The following sections describe a few of the other features commonly provided by routers.
Network address translation
When a router is used to connect a private network to the Internet, one of the router’s most important functions is routing traffic from all the computers on the private side of the router to the public side, which usually has just a single public IP address. To accomplish this magic, the router uses network address translation (NAT).
In short, when a computer on the private side of the network sends a packet through the router to the Internet, the router substitutes its own public IP address as the sender address, and keeps track of the fact that it sent a packet on behalf of a computer on the private side. When the recipient on the Internet receives the packet, it sees that the sender was the router. It then sends a response back to the router, which then substitutes the original sender’s private IP address for the destination address and forwards the packet to the correct computer on the private network.
For more information about NAT, see Book 2, Chapter 3.
A virtual private network (VPN) is a secure connection between two private networks over a public network (in other words, over the Internet). All the data that flows over the VPN is encrypted, so anyone who steals packets from the VPN will find them unintelligible; only the parties on either end of the VPN are able to decrypt the packets.
VPN connections are often called tunnels, because they provide an isolated pathway from one point to another through the Internet. The only way to gain meaningful access to a VPN tunnel is at either end.
There are two common uses for VPNs:
To provide remote workers with secure access to your company network: To do that, you set up a VPN on the router, and then provide your remote workers with the credentials necessary to access the VPN. The remote workers can run a software VPN client on their home computers or laptops to connect to your company network.
To establish a tunnel directly between routers on two networks that are separated geographically: For example, suppose you have offices in Los Angeles and Las Vegas. You can use routers on both networks to establish a VPN tunnel between them. This effectively joins the networks together, so that devices on the Los Angeles network can freely exchange packets with devices on the Las Vegas network, and vice versa.
Figure 3-4 shows this arrangement. As you can see, the routers in both Los Angeles and Las Vegas are connected through the Internet via a VPN tunnel. This tunnel enables computers in Los Angeles and Las Vegas to communicate freely and securely with each other.
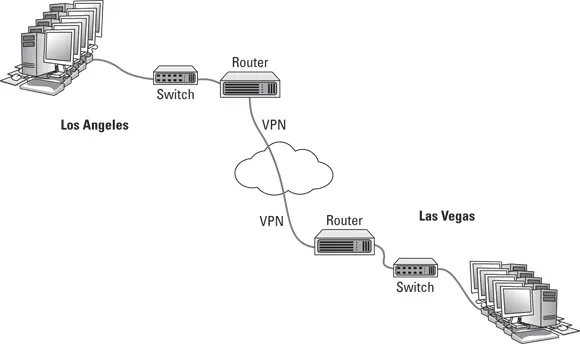
FIGURE 3-4:Connecting offices with a VPN tunnel.
For more information about working with VPN tunnels, refer to Book 4, Chapter 6.
The final topic for this whirlwind introduction to switches and routers is the concept of VLANs. Most advanced switches allow you to create VLANs.
As its name suggests, a VLAN is a virtual network that runs on top of your actual physical network. VLANs work at layer 2 of the OSI model, which means that they’re related MAC addresses, not IP addresses. That said, there is usually a direct correlation between VLANs and IP subnets. If (or when) your network grows large enough that you want to set up two or more subnets to better manage it, you’ll probably also want to set up two or more VLANs, one for each of your subnets.
A VLAN can divide a single switch into two virtual switches that behave exactly as if they were separate switches. This means the following:
If a port on one VLAN receives a packet intended for a destination on the same VLAN, the switch forwards the packet to the destination port, the same as if VLANs were not in use.
When a port on one VLAN receives a packet intended for a destination on the same VLAN that the switch has not yet learned, the switch will flood only those ports that are on the destination VLAN — not all the ports on the switch. Thus, VLANs can reduce traffic caused by flooding.
When a broadcast packet is received, the switch will forward the packet only to those ports that are on the same VLAN. In other words, VLANs can break up broadcast domains in the same way that a router can.
If a port on one VLAN receives a packet intended for a different VLAN, a router is required to link the networks. That’s because separate VLANs are, for all intents and purposes, separate networks.That being said, most switches that support VLANs also support trunk ports, which can switch traffic between VLANs. A trunk port is a port that can handle traffic for two or more VLANs.
To use VLANs, you must manually configure each port of your switches to operate on the appropriate VLAN. By default, all switches regardless of manufacturer are configured out of the box so that all ports operate on a VLAN named VLAN1. To create a new VLAN, you simply create a name for the new VLAN, and then configure the ports that will talk on the new VLAN.
In VLAN terminology, a port that is configured to operate on a single VLAN is called an access port. Ports that are configured to work on more than one VLAN are called trunk ports. By default, all switch ports are configured as access ports on VLAN1.
Note that if you have more than one switch in your network, you can configure VLANs to work across the switches. For example, you can create a VLAN for your company’s accounting department — let’s call it VLAN-Acct. Then you can configure ports on any of your switches as access ports on VLAN-Acct. In this way, your entire accounting staff can operate on the accounting VLAN.
Chapter 4
IN THIS CHAPTER
 Assessing the risk for security
Assessing the risk for security
 Looking at two pillars of cybersecurity
Looking at two pillars of cybersecurity
 Identifying the most important protection and recovery measures
Identifying the most important protection and recovery measures
 Examining standardized cybersecurity frameworks
Examining standardized cybersecurity frameworks
 Looking closer at the NIST Cybersecurity Framework
Looking closer at the NIST Cybersecurity Framework
As an IT professional, cybersecurity is the thing most likely to keep you awake at night. Consider the following scenarios:
Your phone starts ringing like crazy at 3 o’clock one afternoon because no one anywhere on the network can access any of their files. You soon discover that your network has been infiltrated by ransomware, nefarious software that has encrypted every byte of data on your network, rendering it useless to your users until you pay a ransom to recover the data.
Your company becomes a headline on CNN because a security breach has resulted in the theft of your customers’ credit card information.
On his last day of work, a disgruntled employee copies your company contact list and other vital intellectual property to a flash drive and walks away with it along with his red Swingline stapler. A few months later, your company loses its biggest contract to the company where this jerk now works.
Читать дальше


 Assessing the risk for security
Assessing the risk for security










