Evaluate almost 8 VMs parallel with network forensics on a single virtual machine monitor, VMs hosts a web-based service interface that runs tasks as a computationally intensive. This web-based service interface calculates both the great common divers, for example, with or without network forensics, output results show in Figure 2.4. Iteratively calculate the request of cloud users to call a function over several times. Moreover, users’ web services and NetworkMiner analysis run a separate interface.
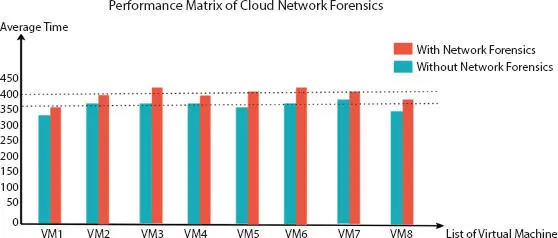
Figure 2.4 Measurement of the performance of network forensics while running cloud infrastructure systems.
Call Function: More than 2,800 times with minimum 20 concurrent requests;
The time it takes to calculate the call function of cloud users is less than 2 minutes;
The average performance of VMs is almost 89%;
Average performance reduction between 3% to 18%.
Recently, cloud service provides offered Forensics-as-a-Service. Similar to the other cloud services, FaaS is a business service model for digital investigators. One is the addition of cloud resources for the analysis of forensics data by cloud users, and the second is the most prominent aspect that, not account for VMM plus network forensics cloud-based system. Estimate the sets of forensics transferred data to the accumulator that aggregate and then the analyzation process-layer.
In the next section, we have taken a real-world scenario of cloud security impact on M2M communication and how we can utilize the cloud application in the fourth industrial revolution.
2.4 Cloud Security Impact on M2M Communication
For an authorized and secure communication channel an autonomous system is required [38], many parts of a system where a machine can communicate with others, such as (i) daemon to backend, (ii) service to service, (iii) IoT tools, and (iv) CLI (client to internet service). Establishing an authorized trust system between client [39], means authorization process attempts to build trust in the cloud environment by authorizing a client. In this case, a cloud client can simply utilize cloud applications, services, and securely processes cloud infrastructure. There is no need to typically authenticate like username/password, two-way authentication, social login, and others. However, provide protected, and secure machines communication, cloud client grant credentials, this credential has two pieces of information, one is the client ID, and the second is secret. This piece of information can request access for secured resources. The cloud-based services access mechanism of secure M2M communication are as under:
The cloud client request to the authorizing server by sending the client ID and secret along with the audience, get access to cloud infrastructure (access distinct virtual machine);
The authorized server validate request (if successful);
Send response by giving the access token;
By providing the access token, cloud users request secured resources from the server.
In this chapter, we have proposed our architecture on the basis of daemon to backend secure communication channel for machines.
2.4.1 Cloud Computing Security Application in the Fourth Industrial Revolution (4.0)
The fourth industrial revolution is the transformation of industrial and manufacturing products, introducing the new stages in the organization, valuing creation processes, and controlling the organizational value chain. Cloud computing (CC) is one of the biggest aspects to boost manufacturing products. CC brought about a remarkable overhaul of the enterprise’s phenomena, a significant investment to establish IT infrastructure. In almost every business, CC benefits in many ways. The most prominent features are the flexibility to pay for resources, 24/7 availability, on-demand means resource elasticity, based on need only. Moreover, when it comes to Infrastructure-as-a-Service (IaaS), an existing infrastructure on the pay-as-you-go platform, an obvious choice for enterprises saving on the cost of investment to acquire, control, available, manage, and maintain server all the time. Infrastructure becomes a commodity; the majority of businesses use the services of the cloud to enhance the manufacturing productions, whether or not they know about the cloud.
To show the advantage of cloud computing in industry 4.0, we have adopted the real-world scenario to make the concept clear. Consider your business has multiple locations, you might have trouble connecting the team, and trying to collaborate on the same project, because of the distance between them. The same issue arises when your employees work remotely. The thing is how we can tackle the situation; cloud collaboration tools allow your people to access the same project and connect several people remotely in a single go. Accessing the real-time project reduces time and money and has many advantages: the ability to upload documents and send via email remotely; decreasing the time for updating; easy to monitor and get updates on the project completion; enhancing communication, reducing cost, and increasing productivity.
Consider another aspect: your company rapidly grows, but you do not have a way to scale your infrastructure. With the rapid enhancement of organizational production growth, you want to hire employees, but you do not have an idea of when and how large it will become. When you purchase convectional internal infrastructure, and potentially you want employees to maintain, that will increase the cost of purchases and hiring employees. In this situation, the cloud is the better solution; no matter how quickly you grow, cloud service provider simply provides scale on-demand IT infrastructure as per need and pay for what you used. The prominent feature in this scenario is protected machine communication; it is a trustable remote service; it provides a secure channel to access IT resources; you can rely on it.
The rapid growth of cloud computing, especially the use of cloud-based IT infrastructure in recent years, creates new challenges for network investigators. Essential means for remote prevention in the cloud-based industry 4.0 environment, tackle the security threats between machine communications that enhance the need of forensics in the cloud. In a cloud environment, it is hard to determine the location of virtual resources, which may change even a certain time frame. Network forensics needs to be limited in a multitenant environment, the reason behind the specific system under observation. We have analyzed the critical problems with a specific concentration on forensics for the cloud service models, and proposed a generic model for secure communication between M2M in a cloud-based environment. For the sake of prevention, we developed a system architecture and integrated implementation of network forensics modules that identify security challenges and its impact on the fourth industrial revolution application, with the support of the OpenNebula cloud management infrastructure. The security issues that our method solved are: First, facilitate cloud users by providing a mechanism of remote network forensics for data acquisition, processes, and monitor means overall control the physical location of virtual resources independently. Second, another limitation in cloud computing that is infringing privacy and security; the proposed approach ensures the separation of cloud users in a multitenant environment. The last is to remove the cost of transferring network collected data, impalement external investigation tools that analyze and control internal cloud services by network investigators. This contribution eliminates the disadvantages of traditional cloud-based services that run locally on the internal infrastructure of the industry.
Читать дальше













