50 billion connected devices in 2020 [Cisco 2011] and to provide valuable information to consumers, manufacturers, and utility providers. IoT is one of the platforms of today's Smart Grid, smart city, and smart energy management systems.
The most common and relevant IoT applications to Smart Grid and DER systems include energy management, distribution automation, building and home automation, and infrastructure management.
2.1.1.3.1 Energy Management
Integration of sensing and actuation systems, connected to the Internet, is likely to optimize energy consumption as a whole. It is expected that IoT devices will be integrated into all forms of energy‐consuming devices (switches, power outlets, bulbs, televisions, etc.) and be able to communicate with the utility supply company in order to effectively balance power generation and supply.
IoT technologies offer consumers, manufacturers, and utility providers new ways to manage devices and ultimately conserve resources and save money by using smart meters, home gateways, smart plugs, and connected appliances.
The introduction of electric smart plugs, in‐home displays, and smart thermostats has given consumers a choice of which household devices they want to monitor. Additionally, the IoT delivers more data for manufacturers and utility providers to reduce costs through diagnostics and neighborhood‐wide meter reading capabilities [Monnier 2013].
Besides home‐based energy management, the IoT is especially relevant to the Smart Grid since it provides systems to gather and act on energy and power‐related information in an automated fashion with the goal to improve the efficiency, reliability, economics, and sustainability of the production and distribution of electricity.
Another application is a city energy consumption service to monitor the energy consumption of the whole city [Zanella 2014]. This service enables authorities and citizens to get a clear and detailed view of the amount of energy required by different services (public lighting, transportation, traffic lights, control cameras, heating/cooling of public buildings, etc.). This service helps identify the main energy consumption sources and to set priorities in order to optimize their consumption behavior.
2.1.1.3.2 Distribution Automation
The Smart Grid provides systems to gather and act on energy and power‐related information in an automated fashion with the goal of improving the efficiency, reliability, economics, and sustainability of the production and distribution of electricity. Using advanced metering infrastructure (AMI) devices connected to the Internet backbone, electric utilities can not only collect data from end‐user connections but also manage other distribution automation devices like transformers and reclosers. Figure 2.2shows an application involving a smart meter with capabilities as an intranet of things and a smart meter as part of the IoT.
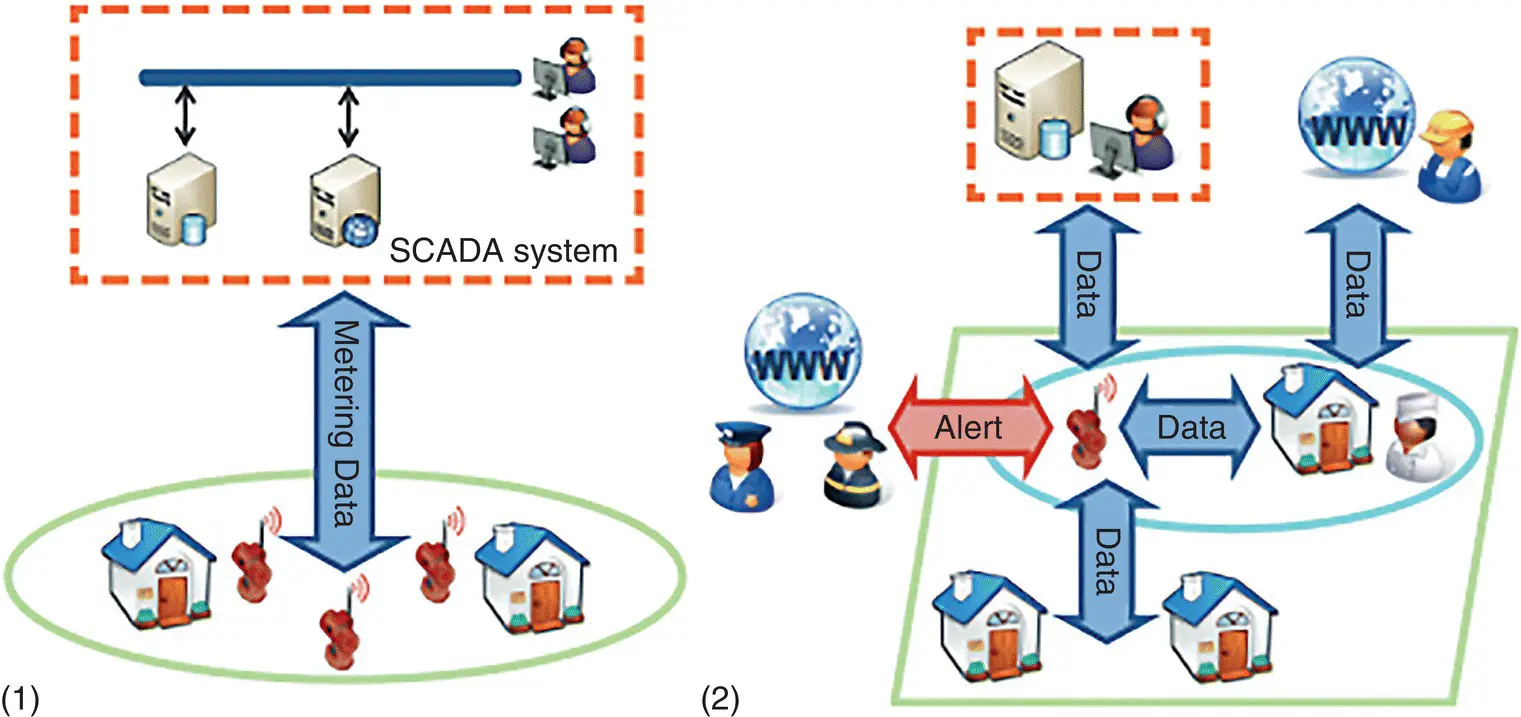
Figure 2.2 A smart meter application in two scenarios.
Source: [Roman 2011]. © 2011, IEEE.
In the intranet‐of‐things scenario (left), the meter interacts only with SCADA system. In the IoT scenario (right), the meter interacts with the SCADA system, household members, other houses, and emergency personnel.
Читать дальше














