1.7.1 Industrial Control Systems
A control system is a device or set of devices to manage, command, direct, or regulate the behavior of other devices or systems. ICSs are typically used to operate the infrastructure in industries such as electrical, water, oil and gas, and chemical including experimental and research facilities such as nuclear fusion laboratories. SCADA systems, DCS, and other smaller control system configurations including skid‐mounted PLC are often found in the industrial sectors and critical infrastructures. These are also known under a general term, ICS. The reliable operation of modern infrastructures depends on computerized systems and SCADA systems.
In the past, control systems were isolated from other IT systems. Connection to the Internet is new (early 1990s) and debatable among specialists. Many experts agree that exposing control systems to the public PSTN and Internet carries unacceptable risk. However, even without any connection to the Internet, these systems are still vulnerable to external or internal attackers that can exploit vulnerabilities in private communication network and protocol, software such as operating systems, custom and vendor software, data storage software, databases, and applications.
Control systems are exposed to the same cyberspace threats like any business system because they share the common vulnerabilities with the traditional IT systems. In complex interactive systems like Smart Grid whose elements are tightly coupled, likelihood of targeted attack as well as failures from erroneous operations and natural disasters and accidents is quite high. Vulnerabilities and attacks could be at different levels – software controlling or controlled device, application, storage, data access, LAN, enterprise, private communication links, and public PSTN and Internet‐based communications.
SCADA system is a common process automation system that is used to gather data from sensors and instruments located at remote sites and to transmit data at a central site for either control or monitoring purposes. The collected data is usually viewed on one or more SCADA host computers located at the central or master site. Based on information received from remote stations, automated or operator‐driven supervisory commands can be pushed to remote station control devices, which are often referred to as field devices. Generally, a SCADA system includes the following components:
Instruments that sense process variables.
Operating equipment connected to instruments.
Local processors that collect data and communicate with the site’s instruments and operating equipment called PLC, remote terminal unit (RTU), intelligent electronic device (IED), or programmable automation controller (PAC).
Short‐range communications between local processors, instruments, and operating equipment.
Host computers as central point of human monitoring and control of the processes, storing databases, and display of statistical control charts and reports. Host computers are also known as master terminal unit (MTU), the SCADA server, or a PC with human–machine interface (HMI).
Long‐range communications between local processors and host computers using wired and/or wireless network connections.
Figure 1.22shows a typical SCADA system with HMI installed in a control center and connected via communication network to monitored field sites.
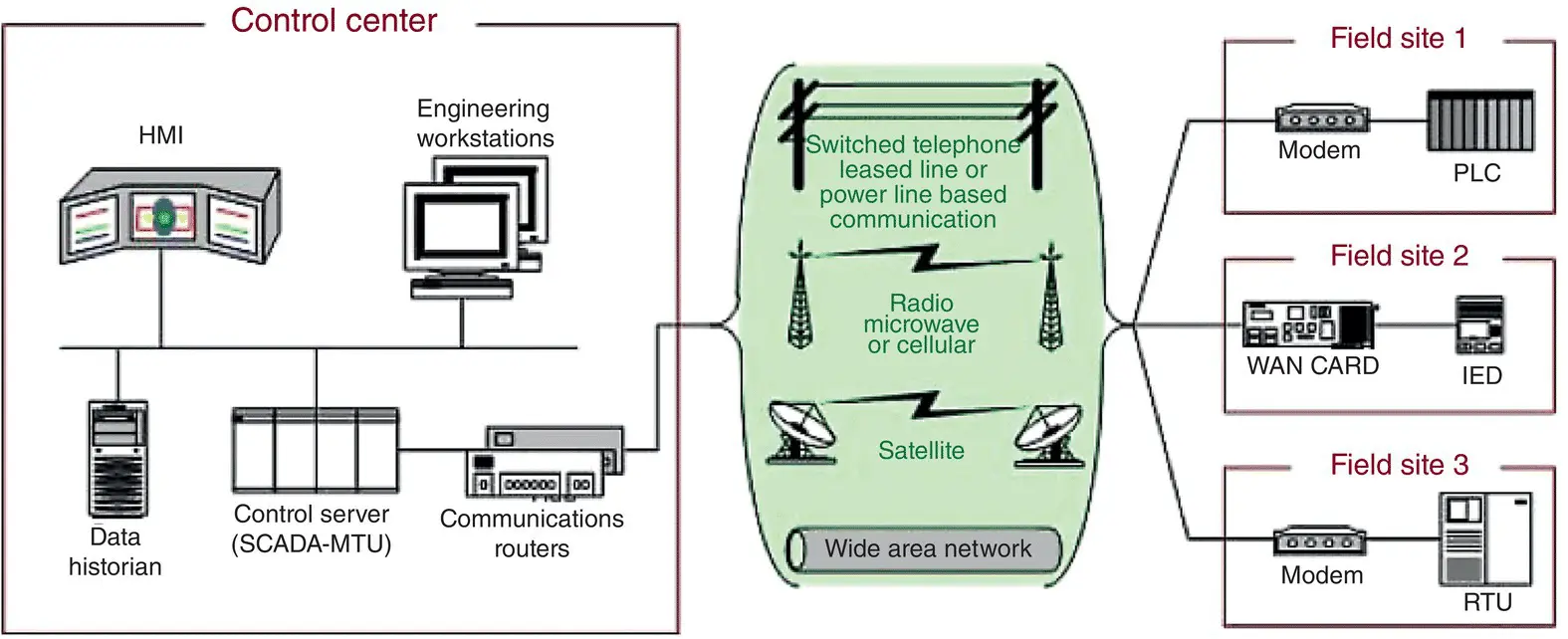
Figure 1.22 SCADA general diagram.
Source: [NIST SP800‐82r2].
Public Domain.
SCADA system is a category of control systems used to monitor or control processes such as chemical, transport, water supply, power generation and distribution, and gas and oil supply. A control system is a device or set of devices to manage, command, direct, or regulate the behavior of other devices or systems. However, SCADA is not a full control system, but rather focuses on the supervisory level. Usually, SCADA systems involve a human‐in‐the‐loop control and decision‐making processes.
The architecture of a SCADA system consists of one of more MTUs that are used by engineers in a control station to monitor and control a large number of RTUs located in field or industrial plants. An MTU is a general‐purpose computer or server running SCADA utility programs and RTUs are generally small dedicated devices designed for rough field or industrial environment. One or more SCADA MTUs retrieve real‐time analog and status data from RTUs, store to data historian, and analyze the data. MTUs automatically send control commands to the RTUs or enable the engineers to do so manually.
Vulnerability discovery techniques and appropriate engineering activities are required to ensure security, reliability, and safety of plants that use SCADA control systems.
These systems evolved from static to dynamic systems. The increased connectivity to Internet and mobile device technology has also a major impact on control system architectures. Modern products are often based on component architectures using commercial off‐the‐shelf (COTS) product elements as units. Security and safety of the SCADA control systems in terms of vulnerabilities, lack of protection, and awareness are discussed in [Hentea 2007]. Information security management principles and processes need to be applied to SCADA systems without exception.
1.7.3 Energy Management Systems
Although not unique definition is used for EMS, one definition is more common:
Computer systems used by operators of electric to monitor, control, and optimize the performance of the power grid (generation, transmission, distribution).
The functionality of any EMS is supported by a combination of two systems:
SCADA system for monitoring and control.
Advanced applications for optimization.
Energy management may be supported by distributed energy management technologies that include energy storage devices and various methods for reducing overall electrical load.
The technology references as SCADA/EMS or EMS/SCADA are common. In [Weiss 2010], EMS is described as a SCADA system with additional applications.
EMS may exclude the monitoring and control functions, more specifically referring to a suite of power applications. In other circumstances, EMS refers to a system of hardware and software components for an automated control and monitoring of the heating, ventilation, and lighting needs of a building or group of buildings such as university campuses, office buildings, or factories [Panke 2002]. Most of these EMS also provide facilities for the reading of electricity, gas, and water meters. The data obtained from these EMS systems can then be used to produce trend analysis and annual consumption forecasts.
The increasing number of SCADA/EMS systems operating in the electric industry, the growing number of market participants, and the development of complex market models relying more on IT technologies contribute to raising the interdependency between the operation of the power grid and the operation of the wholesale electric market.
1.7.4 Advanced Meter Systems
The AMI enable measurement of detailed, time‐based information and frequent collection and transmittal of such information to various parties. Advanced metering systems are composed of hardware, software, communications, consumer energy displays and controllers, and applications (such as customer‐associated systems, meter data management, and supplier business systems).
AMI typically refers to the full measurement and collection system that includes meters at the customer site; communication networks between the customer and a service provider, such as an electric, gas, or water utility; and data reception and management systems that make the information available to the service provider [EPRI 2007], [UCAIUG 2008].
Читать дальше













