Most microgrids operating today are single‐customer microgrids and focus on integrating traditional generation resources (e.g. CHP and diesel generators) with new technologies such as renewable generation and electric energy storage systems. Customized communication and control technologies were developed to enable these resources to act as a single entity with respect to the grid.
Figure 1.14shows the concept of a nested microgrid with a naming convention according to their configuration that is used to differentiate them. Microgrids can exist in multiple configurations: independently, networked along a feeder, or nested within another. Microgrids help with:
Reliability by serving as a grid resource in grid‐connected mode and switching to island mode on detecting a contingency, thus improving reliability metrics
Energy security by ensuring critical loads can be served for sustained periods of time during catastrophic events such as hurricanes or attacks
Environment by operating in a manner to maximize electricity produced from renewable resources to reduce overall emissions
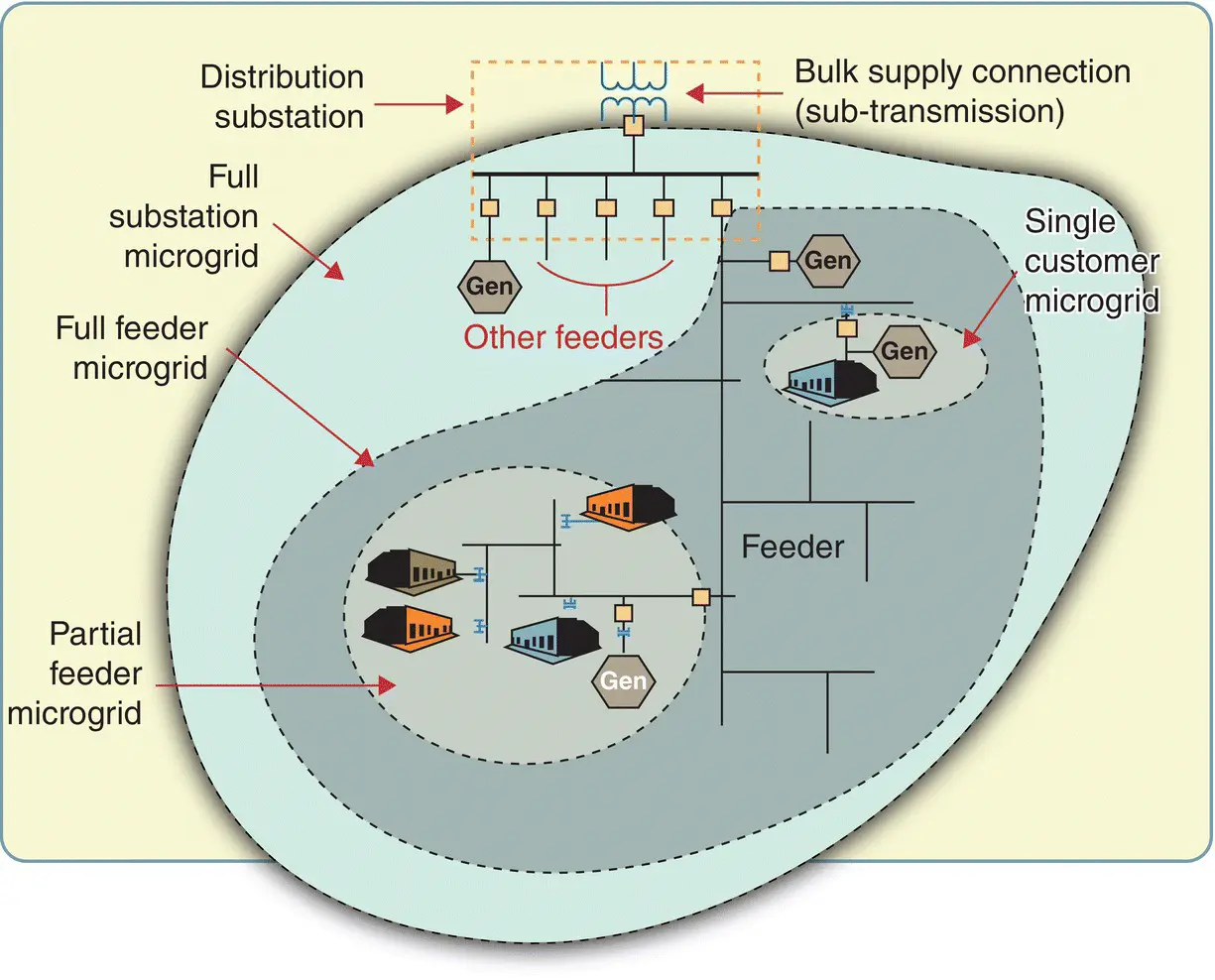
Figure 1.14 Alternative microgrid configurations.
Source: [DOE 2015b]. Public Domain.
1.3.5 Virtual Power Plant
A VPP is an operating concept where a group of DERs that are geographically disperse (e.g. associated with different utility meters, residing on different feeders, or not having clearly defined electrical boundaries) is aggregated and coordinated to act as a single entity (see Figure 1.15). This technology concept can include any combination of individual grid‐enabled customer resources (e.g. DG, EVs, and energy storage) or integrated resources (e.g. smart buildings and microgrids). Additionally, the control of the aggregated resources is accomplished through a mix of strategies and signals that can involve markets [Zurborg 2010].

Figure 1.15 VPP schematic view.
Source: [OECD 2012b]. © 2012, OECD.
The main components of a VPP are interconnected control and management devices as well as an integrated software management system. A software platform, such as a distributed energy resource management system (DERMS), can be used to implement the VPP concept [Saadeh 2015].
The concept of connected VPP is shown in Figure 1.16. An integrated and interoperable DRMS with various utility DMSs makes it possible to use VPP for purposes such as:
Optimize distribution system conditions
Aggregate various DR to provide services to the bulk transmission system
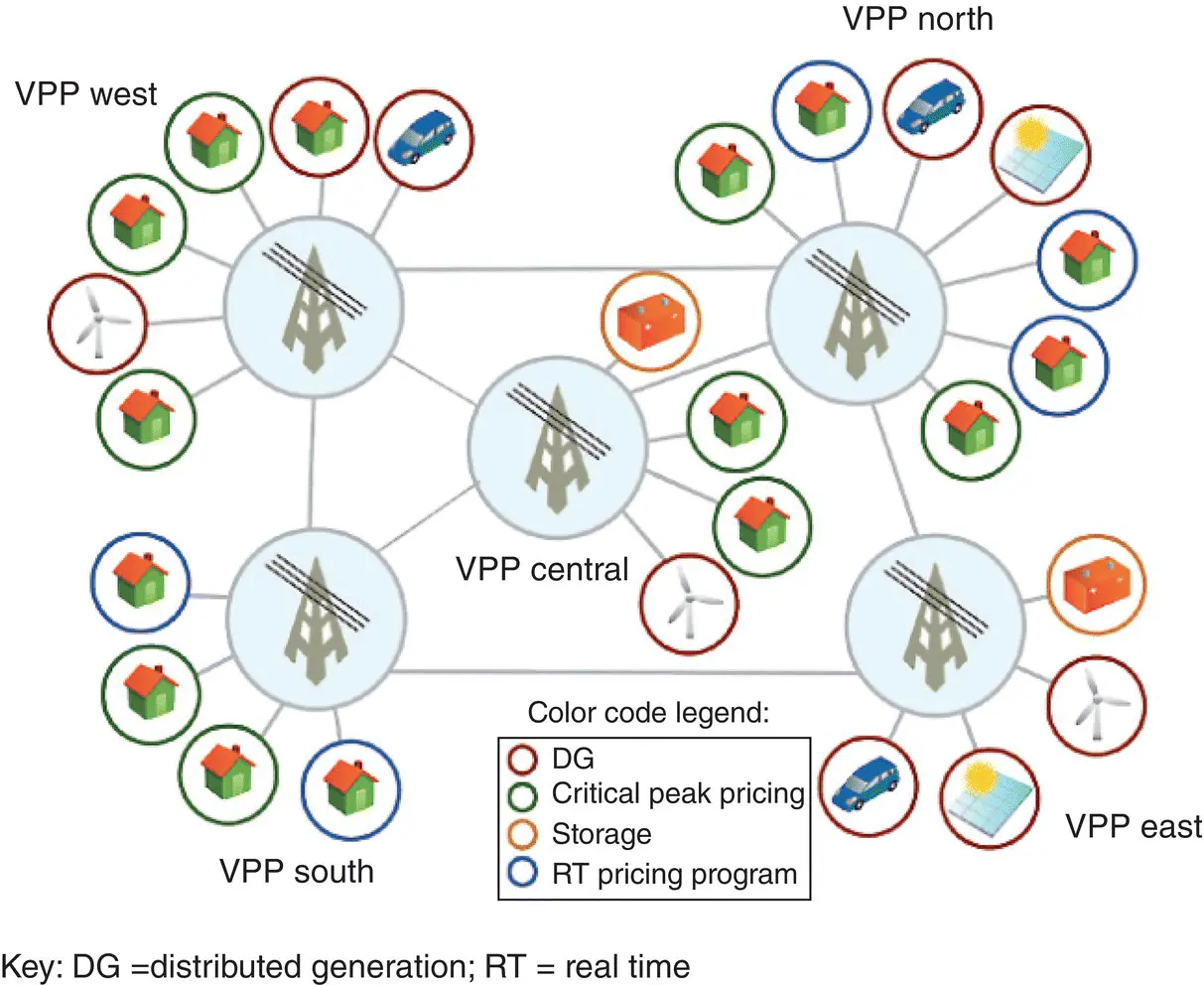
Figure 1.16 Illustration of connected virtual power plants.
Source: [DOE 2015b]. Public Domain.
Advances in communication, modeling, and controls are needed to use this technology more broadly.
Examples of information systems for Smart Grid and DER systems are further discussed in the book.
1.4 Scope of Security and Privacy
Defining the scope of security in the context of IT is not a trivial task because security is complex. Security is defined as the policies, practices, and technology that must be in place for an organization to use information for supporting business activities with a reasonable assurance of safety [Volonino 2004]. There are numerous corporate assets to protect. The protection involves managerial policies, technologies, and legal and ethical issues.
Therefore, in the context of this book, security has a wide base and addresses specific issues regarding Smart Grids, DERs, power grids, network communications, computers, technologies, information, organizations, critical infrastructures, and people.
Security relates to several areas such as physical security, information security, operation security, communication security, national security, network security, disaster recovery, laws and ethics, management, etc. These areas are interrelated and they affect each other. All technology, hardware, people, and procedures are woven together into a security fabric [Harris 2005]. In fact, the so‐called information society is increasingly dependent on a wide range of software systems whose mission is critical, such as telecommunications, control systems, financial systems, and power systems. The potential losses that are faced by businesses and organizations that rely on all these systems, both hardware and software, therefore signify that it is crucial for information systems to be properly secured from the outset.
Security is a condition of the system being protected from unintended or unauthorized access, change, or destruction [IIC 2015]. Therefore, a product, system, or service is considered to be secure to the extent that its users can rely on its functions (or will function) in the intended way [ENISA Glossary].
1.4.1 Security for the Smart Grid
Often security has different meanings to different people (e.g. security professional, control engineer, management). There are several definitions and terms that sometimes make the security an ambiguous field. With the Smart Grid one can associate also the word security, which is one of few Smart Grid terms that is overworked and overloaded (e.g. assigned multiple definitions). Such definitions range all the way from ensuring reliability, keeping the lights on, to protecting the confidentiality of customer information [Nordell 2012]. There are many facets of security that one needs to understand such as security as reliability, security as communication reliability, and security as information protection.
1.4.1.1 Security as Reliability
Security as reliability is one aspect that is used by power engineers to describe power system reliability as the ability of the bulk power system to withstand unexpected disturbances such as short circuits or unanticipated loss of system elements due to natural causes [Nordell 2012]. Traditional power engineering practice views reliability as security.
Electric system reliability is the degree to which the performance of the elements of the electrical system results in power being delivered to consumers within accepted standards and in the amount desired. Reliability in this context encompasses two concepts, adequacy and security:
Adequacy implies that there are sufficient generation and transmission resources installed and available to meet projected electrical demand plus reserves for contingencies.
Security implies that the system will remain intact operationally (e.g. will have sufficient available operating capacity) even after outages or other equipment failure. The degree of reliability may be measured by the frequency, duration, and magnitude of adverse effects on consumer service.
Among reasons for developing an interconnected electric utility system is also the improvement in the reliability of services to customers when individual generating plant reliability was (and still is) much less than 100%. Currently, the security focus of the industry has expanded to include withstanding disturbances caused by man‐made physical or cyber attacks.
1.4.1.2 Security as Communication Reliability
Security as communication reliability is used to describe the reliability for power system communication, which has several facets, including the probability that a given message will be lost entirely, the use of redundant communication paths and automatic failover to protect against message loss, the expected time delay (latency) in delivering a message, and the expected variability of that time delay (jitter) [Nordell 2012]. It also involves how competing messages may (or may not) be given priority when communication channels are saturated. This latter parameter is known as quality of service (QoS) and has long been practiced in the world of telephony, but it is a relatively new concept for power system engineers.
Читать дальше















