In computer networks, network topology is defined as design of physical and logical network. Physical design is the actual design of the computer cables and other network devices. The logical design is the way in which the network appears to the devices that use it.
In complex networks, network topology is the arrangement of network in generic graph or tree. In general, many domains like medical, security, pipeline of water, gas, and power grid are available in graph structure. These graphs are required to restructure two topologies as d-regular trees and random geometric trees [34]. Initially, rumor source identification is discussed and introduces methods for general trees and general graphs based on rumor source estimator. Rumor source estimator plays a key role in finding the exact source of rumor. Source estimator mainly based on Maximum likelihood (ML) estimation is the same as a combinatorial problem [9, 35]. The following section will explain required techniques such as rumor source estimator, ML estimator, rumor centrality, and message passing algorithms to detect rumor source in trees.
1.5.1.2 Network Observation
In rumor source identification, network structure plays an important role. When structure of network is known, it is easy to find how a rumor is spread in network using diffusion models such as SI, SIS, SIR and SIRS. If back track these diffusion models then rumor source can be detected easily. To know the structure of network another model is used called network observation, which provides information about states of each node present in network at particular time. Those states are in a susceptible node—able to being infected, infected node—that can widen the rumor more while recovered node—that is alleviates and no longer infected [10]. If information of each node likely is susceptible, infected or recovered is observed then it is easy to generate structure of network from that knowledge. Network observation can be done in three ways: complete observation, snapshot observation and monitor observation.
1.5.1.2.1 Complete Observation
Complete inspection of network presents broad information like whether a node is susceptible, infected or recovered at each time of interval in network [11]. It is not enough to know about state of node at one time only and requires multiple time intervals. Complete observation will give this knowledge even in different time intervals. Complete observation of small scale network is easy as size of network is small but it is hardly possible in large scale networks. Figure 1.7depicts knowledge about this problem, as shown in Figure 1.7(a) regular tree with 7 nodes considered as small scale network and complete observation of network can be possible like root node, leaf nodes, degree of nodes, etc. In Figure 1.7(b) a generic graph is shown with many nodes and multiple connections between each node treated as large scale network and observation is not easy as finding the root node, leaf nodes and degree of nodes are difficult in these kind of large scale networks. It is observed that complete observation gives better results to provide knowledge about states of nodes but works only in small scale networks [39] not in large scale network. To overcome this problem another model is used called as snapshot observation.
1.5.1.2.2 Snapshot Observation
It provides limited information about states of nodes in network at given time interval. To avoid this problem, instead of one or two snapshots, taking multiple snapshots will give better knowledge about nodes in different time intervals. Disadvantages of taking multiple snapshots may consume much time, and although it provides correct information about lone contaminated nodes, it cannot distinguish between recovered or susceptible [37]. So it is difficult to understand about nodes in these states i.e. either they received rumor and ignored it or not received yet.
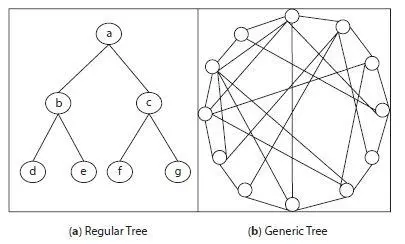
Figure 1.7 Network topology.
1.5.1.2.3 Monitor Observation
Monitor observation means monitoring the network by inserting monitor or sensor nodes in it which works as an observer in network [36]. These sensor nodes gather information about states of nodes and pass this to administrator. The administrator will maintain all gathered data about each node state in a database. But there is chance of missing information in monitor observation as sensor nodes are inserted in a few places of network. Also, there may be a loss of information about some nodes where sensor nodes are not available. Due to unavailability of information of some nodes in network it reduces the accuracy of system, as system is based on number of nodes. If number of nodes increases then accuracy may increase but reduces performance of system due heavy load on network.
These are three types of network observations which help to understand states of nodes and network structure. Network topology and network observation both are used to understand the structure of network. Network structure is one of the best factors that are considered in source identification. Other factors also considered are diffusion model which is mandatory in source identification as discussed in Section 1.5.2.
Diffusion models are also one of the factors considered in source identification as they give information about how fast information diffusion occurs in network [2]. There are four diffusion models namely susceptibleinfected (SI), susceptible-infected-susceptible (SIS), susceptible-infectedrecovered (SIR), and susceptible-infected-recovered-susceptible (SIRS). All these come under epidemic models, which can spread deceases widely from person to other or group of people. These epidemic models are discussed in the following section as well as how they spread and the differences between them.
SI model is one of the oldest epidemic models where S stands for susceptible and I for infected. Initially, for complex networks SI model was proposed by Ref. [12]. If complex networks use SI model then state of nodes is either susceptible or infected. Once a node is infected it could remain in same state throughout life as shown in Figure 1.8.But this model is not practical. There is little chance that a susceptible infected node can be recovered and again in future. In social networks once rumor is received by any user, he/she believes it at that particular time and in the future they may know the truth and recover from it, which is not possible in SI model. The models SIS, SIR and SIRS deal with this issue and these models are discussed in the succeeding sections.
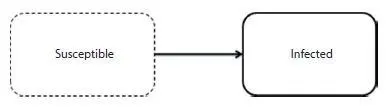
Figure 1.8 SI model.
The SI model is not practically applicable, as it doesn’t allow infected users to be recovered. The SIS model addresses this problem [13, 14], and focuses on number of persons infected and number of persons cured as well. Once anyone is infected they may be cured and become susceptible in the future. Figure 1.9explains the same problem where susceptibility of infection is possible [38]. In social networks once a rumor is received by a user he/she may believe or ignore as they knew fact and can become susceptible in the future.
Читать дальше














