For a simple example, let 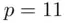 ,
, 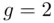 ,
, 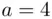 and
and 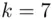 . Then
. Then 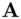 has the private key
has the private key  and the public key
and the public key 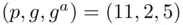 since
since 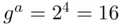 and
and 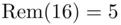 . Let the hash of the message
. Let the hash of the message 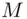 be
be 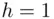 .
. 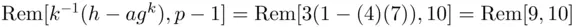 . Then
. Then 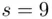 . Thus,
. Thus, 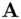 's signature is
's signature is 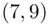 . Condition 2 is then satisfied for this signature.
. Condition 2 is then satisfied for this signature.
3.8 Intruder‐in‐the‐Middle Attack on the Diffie–Hellman (or Elliptic Curve) Key‐Exchange
We concentrate on the Diffie–Hellman key‐exchange. The Elliptic Curve key‐exchange discussed in Chapter 6is very similar, the main difference being that it uses a different group.
Basically, the intruder Eve impersonates Bto Aand Ato B. We use the notation of Section 3.7. Eve chooses an exponent 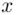 , and intercepts both
, and intercepts both 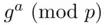 from Ato Band
from Ato Band 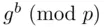 from Bto A. The procedures is as follows:
from Bto A. The procedures is as follows:
1 Eve intercepts from A to B and sends to A.
2 Eve computes , i.e. .
3 A computes . Thus, Eve and A have a common secret key .
4 Eve intercepts from B to A and sends to B. Then Eve and B establish a common secret key . .
When Asends a message to Bencrypted with 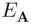 then Eve intercepts it, decrypts it with
then Eve intercepts it, decrypts it with 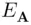 , encrypts it with
, encrypts it with 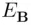 and sends it to B. Bdecrypts it with
and sends it to B. Bdecrypts it with  .
.
Aand Bhave no idea that Eve is in possession of their secret. To avoid the attack, Aand Bneed a procedure that authenticates A (B)to B (A). One way of achieving this is by using digital signatures.
3.9 TLS (Transport Layer Security)
TLS is used to protect data during communication via the Internet. Prior to TLS, the Secure Socket Layer (SSL) protocol was used for secure Internet transactions. The SSL protocol was developed by the Netscape corporation in the 1990s. It evolved into the TLS protocol [MC19,Res18,RNGC19], with the original TLS version 1.0 essentially being SSL version 3.1 [NIS20]. TLS is designed to provide authentication, confidentiality, and data integrity protection between two communicating entities. It is widely used to secure communications in online transactions, including financial transactions, such as online banking and online purchases, and healthcare transactions, such as viewing online medical records [MC19].
Most people will have encountered TLS on a regular basis while making purchases online, logging into accounts, such as social media accounts over the Internet. When doing these via a web browser (such as Google Chrome, Safari, Firefox, Microsoft Edge), these types of applications use HTTPS (Hyper‐Text Transfer Protocol – Secure), which can use TLS. Note that HTTP should never be used to access websites when sensitive or valuable information is involved, such as login names and passwords, bank information. So before entering or accessing any sensitive or valuable information into a website via web browser, always be sure that the URL you are accessing has https:before it (e.g. https://www.amazon.com) as opposed to http:.
As mentioned, TLS is designed to provide authentication, confidentiality, and data integrity protection between two communicating entities. It uses an encrypted channel for communication between a client and a server (with the “client” often being one's web browser). This protects e‐mail messages, for example, from man‐in‐the‐middle attacks during message transmission. (See Section 7.4 for a discussion of Man‐in‐the‐Middle attacks.)
TLS uses a combination of symmetric encryption (such as AES from Chapter 5) and asymmetric encryption (such as RSA from this chapter). Asymmetric cryptography is generally slower and is used for authentication and distributing a shared secret. Symmetric encryption is quicker but needs a shared secret which the asymmetric algorithm provides. The symmetric encryption is used for the actual encrypted transaction.
Before a secure TLS transaction occurs, the server (eBay, Amazon, PayPal, etc.) must generate a public key/private key pair, and then get this pair signed by an authority. This signed information is called the certificate. The person (or organization) that signs the certificate knows as the certificate authority(CA). Anyone may sign a certificate, but every machine maintains a list of trusted CAs, and if the server's certificate is not signed, a warning is usually produced.
Читать дальше

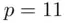 ,
, 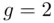 ,
, 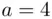 and
and 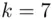 . Then
. Then 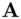 has the private key
has the private key  and the public key
and the public key 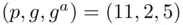 since
since 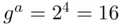 and
and 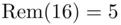 . Let the hash of the message
. Let the hash of the message  be
be 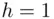 .
. 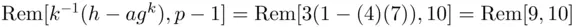 . Then
. Then 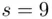 . Thus,
. Thus, 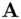 's signature is
's signature is 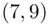 . Condition 2 is then satisfied for this signature.
. Condition 2 is then satisfied for this signature.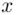 , and intercepts both
, and intercepts both 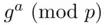 from Ato Band
from Ato Band 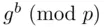 from Bto A. The procedures is as follows:
from Bto A. The procedures is as follows: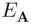 then Eve intercepts it, decrypts it with
then Eve intercepts it, decrypts it with 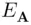 , encrypts it with
, encrypts it with 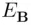 and sends it to B. Bdecrypts it with
and sends it to B. Bdecrypts it with 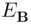 .
.










