Mark Stamp - Information Security
Здесь есть возможность читать онлайн «Mark Stamp - Information Security» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Information Security
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:3 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 60
- 1
- 2
- 3
- 4
- 5
Information Security: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Information Security»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Provides systematic guidance on meeting the information security challenges of the 21st century, featuring newly revised material throughout Information Security: Principles and Practice
Information Security
Information Security: Principles and Practice, Third Edition
Information Security — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Information Security», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
Table of Contents
1 Cover
2 Title Page Information Security Principles and Practice Third Edition Mark Stamp San Jose State University San Joe, California
3 Copyright
4 Dedication
5 Preface
6 About the Authorcontributors Note
7 Acknowledgments
8 Chapter 1: Introductions 1.1 The Cast of Characters 1.2 Alice's Online Bank 1.3 About This Book 1.4 The People Problem 1.5 Principles and Practice 1.6 Problems Notes
9 Part I: Crypto Chapter 2: Classic Crypto 2.1 Introduction 2.2 How to Speak Crypto 2.3 Classic Ciphers 2.4 Classic Crypto in History 2.5 Modern Crypto History 2.6 A Taxonomy of Cryptography 2.7 A Taxonomy of Cryptanalysis 2.8 Summary 2.9 Problems Notes Chapter 3: Symmetric Ciphers 3.1 Introduction 3.2 Stream Ciphers 3.3 Block Ciphers 3.4 Integrity 3.5 Quantum Computers and Symmetric Crypto 3.6 Summary 3.7 Problems Notes Chapter 4: Public Key Crypto 4.1 Introduction 4.2 Knapsack 4.3 RSA 4.4 Diffie–Hellman 4.5 Elliptic Curve Cryptography 4.6 Public Key Notation 4.7 Uses for Public Key Crypto 4.8 Certificates and PKI 4.9 Quantum Computers and Public Key 4.10 Summary 4.11 Problems Notes Chapter 5: Crypto Hash Functions++ 5.1 Introduction 5.2 What is a Cryptographic Hash Function? 5.3 The Birthday Problem 5.4 A Birthday Attack 5.5 Non‐Cryptographic Hashes 5.6 SHA‐3 5.7 HMAC 5.8 Cryptographic Hash Applications 5.9 Miscellaneous Crypto‐Related Topics 5.10 Summary 5.11 Problems Notes
10 Part II: Access Control Chapter 6: Authentication 6.1 Introduction 6.2 Authentication Methods 6.3 Passwords 6.4 Biometrics 6.5 Something You Have 6.6 Two‐Factor Authentication 6.7 Single Sign‐On and Web Cookies 6.8 Summary 6.9 Problems Notes Chapter 7: Authorization 7.1 Introduction 7.2 A Brief History of Authorization 7.3 Access Control Matrix 7.4 Multilevel Security Models 7.5 Covert Channels 7.6 Inference Control 7.7 CAPTCHA 7.8 Summary 7.9 Problems Notes
11 Part III: Topics in Network Security Chapter 8: Network Security Basics 8.1 Introduction 8.2 Networking Basics 8.3 Cross‐Site Scripting Attacks 8.4 Firewalls 8.5 Intrusion Detection Systems 8.6 Summary 8.7 Problems Notes Chapter 9: Simple Authentication Protocols 9.1 Introduction 9.2 Simple Security Protocols 9.3 Authentication Protocols 9.4 “Authentication” and TCP 9.5 Zero Knowledge Proofs 9.6 Tips for Analyzing Protocols 9.7 Summary 9.8 Problems Notes Chapter 10: Real‐World Security Protocols 10.1 Introduction 10.2 SSH 10.3 SSL 10.4 IPsec 10.5 Kerberos 10.6 WEP 10.7 GSM 10.8 Summary 10.9 Problems Notes
12 Part IV: Software Chapter 11: Software Flaws and Malware 11.1 Introduction 11.2 Software Flaws 11.3 Malware 11.4 Miscellaneous Software‐Based Attacks 11.5 Summary 11.6 Problems Notes Chapter 12: Insecurity in Software 12.1 Introduction 12.2 Software Reverse Engineering 12.3 Software Development 12.4 Summary 12.5 Problems Notes
13 Appendix A‐1 Modular Arithmetic A‐2 Permutations A‐3 Probability A‐4 DES Permutations
14 Bibliography
15 Index
16 End User License Agreement
List of Tables
1 Chapter 2 Table 2.1 Abbreviated alphabet Table 2.2 Election of 1876 codebook Table 2.3 Excerpt from a German codebook Table 2.4VENONA decrypt of message of 21 September 1944
2 Chapter 3 Table 3.1 RC4 initialization Table 3.2 RC4 keystream byte Table 3.3 DES S‐box 1 (in hexadecimal) Table 3.4 DES key schedule algorithm Table 3.5 AES ByteSub Table 3.6 TEA encryption Table 3.7 TEA decryption
3 Chapter 4Table 4.1 Addition on an elliptic curve 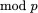
4 Chapter 5Table 5.1 Steps in round  of SHA‐3Table 5.2 Simple steganography example
of SHA‐3Table 5.2 Simple steganography example
5 Chapter 6Table 6.1 Iris scan distance and fraud rateTable 6.2 Biometric equal error rates [121]
6 Chapter 7Table 7.1 Access control matrixTable 7.2 Access control matrix for confused deputy example
7 Chapter 8Table 8.1 Spoofed email in SMTPTable 8.2 Example ACLTable 8.3 Aliceś initial file access ratesTable 8.4 Aliceś recent file access ratesTable 8.5 Aliceś updated file access ratesTable 8.6 Aliceś more recent file access ratesTable 8.7 Aliceś second updated access rates
8 Chapter 11Table 11.1 Approximate lines of codeTable 11.2 A flawed programTable 11.3 Code exampleTable 11.4 Disassembled serial number programTable 11.5 Source code for serial number exampleTable 11.6 Serial number program
9 Chapter 12Table 12.1 Example Java programTable 12.2 Decompiled Java programTable 12.3 Serial number program disassemblyTable 12.4 Hex view of serial.exeTable 12.5 Hex view of original and patchedTable 12.6 Disassembly of patched serial number program
List of Illustrations
1 Chapter 1 Figure 1.1 The main actors
2 Chapter 2 Figure 2.1 Crypto as a black box Figure 2.2 English letter relative frequencies Figure 2.3 Frequency counts for ciphertext in 2.2 Figure 2.4 Reproduction of the Zimmermann Telegram Figure 2.5 Enigma wiring diagram
3 Chapter 3 Figure 3.1 A5 /1 keystream generator Figure 3.2 One round of DES Figure 3.3 Alice hates ECB mode Figure 3.4 Alice loves CBC mode
4 Chapter 4Figure 4.1 Diffie–Hellman key exchangeFigure 4.2 Diffie–Hellman man‐in‐the‐middle attackFigure 4.3 Graph of the elliptic curve 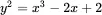 Figure 4.4 Point addition on an elliptic curveFigure 4.5 Hybrid cryptosystemFigure 4.6 Pitfall of sign and encryptFigure 4.7 Pitfall of encrypt and sign
Figure 4.4 Point addition on an elliptic curveFigure 4.5 Hybrid cryptosystemFigure 4.6 Pitfall of sign and encryptFigure 4.7 Pitfall of encrypt and sign
5 Chapter 5Figure 5.1 A better way to signFigure 5.2 SHA‐3 “sponge”Figure 5.3 SHA‐3 state 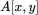 (a
(a  array of 64‐bit words)Figure 5.4 Example ledgerFigure 5.5 Signed ledger entriesFigure 5.6 Numbered and signed ledger entriesFigure 5.7 Invalid entry in a ledgerFigure 5.8 Block
array of 64‐bit words)Figure 5.4 Example ledgerFigure 5.5 Signed ledger entriesFigure 5.6 Numbered and signed ledger entriesFigure 5.7 Invalid entry in a ledgerFigure 5.8 Block 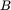 and
and 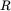 with
with 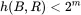 Figure 5.9 Part of a blockchainFigure 5.10 Secret sharing schemesFigure 5.11 Pixel sharesFigure 5.12 Alice's share, Bob's share, and overlay imageFigure 5.13 Texas hold ’em pokerFigure 5.14 A tale of two Alices
Figure 5.9 Part of a blockchainFigure 5.10 Secret sharing schemesFigure 5.11 Pixel sharesFigure 5.12 Alice's share, Bob's share, and overlay imageFigure 5.13 Texas hold ’em pokerFigure 5.14 A tale of two Alices
6 Chapter 6Figure 6.1 Examples of Galton's minutiaFigure 6.2 Extracting minutiaFigure 6.3 An iris in search of a scannerFigure 6.4 Histogram of iris scan resultsFigure 6.5 Smartphone for authentication
7 Chapter 7Figure 7.1 ACLs versus capabilitiesFigure 7.2 Confused deputyFigure 7.3 BLP versus BibaFigure 7.4 Compartments exampleFigure 7.5 Covert channel exampleFigure 7.6 Covert channel using TCP sequence numberFigure 7.7 CAPTCHA example
8 Chapter 8Figure 8.1 A computer networkFigure 8.2 Layering in actionFigure 8.3 TCP headerFigure 8.4 TCP three‐way handshakeFigure 8.5 IP headerFigure 8.6 ARP cache poisoningFigure 8.7 Big picture of the role of a firewallFigure 8.8 Purview of a packet filterFigure 8.9 TCP ACK scanFigure 8.10 Purview of a stateful packet filterFigure 8.11 Purview of an application proxyFigure 8.12 FirewalkFigure 8.13 Defense in depth
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Information Security»
Представляем Вашему вниманию похожие книги на «Information Security» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Information Security» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.











