The first step to understanding and configuring Spanning Tree is to get a handle on the logical topology of each VLAN, so we'll start by looking at VLANs and trunking. After that, you'll learn about Rapid Per-VLAN Spanning Tree (RPVST+ or RSTP), which is the most common Spanning Tree protocol in use today. We'll then cover Multiple Spanning Tree Protocol (MSTP) and finally some Cisco-proprietary Spanning Tree extensions. You can classify each STP type by the approach it uses to prevent loops. There are three approaches:
802.1D—Avoids a loop in the LAN.
PVST—Prevents loops in a VLAN. Most of the time this is what people mean when they say “Spanning Tree.”
MST—Prevents loops in an arbitrary group of VLANs.
Keep these differences in mind as you read through this chapter.
The Need for Spanning Tree
There's nothing inherently problematic about having physical loops. The physical loops become problematic only when they create layer 2 loops. In Figure 2.1, all links are in VLAN 1, creating a loop between each pair of switches as well as among them. We could easily eliminate these layer 2 loops in two ways:
By removing the physical loops
By doing away with a stretched VLAN and turning each link into a routed (layer 3) link, where each link represents a separate broadcast domain
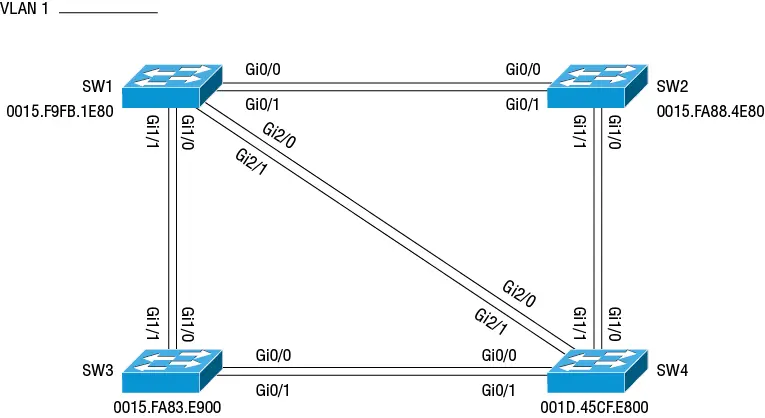
Figure 2.1 Physical looped topology
The latter option would eliminate any chance of a broadcast storm and, from a scalability and stability perspective, would be ideal. We'll cover routed topologies in Chapter 3, “Enterprise Network Design.” Although a routed topology is ideal, implementing it requires planning and effort that the organization may not be willing or able to spend. Many therefore extend VLANs across several switches connected together, often in a loop for redundancy.
The goal of STP is to impose a loop-free logical topology by strategically dropping certain Ethernet frames on specific interfaces (what STP calls ports) to prevent them from endlessly looping through the network. You should already have at least a passing familiarity with Spanning Tree. Before continuing, take a moment to test your understanding by trying to calculate the root bridge and root ports for the topology in Figure 2.1.
To refresh your memory, the STP process is as follows:
1 All switches elect a root bridge. The root bridge doesn't block any traffic but forwards frames normally.
2 Each non-root switch determines its root port. The root port is the port that provides the lowest-cost path back to the root bridge. Any other ports leading back to the root block frames to prevent a loop from forming between the root and the non-root bridge.
3 Each connected pair of non-root switches elects a designated bridge for that link or segment. The designated bridge forwards frames over that link normally, whereas the other bridge doesn't forward any frames. The result is a logical loop-free topology, as shown in Figure 2.2.
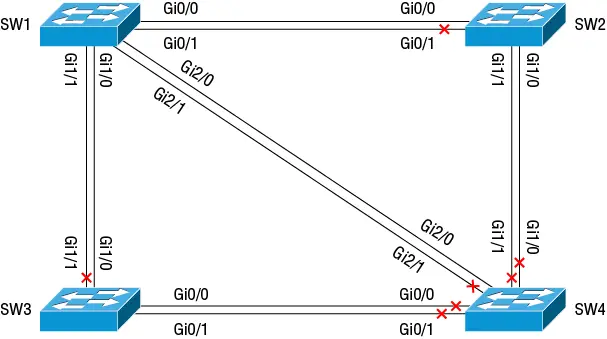
Figure 2.2 Converged STP topology with SW1 as the root
The first step in configuring or troubleshooting Spanning Tree is to ensure your VLANs and trunks are configured properly. Although we naturally think of Spanning Tree as an answer to loops caused by redundant physical connections, bridging loops actually only occur when a layer 2 loop exists in a VLAN. It's possible—indeed, preferable—to configure your trunks in such a way that they don't form a loop to begin with. We'll cover design considerations around VLANs and trunks in Chapter 3. But for Spanning Tree, recognize that the first step is to figure out what VLANs you should have on each switch and what trunks those VLANs should traverse.
Most networks have multiple VLANs stretching across 802.1Q trunks. Ideally, you'll selectively prune VLANs from trunks where you don't need those VLANs. Because any given trunk may carry some VLANs and not others, it's possible for there to be layer 2 loops in one VLAN but not in another. Consider the two VLANs in Figure 2.3. All trunks carry VLAN 3, creating a loop. But only the trunks between SW1 and SW2, SW3, and SW4 carry VLAN 2.
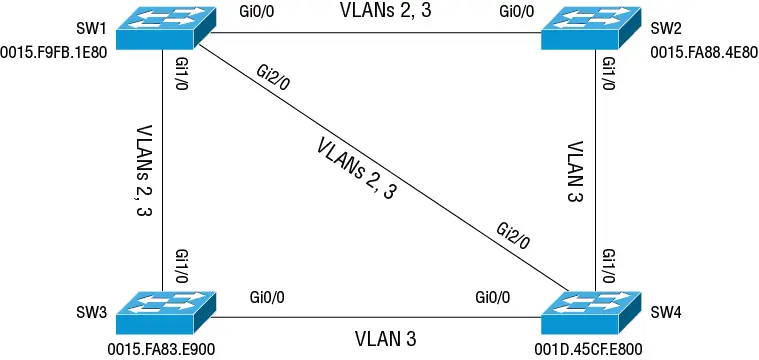
Figure 2.3 Multiple VLANs over 802.1Q trunks
To eliminate the bridging loops in VLAN 3, Spanning Tree must block VLAN 3 traffic from traversing two links. (As a fun exercise, see if you can figure out which two.) VLAN 2 has no loops, so there's no need to block anything. Although we typically say that STP “blocks a port,” this isn't quite accurate. If Spanning Tree were to truly block a port, it would block traffic for all VLANs, not just the one with the loop. This isn't what happens. What it does to break the loop is drop Ethernet frames ingressing a particular port on a particular VLAN. Hence, in order for Spanning Tree to be useful in a multi-VLAN environment, it must treat each VLAN independently.
Per-VLAN Spanning Tree+ (PVST+) is Cisco's implementation of the original Spanning Tree specification, IEEE 802.1D. PVST+ creates a separate Spanning Tree instance for each VLAN. You can configure each Spanning Tree instance differently so that a port blocked for one VLAN will be forwarding for another. This way, you can simultaneously use all available physical links. PVST+ is also sometimes called Shared Spanning Tree Protocol (SSTP).
RPVST+ performs the same basic function as PVST+ but has a faster convergence time—the speed at which each switch settles on which ports to block. As of IOS 15.2(4)E, RPVST+ is the default mode.
MST (802.1s) is similar to RPVST+, except instead of having one Spanning Tree instance per VLAN, MST lets you choose the specific VLANs that belong to each Spanning Tree instance. It's useful for when you have a large number of VLANs and want to minimize the number of Spanning Tree instances to conserve switch resources. In order for a pair of switches to run a PVST+, RPVST+, or MST instance for a VLAN, you need a confluence of several things:
All switches in the topology must have the VLAN configured.It sounds obvious, but a Spanning Tree instance can't participate on a VLAN that doesn't exist. The VLAN must be configured locally on the switch before Spanning Tree can become active for that VLAN.
All switches must have trunks between them.A trunk is always between only two switches. For both switches to establish a trunk, two things must occur:
Both switches must be configured to form a trunk.
Both must agree on the trunk encapsulation type to use 802.1Q or Cisco Inter-Switch Link (ISL).
The VLANs must be allowed on the trunk.Simply establishing a trunk isn't sufficient to carry traffic for a VLAN. Both switches must have the VLAN allowed on the trunk. By default, all VLANs are allowed on a trunk, but it's possible to remove or prune a VLAN from a trunk. We'll look at an example of this in a moment.
Connected switches can form a trunk between themselves automatically using the Dynamic Trunking Protocol (DTP). DTP can operate in one of two modes:
Desirable—DTP actively attempts to negotiate a trunk with the switch on the other end. An easy way to remember this is that the switch desires to form a trunk.
Читать дальше















