2.1.3.1 Infrastructure-as-a-Service (IaaS)
Infrastructure-as-a-Service (IaaS) is one of the types of cloud service models, the computing infrastructure that manages the overall cloud services over the internet. On-demand quickly scales up and down infrastructure services [21], working on the mechanism like a pay-as-you-go platform where cloud users pay only for what they use. This avoids the expense of buying additional physical IT-infrastructure and managed complex server and other data center resources. In a cloud environment, IaaS offers resources as an individual service component, cloud service provider [22] manages the IT-resources in a virtualized environment, and the users can focus only on installation, configuration, and software maintenance. The cloud service providers enable users to elastically utilize virtual server and storage resources by a pay-per-use method, forming networks that tie them all together [23]. By renting IaaS from a cloud service provider, essentially, cloud users not only have on-demand hardware services but also provisioning software services that automate it.
2.1.3.2 Challenges of Cloud Security in Fourth Industrial Revolution
The IT revolution has brought an important transformation in the industrial manufacturing processes with high impact [27]; this envelopment promotes the latest technology trends such as cloud-based systems, Internet of Things (IoT), Big Data Analysis, and others in the fourth industrial revolution. However, new innovative solutions carry challenges and limitations, such as unexpected risk, security vulnerabilities, infringing privacy, and many more [24]. Increased reliance on innovations may gain a competitive advantage [25], but on a certain note, security issues have been one of the most insignificant challengeable aspects for conducting successful business communication and transaction between machines on the cloud platform [26]. This chapter, highlighting the reflections and emphasizing the security issues and limitations of industry 4.0, raises awareness towards good security practice within the fourth industrial revolution:
Inadequate Access Management
Multi-tenancy
Data Loss
Data Breaches
Infringing Privacy
Cost of Transferring
The chapter is structured as follows. The next section presents the generic model architecture for network forensics and cloud security issue in the industry 4.0 application. Section 2.3discusses the model implementation, implementation platform used, such as Open Nebula and Network Miner for analysis of security threats. Section 2.4focuses on the machine-to-machine communication impact on industrial 4.0 applications, and also describes an application scenario of cloud computing security in the domain of industry 4.0. Finally, we conclude our chapter in Section 2.5.
2.2 Generic Model Architecture
This chapter considers cloud-based IT infrastructure in which a cloud service provider (CSP) executes virtual machine (VM) [28], cloud users get full control over the services like software, running on the VM, and these VMs are managed by the virtual machine monitor (VMM) [28]. CSP manages the physical machine with the help of hypervisor and provides resources on-demand to the cloud users [29]; the users have no right to access them directly. Multiple cloud users can share the same infrastructure or IT resources. In the event of malicious attacks, users’ virtual machines can easily be compromised.
The proposed architecture performs as the autonomous authorized third party of network forensics investigation, which forensically investigates cloud-based virtual resources (such as security threats as well as data acquisition, multi-tenant, and infringing privacy) with the support provided by CSP. The factor which we assume here is that we can only trust the cloud provider and the IT infrastructure, whereas cloud users’ VMs are untrusted. However, the behavior of a virtual machine needs to be modified for secure M2M communication; a malicious attacker manipulates data (gains access to the user’s virtual machine). Therefore, we do not collect forensics data while the process is running on the user virtual machine rather than apply forensics investigation directly. The virtualized cloud infrastructure guarantees virtual machine isolation [28]; it is completely clear that the attacker does not access other VMs itself or VMM running on the same physical host.
Several types of research have been published that relate the situation of the trust in the cloud infrastructure, justified through a technical mechanism. Susan F. Crowell says [30] regarding the VMs trust, for virtual machine trust isolation in an IaaS cloud environment, embodiments of the invention monitor level of suspicious activities on the particular virtual machine using embedded node agents. Crowell addresses the critical problems of VMs over the cloud, for example, to create a trustworthy cloud infrastructure by designing a security audit system: verify clients’ data confidentiality and integrity [32], measure virtual machines root-of-trust [31], enforce by a technical mechanism not only by Service Level Agreements (SLAs) contracts.
In this chapter, we present a model for network forensics to investigate security threats (malicious attacks) when machines communicate with each other in a cloud environment. The forensics process model (shown in Figure 2.1) depends on five process-layers that interact with the control manager, and the adaptation of the process-layers from the flow of the process of the NIST network forensics model [33]. The process-layers perform independent tasks regarding the incident investigation of cloud computing security issues. The investigational tasks execute a parallel and distributed manner in a multitenant environment. We already discussed the multitenancy in the above section 2.1.3.2.
In this section, we describe the purpose of an individual process-layer; the first process-layer is the collection of data or data collection layer, in which overall data is captured. The control manager interacts with the data collection and decides when to start or stop the data capturing process. The data collection coordinates with the migration of VM in the cloud environment and the control manager simultaneously collects data traffic of VM migration. On the next process-layer is the separation or filtration; the actual task of the process-layer is to filter captured data by cloud user. The main advantage is that each set of data maintains data accordingly to the single cloud users. Additionally, separation can compress user-specific collected data; reduce the size, and filtering forensically network data traffic.
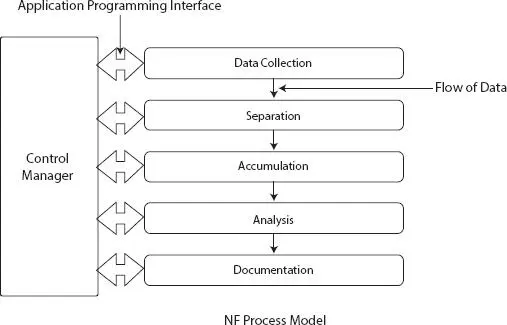
Figure 2.1 Network forensics process model for cloud investigation.
In the third process-layer, the accumulator or aggregate layer deals with the adds data from multiple sources of a single cloud user. The cloud user utilizes resources from distinct physical locations such as load balancing then the accumulator collects all data from multiple source location. Furthermore, this layer helps to collaborate with all the network data into a single set. The fourth layer is data analysis, analysis of the preprocessed data set for the detailed investigation. The control manager configures the complete transmission from data capture to the accumulation layer, analysis process-layer is run as a cloud service in the cloud environment. The last process-layer is documentation, which presents the analysis results and consequence to tackle the entire security threats.
The proposed forensics network architecture for secure machine communication translates the conceptual blocks of separate services as described in Table 2.1.
Читать дальше













