Table 2.1 Network forensics architecture conceptual block of the model.
| Name of network forensics process-layer |
Task description |
| The Control Manager |
Manage cloud infrastructure;An interface configures and controls the forensics process;Authorize forensics request;Target cloud users VMs;Delegate to a third party. |
| Data Collection/Collection of Data |
Execute on the local VM;Monitor physical host;Collect network traffic at the VMM level;For an update, dynamically reconfigure;Start/stop data collection. |
| Separation/Filtration |
Filtering data individual cloud user;Investigate distinct nodes on the particular physical host;All forensics investigations independently investigated;Separate datasets to a single cloud user;Filtering and reduce the network traffic size;Monitor specifically cloud users;The proposed architecture uses VMs lookup table;Filtering ID, Mac addresses for further investigation. |
| Accumulator/Aggregation |
Filtration process-layer provides data;Collect data;Capture from the several locations;Combine data. |
| Analyzation |
Potentially support multiple possibilities;Transfer the accumulator layer output to the investigator;A user of the cloud deploy analysis as a cloud service;Run analysis on the cloud. |
| Documentation |
Produce a report on the basis of analysis results;Presentation of analysis outcomes. |
In this section, we have implemented the model of the prototype architecture described in section 2.2. In the implementation phase, we extend some crucial components that are usable for network forensics investigation on the cloud environment; the prototype implementation of the proposed architecture assumption are as follows:
An account of individual cloud user VMs managed by CSP;
Cloud users able to run/stop the process of data collection for forensics investigation;
Monitor the VMs for cloud security perspective and also ensure the M2M secure communication;
Inside the cloud, a web-based system created and used to analyze the collected data.
In this chapter, we clarify that the users are able to work with the VMs, to change their status individual and also monitor the overall activity parameters of VMs. Our proposed architecture slightly extends the software management for control of network forensics by adding some application programming interface. Using OpenNebula [34, 35], an open-source active community-based cloud management system, it supports more distinct and independent VMMs products. The main objective is to create an interface of analysis tool to capture malicious threats that run as a service in the users’ cloud VMs. In this scenario, NetworkMiner [36] an open-source network forensics analysis framework, helps to analyze collected forensics data within the cloud [38]. The next couple of sections briefly elaborate on the complete mechanism of the OpenNebula and NetworkMiner analysis tool.
2.3.1 OpenNebula (Hypervisor) Implementation Platform
In the model architecture, the control manager is the add-on extension of the OpenNebula application programming interface (shown in Figure 2.2) that we already discussed in section 2.3. The cloud user request to the control manager for accessing on-demand VMs for the different physical host, the control manager instance OpenNebula can manage users request regarding cloud storage, networks, and software services.
The authentication gives the user access to VMs within the cloud [37]. All the physical hosts share multiple virtual machines, and these machines monitor by virtual machine monitors (VMM). OpenNebula perform overall management of a cloud system; it helps the network investigator to analyse forensically captured data of vulnerabilities, risk, cyber-threats, and malicious attacks on cloud network environment for further investigations.
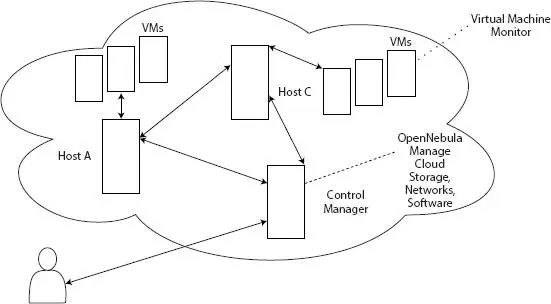
Figure 2.2 OpenNebula: a community-based cloud management system that manages resources of the cloud physical host, VMs, VMM, control access, and authentication between cloud users.
2.3.2 NetworkMiner Analysis Tool
NetworkMiner analysis is an open-source network forensics analysis tool that aims to collect malicious attacks or threats over the cloud; these things help in the forensics investigation. In the implementation phase, cloud user direct data collection and separation or filtration layer, where it can start/ stop/reset cloud VMs that running as a forensics service.
The collaboration of the layers performs both the tasks, for example, VMM and network forensics task. NetworkMiner received collected data from OpenNebula and then run accumulator and analysis forensics process-layer as a cloud-based service for aggregate as well as analyze provided captured data. The documentation layer performs visualization of the analysis output. Our modified has additional forensics components (shown in Figure 2.3) that ensure safe machine communication and also help for further investigation.
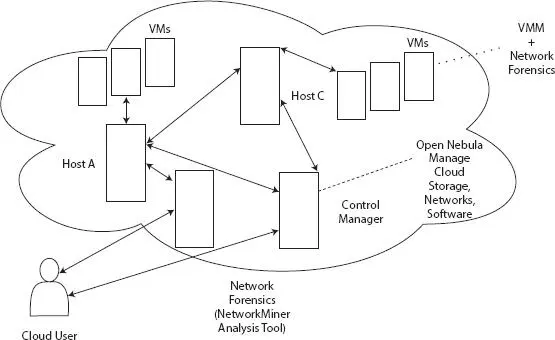
Figure 2.3 NetworkMiner analysis tool cloud-based forensics services.
The actual cloud environment provided by OpenNebula and Network Miner is as under:
The first is to start data collection, trigger to start the forensics process on the cloud network;
Next is stop data collection, trigger to stop the network forensics process;
Virtual machine identity (VM-ID) used by OpenNebula for setting the action parameter of an individual virtual machine;
OpenNebula translating VM-ID into MAC network address;
Filtering the MAC address;
Help to capture the PCAP file (Package capture file) used for tackle network traffic;
An additional component of network forensics Network Miner analysis tool manages the entire VMs analysis (VMM); the main task is to collect, separate, accumulate, and analyze data for proper communication;
The control manager triggers the overall system action.
In the next section, we calculate the performance matrix of OpenNebula and NetworkMiner, and also compare both the accuracy and efficiency of the tools to the other well-known network forensics tools.
2.3.3 Performance Matrix Evaluation & Result Discussion
Performance evaluation of the proposed architecture is to verify our network forensics cloud-based system performs well enough as compared to the previously published model. The setup of measuring the performance impact on the running VMM manages all VMs in the cloud environment with network forensics. The process consumes computational and power resources to evaluate the model performance, communicate resources that would capture, aggregate and analyse, and transfer network traffic.
In the experiment, the proposed model architecture intended to quantify the performance matrix by comparing both the scenarios: (i) without network forensics and (ii) with network forensics (shown in Figure 2.4).
The performance measurement was done by setting the tune of the host system, as well as mention the crucial software specification of the hosts, described below:
System Software: Linux Ubuntu 18.04;
Application Software: OpenNebula and NetworkMiner;
System Specification: x64 2.4GHz Octa-Core 7th Generation CPU with 32GB RAM connected via highly powerful ether-net connectivity up to Gigabit.
Читать дальше














