Electric transportation refers, primarily, to enabling large‐scale integration of PEVs to increase use of renewable sources of energy.
Database management systems and the communication‐associated networks that create a two‐way network between advanced meters and utility business systems, enabling collection and distribution of information to customers and other parties, such as the competitive retail supplier or the utility itself; customers may be consumers and producers of energy (owners of renewable and storage systems).
The following are examples of DER information systems that can be included in the category of management information systems:
DR and consumer energy efficiency encompasses mechanisms and incentives for utilities, business, industrial, and residential customers to cut energy use during times of peak demand or when power reliability is at risk; DR is necessary for optimizing the balance of power supply and demand.
Information security management system supports the approach to developing, implementing, and improving the effectiveness of an organization’s information security with regard to the management of risk.
Other categories of information systems may include:
End‐user computing systems to support the direct hands on use of computers by end users for operational and managerial applications.
Business information systems to support the operational and managerial applications of the basic business functions of the organization, for example, integrated systems in Smart Grid.
Strategic information systems to support the operational and managerial applications of the basic business functions of the organization.
1.6 Integrated Systems in a Smart Grid
OT represents a broad category of applications that utilities use for operations that include safe and reliable generation and delivery of energy. OT includes power equipment (e.g. operating gear, oil circuit breakers, solid‐state relays, and many devices in between) and control room applications such as SCADA systems that monitor the network, reaching out to devices as complex as substation gateways or to devices as simple as sensors. OT is often applied within a mission critical framework.
If OT is more focused in operations, IT systems are just the opposite. IT systems allow machines to exchange information directly with humans, usually within a second or longer. Examples include improved enterprise resource planning (ERP), geographic information systems (GIS), and customer relationship management (CRM) systems, along with office‐based productivity tools and mobile computing devices, which have now permeated the utility workplace. Until recently, the growth in IT stood independent of the hidden OT equipment, serving and protecting the grid. The interconnection of a wide array of traditional and emerging utility business and operation information systems such as EMS, DMS, SCADA, market management system (MMS), AMI, Customer Information System (CIS), and outage management system (OMS) allows the utilities, customers, and other service providers not only to monitor energy usage and grid status with higher precision and accuracy but also to analyze and activate distributed energy resources and storage options and construct pricing responses to appropriately reorient consumption patterns to balance available power generation capacity and demand continuously – all in real time. These activities require secure automated information exchange, analysis, and intelligent decision making distributed throughout the grid.
Therefore, the picture is starting to change. The Smart Grid is transforming utility operations and pushing IT across its traditional boundary into OT so rapidly that is blurring the distinction between the two categories (see Figure 1.21). The dynamics of IT and OT integration and how utilities can leverage this convergence for smarter, more cost‐effective, and more reliable operation are discussed in [Meyers 2013].
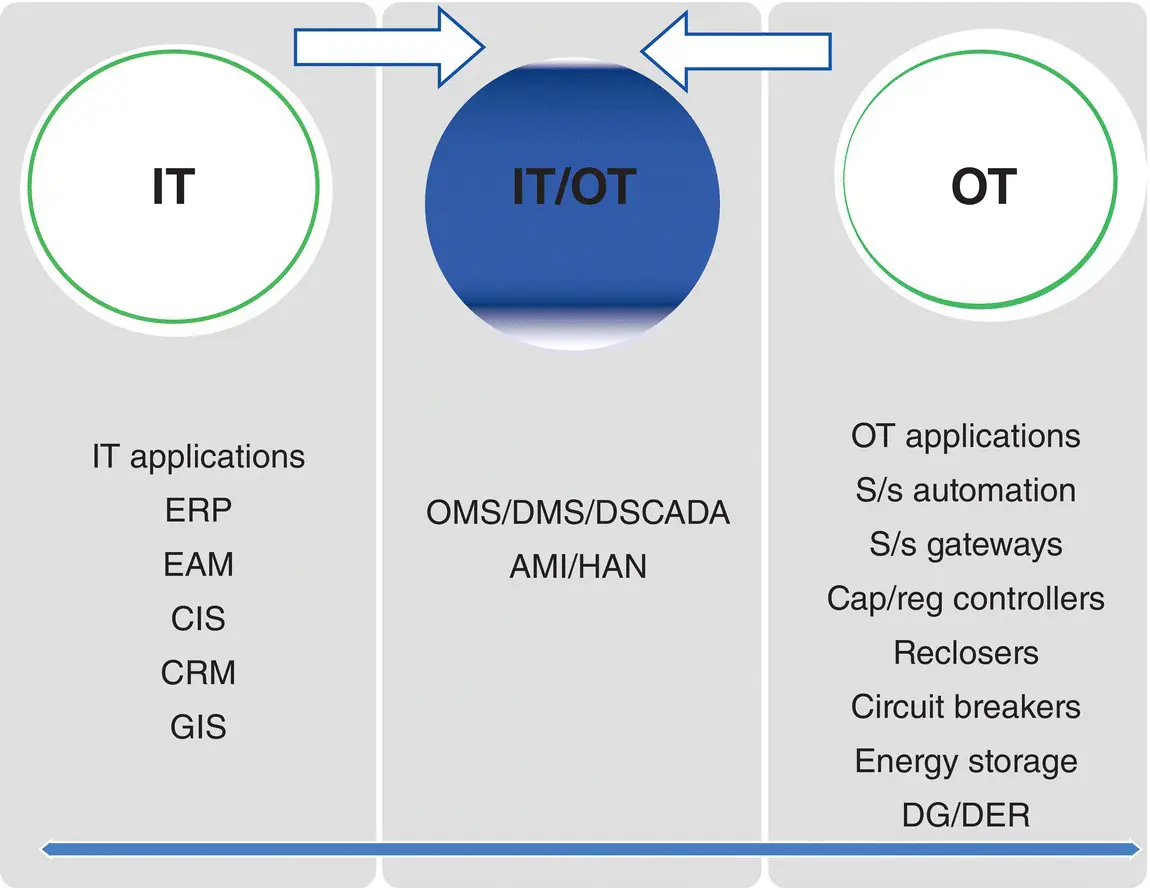
Figure 1.21 OT and IT integration. ERP, Enterprise Resources Planning; EAM, Enterprise Asset Management; GIS, Geographic Information Systems; CRM, Customer Relationship Management; CIS, Customer Information Systems; OMS, Outage Management System; DMS, Distribution Management Systems; DG, Distributed Generation; DER, Distributed Energy Resource; HAN, Home Area Network; AMI, Advanced Metering Infrastructure; DSCADA, Distribution Supervisory Control And Data Acquisition (DSCADA)
Smart meters and home area network technologies are also helping to blur the lines between the energy supply and energy distribution domains. For example, the OMS at many sites has migrated away from the enterprise and toward the operation domain.
The Smart Grid is redefining technology norms, and the modernization is characterized by the following trends:
The continuous growth in OT deployment.
The continuous implementation of IT by the utility to model, monitor, and manage its distribution system.
An urgent requirement for utilities to integrate their IT and OT networks.
However, the extensive digital technologies that enable significant improvements to new energy systems also increase the attack surface for cyber intrusion. For power system and supply security reasons, DER systems have to include ancillary services that are commonly seen on traditional power systems or bulk generation systems, so as to ensure compatibility with older and legacy devices and systems.
The characteristics of the future grid are distinctly different from those of the current power system as shown in Table 1.4. As shown in this table, there are more challenges including security that have to be addressed by Smart Grid systems.
Table 1.4 Comparison of key attributes of current and future systems.
Source: [DOE 2015b]. Public Domain.
| Current system |
Future paradigm |
| Monolitic |
Modular and agile |
| Centralized generation |
Centralized and distributed generation |
| Decisions driven by cost |
Decisions driven by cost and sustainability |
| Vulnerable to catastrophic events |
Contained events |
| Limited energy choices |
Personalized energy options |
| Vulnerable to new threats |
Inherently secure against threats |
The extensive digital technologies that enable significant improvements to new energy systems also increase the attack surface for cyber intrusion. The increasingly significant role of information systems and growing dependence on managing the power flow (generation, transmission, and distribution), markets, customers, financial, and trade needs call for special efforts to foster confidence in computing systems and information systems for business and industrial applications. Since the emergence of Internet and World Wide Web technologies, the control systems were integrated with the business and IT systems and became more exposed to cyber threats. Although specific threats target control systems and intelligent devices, these systems are also exposed to the same cyberspace threats as any business system because they share the common vulnerabilities with the traditional IT systems.
1.7 Critical Smart Grid Systems
The availability and reliability of computing and information systems for business and power grid applications are dependent on the secure operations of ICSs and other infrastructures. The following sections include a brief introduction of key systems and security concerns. Any attack on any of these systems can propagate on other systems too.
Читать дальше













