1 ...7 8 9 11 12 13 ...16 Large data centers are built by various cloud providers across the world, which have the capacity to serve users from around the world. Hence there exists a separation from the cloud centers to the users, which creates delays, latencies. Another disadvantage of cloud services due to distance of separation is location access can never be accurate. Information about users and their mobility is also another disadvantage of cloud computing. In augmented reality applications like cloud gaming as discussed for real-time tracking system applications like vehicular systems, a unique computing method is required, which is achieved by edge computing [7].
Edge computing enables the deployment of cloud computing capabilities at the edge of the network. The infrastructure providers own the data centers and implement multi-tenant virtualization. The third-party customers, end users, and infrastructure providers can access these edge data centers. Edge computing services are automated, thus refraining from disconnecting from the cloud. This leads to the possibility of creating a hierarchical multi-tiered architecture. Edge computing leads to an open ecosystem where one trusted domain cooperates with other trusted domains and a multitude of customers are served. Though there are multiple edge paradigms with few differences, there are also similarities [8]. Edge Architecture’s outline is provided below for understanding before dealing with the challenges and the solution using mathematical models (Markov Chain Model and game theory), deep learning and evolutionary algorithm.
All the edge activities are controlled by two-tier architecture, so it works properly in time-sensitive systems. The design of two-dimensional structures focuses primarily on efficiency, application management, and edge management.
The edge network aims to reduce the data strain by providing computation away from data centers towards the network’s edge. To provide services for cloud computing, an edge computing network is created by using smart objects and network gateways and decentralizing the data centers. The edge network consists of three layers, among which Edge devices are the first layer. Edge devices are the data providers that include user gadgets, e.g., sensors, machines, smartphones, and wearables, as shown in Figure 2.1. They are responsible for data collection and delivery [7]. Edge nodes, the second layer of the network layer, are the router, switches, and small/macro base stations responsible for computing operations and data processing and data routing [9]. The third layer is the cloud that consists of data centers, servers, databases, and storage, and is responsible for data analytics using Artificial intelligence, visualization, and other high computational requirements [9].
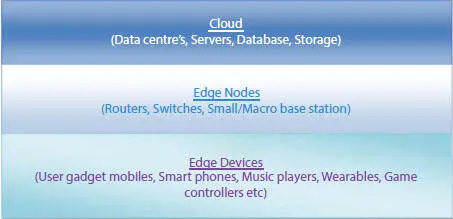
Figure 2.1 Edge network.
The three-tier architecture, Edge Computing (EC), acts as a complement to cloud computing. It is appropriate for applications with sensitive time functions as well as activities that strengthen counting [10]. Critical time operations are managed on the margins, and computer consolidation tasks are performed in the cloud. The three-dimensional structure focuses primarily on the Interface between the cloud and end, as well as the assigned function. Edge computing is part of the cloud-based IoT system. Edge computing improves the performance of the IoT system. To understand the need for edge computing, we need first to understand cloud-based IoT functioning.
Then computing has been backed by the centralized network with cloud computing, which allows the users to consume large numbers at any time in different places based on the pay concept. In the concept of cloud computing, there is a frequency of communication between the centralized server and user models such as smartphones, smartwatches, etc. [5].
The physical distance between the end device and the cloud server is typically vast. It leads to an increase in response time because of the considerable distance. In cloud computing, there are many challenges to provide uninterrupted service by having a good communication link to the end user, especially when the distance between the cloud server and end device is large and the device is on mobility. For example, a person with a mobile who moves from one place to a different place requires a large number of cloud servers with short response time and depends on the stability of cloud nodes. It triggers a lot of research – based on beyond the clouds towards the edge of the network, as shown in Figure 2.1[8]. This Edge Computing system overcomes the challenges noted above of a cloud-based IoT system. As shown in Figure 2.1, edge network nodes are formulated in such a way they will be close to the end device and doing part or full computation of cloud server by offloading the load from it. Since the computation is done locally, the system’s performance can be improved with significantly less response time.
An extensive literature survey on edge computing with different applications has been done to improve performance in a cloud-based IoT system.
2.1.3 Edge Computing Motivation, Challenges and Opportunities
As discussed in the preceding section, the aim of having edge computation is to decrease the data strain from the cloud towards the edge of the network. Hence there is the possibility of deploying and running a number of applications at the edge of a network. The implementation of edge computing has a lot of potential and advancement in many industries.
i) Motivation for Edge Computing:
The motivation for edge computing is drawn from its speed of communication. Facial recognition is one of the applications from where it can be inferred that edge computing excels in applications that require short response time [1]. As computing is done closer to the source, visual guiding applications like Google maps create better user experiences. The cloud system becomes less loaded due to offloading offered by edge computing, thus becoming energy efficient. Communication between the initial layer, i.e., smart homes and cloud drain the battery, therefore, an alternative as the edge can overcome the problem [12]. Network traffic and data explosion is prosperity that tempts to adopt edge computing. There are yet many edge computing powers that are clearly mentioned in Figure 2.2. To achieve cloud decentralization and low latency in computing. Resource allocation of front-end devices can be overcome by sustainable energy consumption, which drives edge computing motivation. Edge computing also enhances and supports smart computing techniques.
ii) Edge computing challenges:
In order to implement edge computing, it is vital to take challenges into account.
Privacy and Security - As edge computing works with various nodes, traveling to and from different networks requires special encryption mechanisms for security ( Figure 2.2). Resource containment being one of the properties of edge computing, security methods are required [1].
Optimization metrics - Edge computing is a distributed paradigm. The workload has to be deployed in various data centres effectively depending on bandwidth, latency, energy, and cost to reduce the response delay [12]. Experiencing uncompromising QoS is another challenge of edge computing ( Figure 2.2).
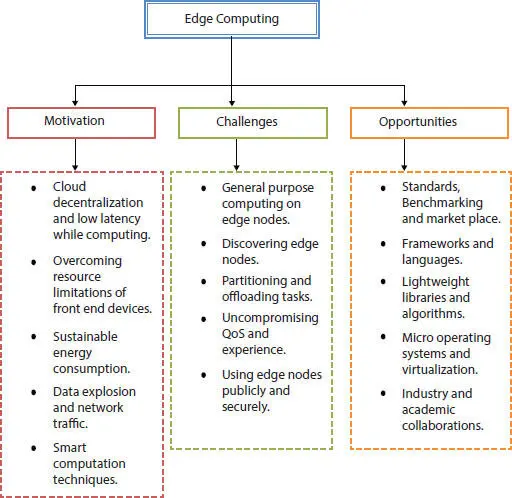
Figure 2.2 Edge computing motivation, challenges and opportunities.
Читать дальше














