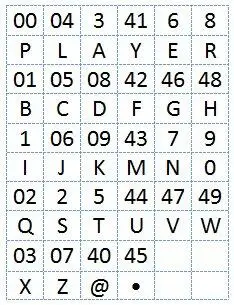
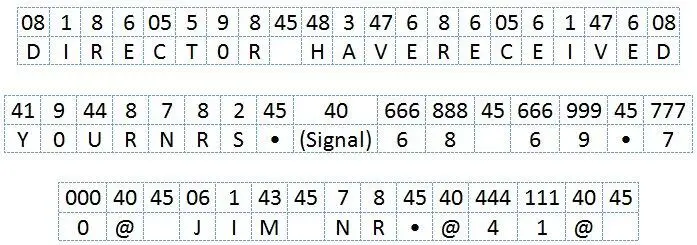
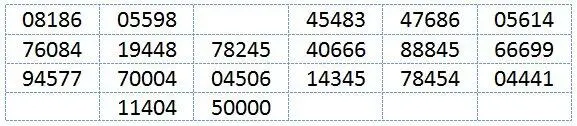
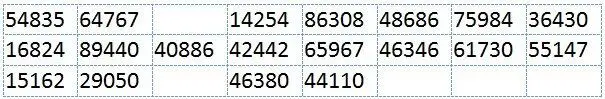
Alexander Foote - Handbook for Spies
Здесь есть возможность читать онлайн «Alexander Foote - Handbook for Spies» весь текст электронной книги совершенно бесплатно (целиком полную версию без сокращений). В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Город: N. Y., Год выпуска: 1949, ISBN: 1949, Издательство: DOUBLEDAY & COMPANY, INC., Жанр: military_history, История, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Handbook for Spies
- Автор:
- Издательство:DOUBLEDAY & COMPANY, INC.
- Жанр:
- Год:1949
- Город:N. Y.
- ISBN:1-61646-067-9
- Рейтинг книги:5 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
Handbook for Spies: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Handbook for Spies»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
After the War, he spent some time in the Eastern Bloc and then returned to the West and published his book, A Handbook for Spies. He died in the 1950s.
Because of the implausible veracity of the intelligence (fast, plentiful, and accurate) and never explained source of the Lucy Ring's information, suspicion attaches to all those associated with it. Since Foote, as the Lucy Ring's radio operator was a central cog in the chain of supply and therefore in a position to know much, his subsequent account has been thought to be rather dubious in places. This and the fact that he seemingly managed to return to the West rather easily, has led some to suggest Foote was a British Secret Service double agent and one conduit (perhaps even the main one) of intelligence from Britain to Roessler and thence to Moscow.
According to various sources, Foote was indeed a MI6 (SIS) double agent unbeknownst to Rado. After the destruction of Rado's network and his escape from Switzerland, Rado met Foote in Paris and both were ordered to return to Moscow immediately. They took off aboard a Russian military aeroplane on January 6, 1945, taking a circuitous route (due to the war being still in progress) via Egypt. Their plane landed to refuel in Cairo, where upon Rado defected. Continuing alone to Moscow, Foote was subjected to intensive interrogation in an attempt to determine his loyalty and the possibility of his being a penetration agent. Foote was confronted with an instance of disinformation sent from his transmitter in May 1942 and told "That message cost us 100 000 men at Kharkov and resulted in the Germans reaching Stalingrad." Foote said that he merely passed on what he received from Radó. Satisfied with Foote's explanation, the Soviets gave Foote a false identity under the alias of Major Granatov. Posing as a German, Albert Müller, he inserted himself into post war Berlin to establish this alias with the aim of being sent by Moscow Centre to Argentina, to attempt to identify and infiltrate groups of escaped high ranking Nazis.
Journalist, broadcaster and author Malcolm Muggeridge, himself a wartime MI6 officer, "got to know Foote after the war" (pp 207-08) when Foote paid Muggeridge "regular visits" at his flat near Regents Park, London. Foote at this time was working as a clerk in the Ministry of Agriculture and Fisheries, work he found, according to Muggeridge, "very tedious". Muggeridge is firmly of the opinion that the information Foote sent "could only, in fact, have come from Bletchley"
In March 1947, following the defection of a Soviet agent who had been involved with British Intelligence, Foote's allegiance to the British may have been confirmed. Foote himself defected from his Russian control in Berlin, escaping to the British sector.