There is a growing concern about the security and safety of the control systems in terms of vulnerabilities, lack of protection, and awareness.
Besides security concerns, computer systems including control systems raise the issue of safety causing harm and catastrophic damage when they fail to support applications as intended. Therefore, information security management principles, processes, and security architecture need to be applied to smart power grid systems without exception [ENISA 2015a].
Smart Grid technologies and applications create new security and privacy risks and concerns in unexpected ways. Concerns of privacy of consumers and people are of vital importance in the energy sector. If there is any compromise of the personal data or security of the power service, it can undermine many services and applications. An incident would not only create a breach of privacy or confidentiality, integrity, or availability of the information, but it might also compromise the potential future markets the technology might have been able to create if it the service had been secure. Therefore, the vulnerability of the power system is not mainly a matter of electric system or physical system, but it is also a matter of cybersecurity. Attacks (such as attacks upon the power system, attacks by the power system, and attacks through the power system) to the Smart Grid applications could bring huge damage to the economy and public safety.
In complex interactive systems like Smart Grid whose elements are tightly coupled, the likelihood of targeted attack as well as failures from erroneous operations and natural disasters and accidents is quite high. Vulnerabilities and attacks can be at different levels – software controlling or controlled device, application, storage, data access, LAN, enterprise, private communication links, and public PSTN and Internet‐based communications.
The destruction of power grid systems and assets would have a debilitating impact on energy security, economic security, public health, or safety. With a system that handles power generation, transmission, and distribution, security responsibility extends beyond the traditional walls of the data center. An intruder can, intentionally or unintentionally, cause a power line to be energized that would endanger lives. Similarly, a power line may be de‐energized in such a way as to cause damage to transmission and control systems and possibly endanger the safety of employees and the public. Therefore, each organization should develop its own policy to protect assets, employees, and general public who are at risk when human (intentional or unintentional) threats or natural disasters occur.
Security controls (called also safeguards, measures, or countermeasures) are needed to ensure protection of an organization assets (tangible and intangible) and people as well as safety of people. Tangible assets are physical assets that include power equipment, computers, devices, facilities, and supplies. Intangible assets include data, information, reputation, intellectual property, copyrights, trade secrets, business strategies, and any other information valuable to any organization.
It is recognized that as new capabilities are included in the Smart Grid, potential privacy issues may occur [NISTIR 7628]. A privacy policy framework for the Smart Grid and for smart homes is suggested in [GridWise 2011]. This framework is limited and addresses only consumer privacy issues that arise from the collection, use, and retention of such data no matter from what source it is collected.
1.5 Computing and Information Systems for Business and Industrial Applications
Business firms and other organizations rely on information systems to carry out and manage their operations, interact with their customers and suppliers, and compete in the marketplace. An information system is composed of many components that include hardware, software, data, people, procedures, and networks necessary to use information as a resource in an organization [Whitman 2011]. An information system is an organized assembly of computing and communication resources and procedures – e.g. equipment and services, together with their supporting infrastructure, facilities, and personnel – that create, collect, record, process, store, transport, retrieve, display, disseminate, control, or dispose information to accomplish a specified set of functions [RFC 4949].
An information system aims to support operations, management, and decision making. In a broad sense, the term is used to refer not only to the ICT that an organization uses but also to the way in which people interact with this technology in support of business processes. At the center of any computing or information system is data and information.
1.5.1 Information System Classification
Figure 1.17shows different types of information systems. Distinct types of information systems include the following [O’Brien 2011]:
Management information systems are used to analyze and facilitate strategic and operational activities. They utilize systems to generate information to improve efficiency and effectiveness of decision making, providing critical information tailored to the information needs of executives (e.g. decision support).
Operations support information systems refer to the interconnected databases and applications implemented for the ongoing central maintenance of electronic operational data. Operations information system process data generated by business operations, maintain records about the exchanges, handle routine (yet critical) tasks, monitor, and control industrial processes.
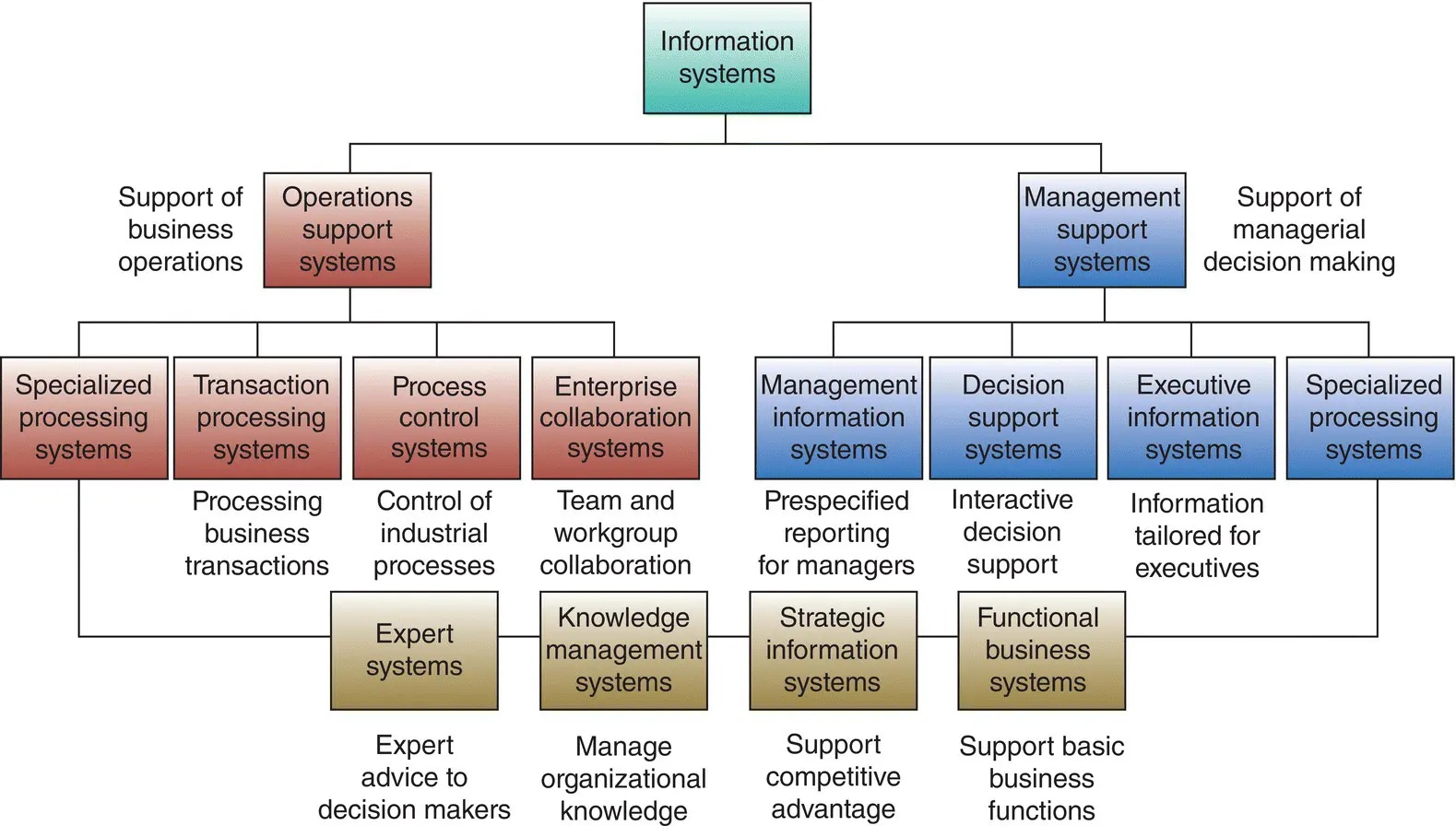
Figure 1.17 Information systems classification.
Source: [O’Brien 1999]. © 1999, McGraw‐Hill.
As depicted in this diagram, both categories Operations support and Management Support Systems categories include specialized processing systems such expert systems (expert advice to decision makers), knowledge management systems (manage organizational knowledge), strategic information systems (support competitive advantage), and functional business systems (support business functions).
Also, information systems include specialized systems such as industrial/process control systems, telephone switching and private branch exchange (PBX) systems, and environmental control systems [CNSSI 4009].
Process control systems, SCADA systems, distributed control systems (DCS), and other smaller control system configurations including skid‐mounted programmable logic controllers (PLC )are often found in the industrial sectors and critical infrastructures. These are also known under a general term, industrial control system (ICS) [NIST SP800‐82r2]. SCADA systems and DCS monitor the flow of electricity from generators through transmission and distribution lines. These electronic systems enable efficient operation and management of electric systems through the use of automated data collection and equipment control. A related term is industrial control network, which is a system of interconnected equipment used to monitor and control physical equipment in industrial environments [Galloway 2012].
Industrial control system is a generalized term referring to a system of electronic components that control the physical operations of machines. Automated or operator‐entered commands can be issued to machines, either locally in‐plant or remote station control devices, often referred to as field devices. The machines may transmit sensor data back to the controller for monitoring and automated operational functions. ICS sare typically used to operate the infrastructure in industries such as electrical, water, oil and gas, discrete manufacturing, and chemical including experimental and research facilities such as nuclear fusion laboratories. The reliable operation of modern infrastructures including Smart Grid depends on computerized systems and SCADA systems.
Читать дальше













