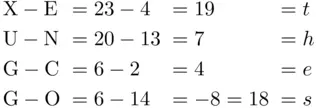To break such a cipher, one can decrypt the message by trying all 26 keys (this is referred to as an exhaustive search). For long messages, the likelihood of a cipher text decrypting to two intelligible messages is small.
We mention here briefly affine ciphers . They are similar to Caesar ciphers in that they are simple substitution ciphers, but they differ in that enciphering involves not only addition, but also multiplication as well.
The Scytale cipher was introduced around 500 BCE by the Spartans, who used this rather simple but effective method to send crucial planning data between generals and bureaucrats. Both the sender and receiver were in possession of a cylindrical tube of the same diameter. To encode the message, the sender would wrap a thin strip of paper around the tube, with the paper spiraling its way down the length of the tube. The message was then written on the strip, with letters being written one beneath the other until the end of the tube was reached. (The message was then continued by starting a new column of letters, and this process was repeated until the message was finished.) To encode, the sender would simply unwrap the paper, leaving a thin strip of unintelligible letters. To decode, the receiver only had to wrap the paper around their similar tube and read the message off in columns.
It is often much simpler to duplicate the Scytale process with pencil and paper. Using a preselected number of rows (this number is the cipher key), write the message in columns. Then, “unwrap” the message by writing a string of characters consisting of the concatenated rows. For example, the message “THE ENEMY WILL ATTACK AT DAWN” is encrypted as follows:

Knowledge of the cipher key reduces the decryption process to a trivial matter. Using the fact that the key for this example is six, count up the total number of characters and divide by six. Doing so yields the period of the sequence, which is four. Thus, by taking the first, fifth, ninth,  characters, one can reconstruct the columns. Upon completion, the message can be read off, column by column.
characters, one can reconstruct the columns. Upon completion, the message can be read off, column by column.
The Scytale concept can be modified to create very complex ciphers. By arranging the plain text in varying matrix patterns and “unwrapping” in different ways, messages can be scrambled very effectively. The Scytale cipher, along with its variants, belongs to a class of ciphers called transposition ciphers, in which all plain text characters are present in the cipher text, but they appear in a substantially different order.
The next classical cipher of great interest is known as the Vigenère cipher. Although it is a relatively simple concept, it has influenced many ciphers used throughout history, including some that are still in use today. The idea is to modify the notion of Caesar ciphers, which were covered in Section 2.2. Instead of a single cipher key, we make use of an entire keyword, which is a key in the form of a string of letters chosen by the user. For example, suppose we decide to use the word “encode” as our keyword. The enciphering process is carried out as follows. The keyword is repeated as many times as necessary to span the length of the message. Each letter corresponds to a number between 0 and 25 (so 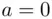 ,
, 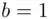 ,
,  ,
, 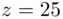 ). Then, to encipher, we add the corresponding numbers of the keyword and the message, subtracting 26 if the sum is bigger than 25. Then we switch back to letters to get the cipher text. For example, if the message letter is
). Then, to encipher, we add the corresponding numbers of the keyword and the message, subtracting 26 if the sum is bigger than 25. Then we switch back to letters to get the cipher text. For example, if the message letter is 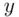 (
( 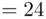 ), and the keyword letter is
), and the keyword letter is 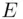 (
( 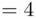 ), then the cipher text letter corresponds to
), then the cipher text letter corresponds to 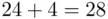 . However, 28 is larger than 26, so we subtract 26 to get 2, which is
. However, 28 is larger than 26, so we subtract 26 to get 2, which is  . Thus,
. Thus,  enciphers to
enciphers to  .
.
| Keyword: |
E |
N |
C |
O |
D |
E |
E |
N |
C |
O |
D |
E |
E |
N |
C |
| Message: |
t |
h |
e |
s |
k |
y |
i |
s |
f |
a |
l |
l |
i |
n |
g |
| Cipher text: |
X |
U |
G |
G |
N |
C |
M |
F |
H |
O |
O |
P |
M |
A |
I |
Notice that each letter of the cipher text is shifted by varying amounts, unlike the Caesar cipher. Interpreting this as many monoalphabetic ciphers acting on individual characters, it is easy to see why the Vigenère cipher is referred to as a polyalphabetic cipher.
To decipher, simply subtract the value of the respective key letters from each cipher text letter. For example, to decrypt the cipher text “XUGGNCMFHOOPMAI” from above, we use the keyword “ENCODE” as follows:
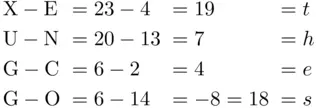
Repeat the process until all plain text characters have been determined. This enciphering process is easy if one has knowledge of the key. However, it can be difficult to break the cipher without such information. This will be investigated in Section 2.6.
The Vigenère cipher is known as a type of block cipher, where the block length is equivalent to the key length. In a block cipher procedure, the plain text or message is encrypted block by block, rather than character by character.
There are a few important remarks to be made regarding the use of the Vigenère cipher. First, because the same plain text character enciphers to different characters depending on the position, the cryptanalysis of such a cipher is much more complex than for a simple monoalphabetic substitution cipher. We also point out that the Vigenère cipher was invented to hide the frequencies of letters in the English language. The Caesar cipher, for example, does not do this. Also, if the key phrase “VIGENERECIPHERX” had been used instead of “ENCODE,” in our previous example, the encrypted message would have had perfect secrecy. Perfect secrecy is achieved if the cipher text yields no information about the plain text, and this occurs, roughly speaking, when the keyword is as long as the message itself. Such a secure system can be obtained using one‐time pads, which we investigate later in the book.
Читать дальше


 characters, one can reconstruct the columns. Upon completion, the message can be read off, column by column.
characters, one can reconstruct the columns. Upon completion, the message can be read off, column by column.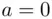 ,
, 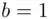 ,
,  ,
, 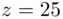 ). Then, to encipher, we add the corresponding numbers of the keyword and the message, subtracting 26 if the sum is bigger than 25. Then we switch back to letters to get the cipher text. For example, if the message letter is
). Then, to encipher, we add the corresponding numbers of the keyword and the message, subtracting 26 if the sum is bigger than 25. Then we switch back to letters to get the cipher text. For example, if the message letter is 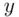 (
( 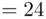 ), and the keyword letter is
), and the keyword letter is 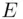 (
( 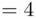 ), then the cipher text letter corresponds to
), then the cipher text letter corresponds to 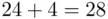 . However, 28 is larger than 26, so we subtract 26 to get 2, which is
. However, 28 is larger than 26, so we subtract 26 to get 2, which is 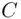 . Thus,
. Thus, 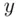 enciphers to
enciphers to 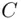 .
.