1 ...6 7 8 10 11 12 ...16 A Balanced Energy Consumption (BEC) protocol is designed by [4]. In this protocol the relay node is selected with cost function which is based on distance of node form sink. To distribute load uniformly each relay node is selected for a specific round. Nodes nearer to the sink can transmit data immediately to the sink, otherwise data is passed to closest relay node. A threshold value of residual energy is also fixed on meeting the threshold value node only send critical data to sink. A simulation study has shown the better performance in term of network lifetime. Another attempt to achieve better throughput in terms of energy-consumption is achieved in heterogeneous WBAN [5]. It also works on the same principal. Residual energy, data rate and distance from sink, is the basic selection criteria for selection of relay node. Key requirement of any WBAN is minimum delay and energy efficiency. To improve the clustering in WBAN a load balancing and position adaptive technique is proposed by [6]. For the selection of cluster head the author used probability distribution method. A centralized clustering method is proposed by [7] to optimize the consumption of energy in WBAN. The cluster tree based structure is designed for the formation of uniform clusters.
An adaptive routing protocol is deployed by the author in [8]. The channel/link information is used for the purpose of selection of best relay nods for reduction of energy consumption per bit. Sender node only sends the data to sink, by relies on nodes only when the link quality is up to the predefined level of threshold. Otherwise it transmits information to the sink, directly. Omar Smail et al. , proposed an energy efficient routing protocol for WBANs [9]. They use residual energy to increase network lifetime. This method used to select energy efficient stable links. In [10] a fuzzy adoptive routing protocol is proposed. It uses clustering mechanism for direct communication with sink node. In decision of forwarding it takes in account the criticality and location. Another routing protocol is proposed by [11] in which routing is managed by mobile-sink, it discovers the shortest route among numerous unequal clusters. This makes sure to avoid the energy hole problem in the network. Results have shown that this clustering technique performed well. A secure cluster base strategy for both inter-WBAN and intra-BAN is purposed by [12]. For intra-WBAN they used to generate a pairwise (PV) key. The best thing about PV is the keys generation on both sending and receiving end is the same. In the result of the highly dynamic nature of the human body, generated PV is time-variant. In inter-BAN communication, clusters are formed on the bases of two parameters (residual energy and distance). The node which has more energy is more likely to form clusters, in the same way, the node that is more closer to the RBS will have a high probability of becoming the cluster head. Some other authors also used genetic algorithms in WBAN [13–16]. A concept of a virtual cluster is given by [17], they form clusters only among intra-BAN nodes. Although nodes in intra-BAN are fairly close to each other, but due to energy limitation in sensors nodes, this technique gave remarkable results.
By creation of the long-lasting clusters, frequent path search is reduced. We are considering the scenario where multiple WBANs are present. Instead of having a connection of each WBAN with RBS, we considered some of the WBANs are not in the range of RBS. Each WBAN consist of one Personal Server (PS) and multiple sensor nodes. The sensor nodes pass their collected data to the PS and this PS is responsible for further transmission. In our purposed technique PS of different WBANs form clusters. Each cluster contains a cluster head and cluster members (CM) in its vicinity. CH is a selected PS of a WBAN within the WBANs of a cluster. Now all other WBANs will be connected to the CH, multiple CHs of different WBANs can have hop-to-hop communication, and this way data is passed to the nearest AP.
Our communication can be classified into following hierarchal groups.
Sensor node to PS
PS(CM) to CH
CH to RBS
Figure 3.2is describing the actual working of the clustering technique. WBANs of cluster “A” and its CH are not in the range of RBS. But cluster “B” is in the vicinity of RBS, so cluster “B” is capable of communication with RBS. In this case, cluster “A” required the help of cluster “B”. Members of cluster “A” have a direct link with A’s cluster head, further CH-A can establish a connection with CH-B. It is a simple mechanism of clusters communication.
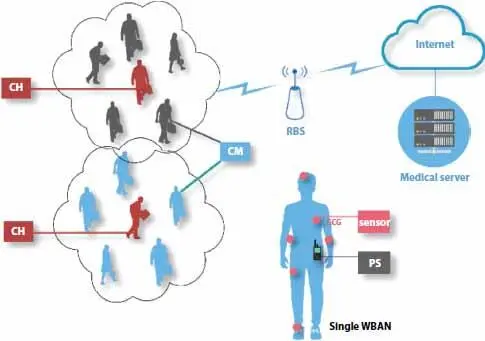
Figure 3.2 Inter-WBAN clustering.
3.3.1 Evolutionary Algorithms
For cluster formation in our purpose methodology we are using Evolutionary algorithms. These nature inspired algorithms form multiple solutions the most efficient and the optimized solution is selected among all solutions. For NP-hard problem there is no known polynomial algorithm so time for finding solution grows exponentially with the size of problem. For solving these problems, we define the desired criterion where our algorithm should terminate. Our defined problem (Clustering in inter-WBAN) is also an NP-hard, as we need to find optimum clusters with multiple nodes and multiple parameters. Most real word problems may have to achieve multi-objective, these objectives may be different in nature. Multi-objectives problems required simultaneous optimization. Each objective is achieved with its specific objective function. These objective functions are measured in different units, and usually, they are conflicting and competing. Suppose we want to buy a railway ticket with low cost and less time to reach the destination. It is a fact that with cheap ticket, railway service will be compromised, and will stop on every station and cost more time. On the other hand, an expansive ticket train may cost less time to reach the destination. Multi-objective functions with conflicting objectives raise the set of optimal solutions, as no single solution can be considered to be best, with respect to all objectives. These solutions can be classified on as dominated and no-dominated sets Figure 3.3.
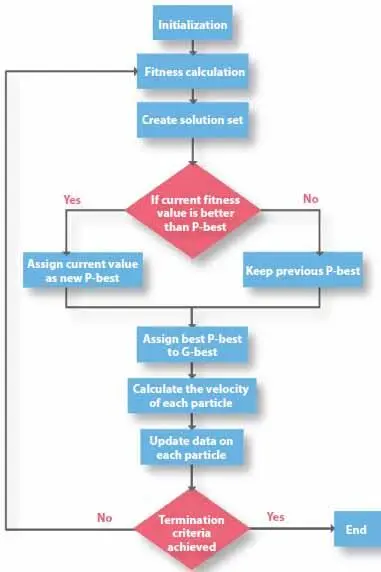
Figure 3.3 Flow chart of proposed scheme.
a) Fitness Calculation
Evolutionary algorithms are used to find a different solution. Every solution generally signified as a string of binary numbers (Chromosome). To come up with the best solution it is required to test all these solutions. For this purpose, we need to identify the score of each solution to find how closely it meets the overall specified desired result. This score is generated by the application of fitness function.
b) Local Best/Global Best
We calculate two values local best and global best, the local best value of everyone, if the current value of velocity of an individual is better than older value, the local best value will be replaced with the new one, otherwise, remain the same. The same goes for the global best value. Global best value is the best value among all the solution sets till now.
Our algorithm consists of two parts. The first part is network creation part, where we specify the basic parameters. Our network is a grid of 1 km × 1 km in size. We specified the transmission ranges from 2, 4, 6, 8, 10 and alternatively we run it with number of nodes from 50, 100, 200, 250, and 300. Network creation part randomly deploys the nodes on the grid. Once the network is created, Evolutionary algorithms start to find optimum clusters. In our experimentation, we used three algorithms,
Читать дальше














