The problem with Class B networks is that even though they are much smaller than Class A networks, they still allocate far too many host IDs. Very few networks have tens of thousands of hosts. Thus, careless assignment of Class B addresses can lead to a large percentage of the available host addresses being wasted on organizations that don't need them.
In a Class C address, the first three octets are used for the network ID, and the fourth octet is used for the host ID. With only eight bits for the host ID, each Class C network can accommodate only 254 hosts. However, with 24 network ID bits, Class C addresses allow for more than 2 million networks.
The problem with Class C networks is that they’re too small. Although few organizations need the tens of thousands of host addresses provided by a Class B address, many organizations need more than a few hundred. The large discrepancy between Class B networks and Class C networks is what led to the development of subnetting, which I describe in the next section.
Subnetting is a technique that lets network administrators use the 32 bits available in an IP address more efficiently by creating networks that aren’t limited to the scales provided by Class A, B, and C IP addresses. With subnetting, you can create networks with more realistic host limits.
Subnetting provides a more flexible way to designate which portion of an IP address represents the network ID and which portion represents the host ID. With standard IP address classes, only three possible network ID sizes exist: 8 bits for Class A, 16 bits for Class B, and 24 bits for Class C. Subnetting lets you select an arbitrary number of bits to use for the network ID.
Two reasons compel people to use subnetting. The first is to allocate the limited IP address space more efficiently. If the Internet were limited to Class A, B, or C addresses, every network would be allocated 254, 64,000, or 16 million IP addresses for host devices. Although many networks with more than 254 devices exist, few (if any) exist with 64,000, let alone 16 million. Unfortunately, any network with more than 254 devices would need a Class B allocation and probably waste tens of thousands of IP addresses.
The second reason for subnetting is that even if a single organization has thousands of network devices, operating all those devices with the same network ID would slow the network to a crawl. The way TCP/IP works dictates that all the computers with the same network ID must be on the same physical network. The physical network comprises a single broadcast domain, which means that a single network medium must carry all the traffic for the network. For performance reasons, networks are usually segmented into broadcast domains that are smaller than even Class C addresses provide.
A subnet is a network that falls within a Class A, B, or C network. Subnets are created by using one or more of the Class A, B, or C host bits to extend the network ID. Thus, instead of the standard 8-, 16-, or 24-bit network ID, subnets can have network IDs of any length.
Figure 3-3 shows an example of a network before and after subnetting has been applied. In the unsubnetted network, the network has been assigned the Class B address 144.28.0.0. All the devices on this network must share the same broadcast domain.
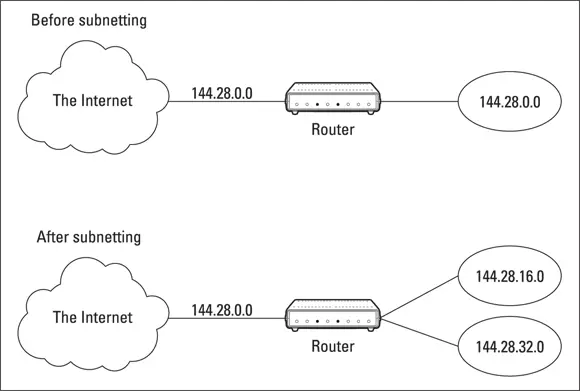
FIGURE 3-3:A network before and after subnetting.
In the second network, the first four bits of the host ID are used to divide the network into two small networks, identified as subnets 16 and 32. To the outside world (that is, on the other side of the router), these two networks still appear to be a single network identified as 144.28.0.0. For example, the outside world considers the device at 144.28.16.22 to belong to the 144.28.0.0 network. As a result, a packet sent to this device will be delivered to the router at 144.28.0.0. The router then considers the subnet portion of the host ID to decide whether to route the packet to subnet 16 or subnet 32.
For subnetting to work, the router must be told which portion of the host ID should be used for the subnet network ID. This little sleight of hand is accomplished by using another 32-bit number, known as a subnet mask. Those IP address bits that represent the network ID are represented by a 1 in the mask, and those bits that represent the host ID appear as a 0 in the mask. As a result, a subnet mask always has a consecutive string of ones on the left, followed by a string of zeros.
For example, the subnet mask for the subnet shown in Figure 3-3, where the network ID consists of the 16-bit network ID plus an additional 4-bit subnet ID, would look like this:
11111111 11111111 11110000 00000000
In other words, the first 20 bits are ones, and the remaining 12 bits are zeros. Thus, the complete network ID is 20 bits in length, and the actual host ID portion of the subnetted address is 12 bits in length.
To determine the network ID of an IP address, the router must have both the IP address and the subnet mask. The router then performs a bitwise operation called a logical AND on the IP address in order to extract the network ID. To perform a logical AND, each bit in the IP address is compared with the corresponding bit in the subnet mask. If both bits are 1, the resulting bit in the network ID is set to 1. If either of the bits are 0, the resulting bit is set to 0.
For example, here’s how the network address is extracted from an IP address using the 20-bit subnet mask from the previous example:
IP address: 10010000 00011100 00010000 00010001 (144.28.16.17)Subnet mask: 11111111 11111111 11110000 00000000Network ID: 10010000 00011100 00010000 00000000 (144.28.16.0)
Thus, the network ID for this subnet is 144.28.16.0.
The subnet mask itself is usually represented in dotted-decimal notation. As a result, the 20-bit subnet mask used in the previous example would be represented as 255.255.240.0:
Subnet mask: 11111111 11111111 11110000 00000000 255 . 255 . 240 . 0
Don’t confuse a subnet mask with an IP address. A subnet mask doesn’t represent any device or network on the Internet. It’s just a way of indicating which portion of an IP address should be used to determine the network ID.
Note that a subnet mask cannot be an arbitrary collection of octets. Instead, a subnet mask always has a certain number of binary 1s on its left side, and the remaining bits of the mask are always 0. This limits the dotted-decimal representation of a subnet mask to certain values.
 You can spot a subnet mask right away because the first octet is always 255, and 255 is not a valid first octet for any class of IP address.
You can spot a subnet mask right away because the first octet is always 255, and 255 is not a valid first octet for any class of IP address.
Because a subnet mask always begins with a consecutive sequence of ones to indicate which bits to use for the network ID, you can use a shorthand notation — a network prefix — to indicate how many bits of an IP address represent the network ID. The network prefix is indicated with a slash immediately after the IP address, followed by the number of network ID bits to use. For example, the IP address 144.28.16.17 with the subnet mask 255.255.240.0 can be represented as 144.28.16.17/20 because the subnet mask 255.255.240.0 has 20 network ID bits.
Читать дальше


 You can spot a subnet mask right away because the first octet is always 255, and 255 is not a valid first octet for any class of IP address.
You can spot a subnet mask right away because the first octet is always 255, and 255 is not a valid first octet for any class of IP address.










