After the user has satisfied their business responsibilities, accountants then have review and audit processes in place to ensure that information is accurate, with no discrepancies. For example, I worked in a fast food restaurant where they tracked the number of servings of expensive foods. The restaurant served fried clams, and because the point-of-sale system could track every order, the store manager had to count the available servings at the beginning and end of the shift, and they had to ensure that sales matched the difference in available servings.
Though the clams were a specific example, all mature organizations track just about everything in and everything out. The accounting process looks to ensure proper tracking of financial resources. Some of it is to ensure proper financial reporting for taxes and investors. They look for any deviations in expectations. The reason for deviations don’t matter.
In cybersecurity, you have to apply these lessons and use behavioral analytics, review log files, and otherwise look for evidence of violations of security procedures. Though this is a critical response issue, reviewing this information can also tell you where user behaviors need to be improved.
 Much like an accountant’s job is to identify deviations — whether the deviation is caused by error, accident, or malfeasance — when a user deviates from defined practices, the system should not care. It should be identified and investigated. Your organization should detect an action regardless of motivation. For example, if a user attaches a sensitive file to an email, it should be stopped regardless of whether it’s an accident or the user has malicious intent.
Much like an accountant’s job is to identify deviations — whether the deviation is caused by error, accident, or malfeasance — when a user deviates from defined practices, the system should not care. It should be identified and investigated. Your organization should detect an action regardless of motivation. For example, if a user attaches a sensitive file to an email, it should be stopped regardless of whether it’s an accident or the user has malicious intent.
Whenever a deviation occurs, the type of deviation drives the follow-up process. It’s possible that forms, such as an expense form, will be returned for revision. If something valuable appears to be missing, it might inspire an investigation. In extreme cases, there might be a need for forensic accountants to complete a detailed investigation.
Applying the ABCs of Awareness
The mark of success for an awareness program is that people change their behaviors as required. For security awareness programs, these behavior changes should provide a return on investment and justify the awareness program, as Chapter 8discusses in detail.
In short, the ABCs of awareness mandate that awareness influences behavior. Behaviors practiced consistently create the culture. Culture in turn provides awareness and drives behaviors.
The goal is for awareness to influence behavior. Then behaviors, practiced consistently, create a culture (or consistent behaviors practiced across the organization) , and in the case of a security awareness program, they create a security culture. Your security culture then helps to drive both awareness and behaviors. Figure 3-1 illustrates this relationship.
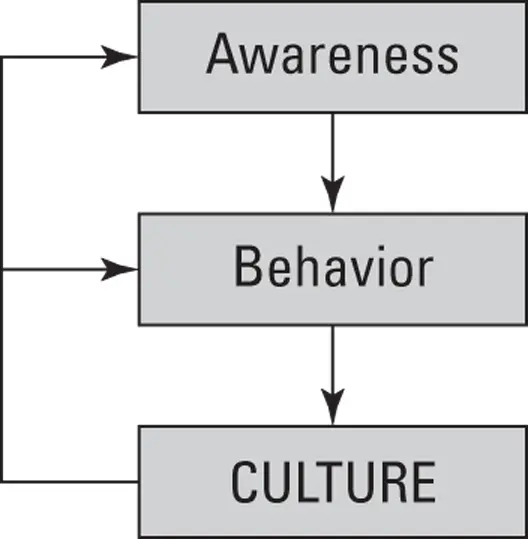
FIGURE 3-1:The ABCs of awareness.
 Having awareness doesn’t matter if users don’t practice the desired behaviors. Most people know not to reuse passwords across multiple accounts, for example, yet you still face incidents unnecessarily because users reuse their passwords. In 2019, criminals published credentials for more than 3,000 Ring cameras in people’s homes. They were able to hack in and interact with children, using passwords that had been stolen in hacking incidents and then sold on the dark web. Though the passwords were from various websites, attempts to use them to access the cameras were successful because the parents had used the same passwords on the Ring account as they did on other Internet accounts.
Having awareness doesn’t matter if users don’t practice the desired behaviors. Most people know not to reuse passwords across multiple accounts, for example, yet you still face incidents unnecessarily because users reuse their passwords. In 2019, criminals published credentials for more than 3,000 Ring cameras in people’s homes. They were able to hack in and interact with children, using passwords that had been stolen in hacking incidents and then sold on the dark web. Though the passwords were from various websites, attempts to use them to access the cameras were successful because the parents had used the same passwords on the Ring account as they did on other Internet accounts.
If behaviors are consistently poor, the security culture is weak. If senior employees choose not to wear their badges, a new hire walking into the organization will soon stop wearing their badge too, no matter what the awareness posters say.
 Have you ever heard someone say that it’s easier to stay in shape than to get in shape? In other words, if you’re already fit, you can just continue to do what you’re doing to stay fit. Otherwise, you have to change and improve something in order to become fit. It’s the same for a security culture: If it’s strong, it’s easier to maintain a strong security culture than to strengthen a weak security culture. Just making people aware of what they should do won’t change their behavior, because the culture reinforces the weak behaviors. You need to consider how to change the culture, and that takes more effort than just attempting to tell people what to do.
Have you ever heard someone say that it’s easier to stay in shape than to get in shape? In other words, if you’re already fit, you can just continue to do what you’re doing to stay fit. Otherwise, you have to change and improve something in order to become fit. It’s the same for a security culture: If it’s strong, it’s easier to maintain a strong security culture than to strengthen a weak security culture. Just making people aware of what they should do won’t change their behavior, because the culture reinforces the weak behaviors. You need to consider how to change the culture, and that takes more effort than just attempting to tell people what to do.
Benefiting from Group Psychology
Psychology that focuses on individuals is helpful to relate to people in intimate settings and in generalities, but if you’re trying to change behaviors consistently across a large organization, the study of the individual has limited value. You need to influence an organization as a whole or, more specifically, you need to influence the security culture.
Clearly, to influence the culture, you have to influence the individuals within the organization. However, when you’re trying to influence a culture, you’re not trying to influence everyone — rather, you’re influencing as many people as possible. For example, in the cybersecurity field, everyone ideally has strong and unique passwords. However, as I discuss later in this chapter, perfect security will never exist — only risk reduction.
In many ways, this may sound like an attempt to create a one-size-fits-all strategy. The reality is that you’re creating a one-size-fits- most strategy. Again, ideally, you would be able to meet with all individuals and work with them to have them understand the desired behaviors and convince them to enact the behaviors in a style through communications that are best for their learning styles. Again, that strategy isn’t practical, so you have to look at ways to influence groups of people, regardless of the individual learning styles. Admittedly, you will never get everyone — but, again, your goal is optimized risk reduction.
The ABCs of behavioral science
The ABCs of behavioral science are similar to the ABCs of awareness, but with important differences: The ABCs of awareness lay out a path, and the ABCs of behavioral science define motivation. (See Figure 3-2.)
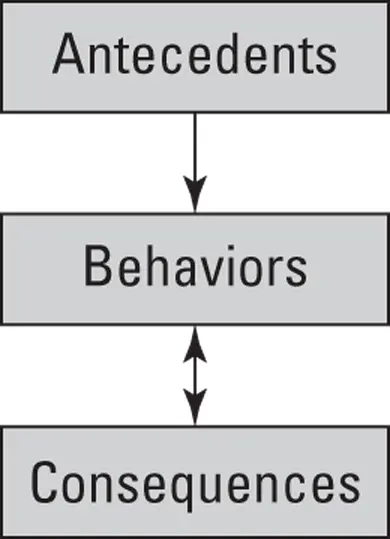
FIGURE 3-2:The ABCs of behavioral science.
Here’s how to break down the ABCs of behavioral science:
A stands for a ntecedents. In the context of this book, an antecedent is something that intends to influence a behavior. Antecedents in the security field are usually security awareness efforts. For example, users might see posters reminding them to wear their security access badges.
B stands for b ehavior. The B is the desired behavior that you’re trying to create. For example, users may be expected to wear their badges at all times while in the building.
Читать дальше

 Much like an accountant’s job is to identify deviations — whether the deviation is caused by error, accident, or malfeasance — when a user deviates from defined practices, the system should not care. It should be identified and investigated. Your organization should detect an action regardless of motivation. For example, if a user attaches a sensitive file to an email, it should be stopped regardless of whether it’s an accident or the user has malicious intent.
Much like an accountant’s job is to identify deviations — whether the deviation is caused by error, accident, or malfeasance — when a user deviates from defined practices, the system should not care. It should be identified and investigated. Your organization should detect an action regardless of motivation. For example, if a user attaches a sensitive file to an email, it should be stopped regardless of whether it’s an accident or the user has malicious intent.
 Have you ever heard someone say that it’s easier to stay in shape than to get in shape? In other words, if you’re already fit, you can just continue to do what you’re doing to stay fit. Otherwise, you have to change and improve something in order to become fit. It’s the same for a security culture: If it’s strong, it’s easier to maintain a strong security culture than to strengthen a weak security culture. Just making people aware of what they should do won’t change their behavior, because the culture reinforces the weak behaviors. You need to consider how to change the culture, and that takes more effort than just attempting to tell people what to do.
Have you ever heard someone say that it’s easier to stay in shape than to get in shape? In other words, if you’re already fit, you can just continue to do what you’re doing to stay fit. Otherwise, you have to change and improve something in order to become fit. It’s the same for a security culture: If it’s strong, it’s easier to maintain a strong security culture than to strengthen a weak security culture. Just making people aware of what they should do won’t change their behavior, because the culture reinforces the weak behaviors. You need to consider how to change the culture, and that takes more effort than just attempting to tell people what to do.











