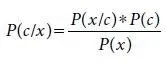Cyber bullying is bullying that happens over digital devices like cell phones, computers, and tablets [26]. It can occur by sending emails, messages through social networks like Facebook, Twitter, Instagram, WhatsApp and software services like Gmail, Yahoo, etc. where a group of people are connected and sharing social information. Some people are misusing these facilities and bullies by sharing abused photos, videos, or negative information about others, etc. [27]. It is very harmful to the society and needs attention to combat and find culprit.
1.3.2.3 Buying Illegal Things
Buying illegal things like Bit coins and drugs belong under criminal activities in India and many other countries. So this is also a one of the cyber-crime that needs attention to prevent and find the source of user who bought those [6].
1.3.2.4 Posting Videos of Criminal Activity
Posting/sharing videos of criminal activities such as abused photos, videos, and disinformation on online social networks is also under cyber-crime [5]. There are some other activities like sharing security issues of country and posts against some religions and communities also falls under this cyber-crime.
These are some popular cyber-crimes but are not limited to many others such as Denial-of-Service attack, Email bombing, spamming, Cyber stalking, etc. [6]. So there is a need to focus on these cyber-crimes and how to prevent and punish the culprits.
1.3.3 Cyber-Crimes on Social Networks
Nowadays, social networks like Facebook, Twitter, WhatsApp, Sina Wiebo, etc. are become very popular in sharing and diffusing any kind of digital information. But sharing all kinds of information is not legal in any social networks. If anyone is sharing illegal information in social networks then it is considered as cyber-crime. Some of the cyber-crimes on social networks are listed in the section below.
1 A. Posting RumorsPosting/sharing any misinformation (unknown) or disinformation (wontedly wrong) is called as rumors. The diffusion of rumors is very fast comparing to the actual news in social networks [5]. Finding whether particular post content is rumor or not is a challenging task, and if it is a rumor, detecting the source of rumor is also becomes a big challenge to many people like government, police and experts who are working on social networks. Therefore, it is important to put more effort on how to control rumors in social networks and also detection of rumor source to punish them.
2 B. Sharing Abusive Photos/VideosSharing any kind of abusive photo or video of anyone is illegal activity and treated as cyber-crime [6].
3 C. Posting Comments Against Religions, Communities or Country
4 D. Movie Release Online Without Permission.These are other occurring cyber-crimes in social networks but are not limited to these four important cyber-crimes. Whatever it may be, there is a need to prevent them and if anyone has done these, a need to find and punish them. In the next section, a discussion is given about how to detect whether a given data is rumor or fact-based on some classification algorithms.
Rumor is a currently trending topic which contains an unverified content. This content may be either wrong information (misinformation) or intentionally wrong information (disinformation) [31]. Social media is capable of diffusing the information rapidly in the network as these rumors are also disseminated over the network. Some people may not know the difference between rumor and fact and may share the same rumor to other communities.
It is observed that rumors (about politics, religions, communities, etc.) diffuse very fast when compared to normal news. Thus, it is important to stop diffusion of rumors in social media, which requires detecting whether the information is rumor or not. Nowadays, rumor detection becomes a challenging task and many researchers are working on it. How a information can be classified rumor or non-rumor is shown in Figure 1.2.The figure shows how a rumor is classified as true or false and if it is false how it is classified as misinformation or disinformation.
In order to classify whether given data is rumor or not, follow the procedure as shown in Figure 1.3.
Initially, we consider a rumor dataset (messages) from social network. Next, to process the data, data processing is used. After processing, it is required to extract features like user features, Tweet features, and comment features from processed Twitter data as shown in Table 1.2.Later, use any classification algorithm to classify rumors based on these features. Classification models classify and produce results. In order to detect whether a given text is a rumor or not, the most common approach is to simply tokenize the text and apply classification algorithms. There are many classification algorithms that exist, but only few algorithms give better results. They are algorithms like Naïve Bayes, SVM, Neural network with TF, Neural network with Keras, decision tree, random forest, Long Short Term Memory, etc. In this section two major classification algorithms are discussed.
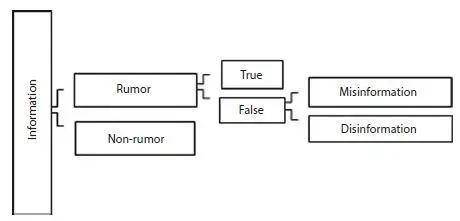
Figure 1.2 Classification of rumor and non-rumor.
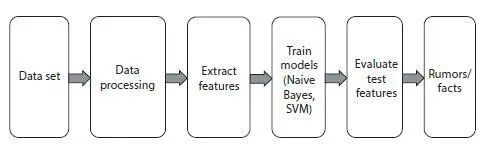
Figure 1.3 Rumor classification process.
1.4.1.1 Naïve Bayes Classifier
In machine learning, Naïve Bayes classification algorithm is a very simple algorithm which is based on a combination of Bayes theorem and naïve assumption. A Naïve Bayes classifier assumes that presence of one feature is unrelated to the other features presented in same class [30]. Generally the assuptions made by Naïve Bayes are not correct in real situations, and even independence assumption never correct, but it works well in practice [29].
Table 1.2 Dataset features [31].
| User features in social networks |
Tweet features in Twitter |
Comments features in social networks |
| No of followers |
No of records |
No of replies |
| No of friends |
No of words |
No of words |
| User has location in his profile |
No of characters |
No of characters |
| User has URL? |
Tweet contains URL? |
Comments contain URL? |
| User is a verified user? |
Source of tweet |
Source of comment |
| Ratio of friends/followers |
Length of tweet |
Length of tweet |
| Age of the user account |
No of hash tags |
No of question mark |
| Ratio of statuses/followers |
No of mentions |
No of pronouns |
| No of pronouns |
No of URLs |
| No of URLs |
No of exclamation mark |
| No of question mark |
Polarity |
| No of exclamation mark |
Presence of colon symbol |
| Polarity |
|
| Presence of colon symbol |
It can be done using the following Bayes theorem,
(1.1) 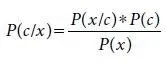
Читать дальше