| Our experiment |
Gold Set |
|
|
Positive (+) |
Negative (−) |
|
Positive (+) |
T_Pos |
F_Pos |
|
Negative (−) |
F_Neg |
T_Neg |
The performance of the method has been validated using various statistical measurements & metrices. For details, please refer to Table 2.3. The visual representation of the method's performance has also been depicted in Figure 2.13.
In our experiment, the value of t-pos = 14, F_pos = 5, F_Neg = 5, and T_neg = 418. Performance of our method using various metrices.
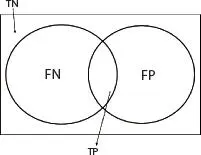
Figure 2.12 Concepts of type-I and type-II error in terms set.
Table 2.3Performance of the method using various metrices.
| Parameter |
Value |
| Sensitivity |
0.736 |
| True negative rate |
0.976 |
| Precision |
0.736 |
| Negative-predictive value |
0.163 |
| Miss rate |
0.263 |
| Fall out |
0.011 |
| False discovery rate |
0.357 |
| False omission rate |
0.011 |
| Threat score |
0.583 |
| Prevalence threshold |
0.149 |
| Accuracy |
0.977 |
| Balance accuracy |
0.856 |
| Matthews correlation coefficient |
0.725 |
| Fowlkes-Mallows index |
0.736 |
| Informedness or bookmarker informedness |
0.712 |
| Markedness |
−0.101 |
| F-score |
0.736 |
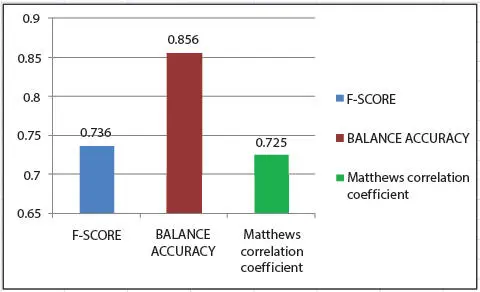
Figure 2.13 Performance measurements of the F-score, balance accuracy, and Matthews correlation coefficient.
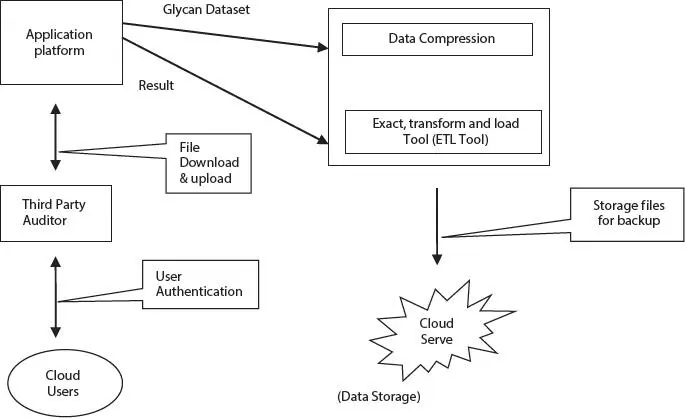
Figure 2.14 Block diagram of glycan cloud.
There are two types of data sets stored in the cloud, namely, glycan dataset and result data. In Figure 2.14, dataset can be stored either. Dataset can be stored either in the form of files or in form of blocks in the cloud. Accessing the cloud is based on internet or intranet. To store the glycan dataset in the cloud storage system, one can move to any location that supports internet access. To save and recover the information, it is not essential to carry physical storage device or use the same computing systems. In this cloud system, security is also a major issue. When data will be stored securely in the cloud, security measures will be followed by authentication, encryption, tokens, and data replication. Authentication is the key security features where authorized user can access this glycan dataset stored in the cloud storage. Dataset of glycan and generated data should be encrypted first and store in the cloud. Only authorized user should know about the decryption key to access the dataset and final resulting framework. Tokens are generated by the third party auditor to check all data set and certify that whether the resultant information is corrupted or not. Hence, the data compression is used to speed up file transfer and decrease the cost of storage hardware, whereas the Exact, Transpose, and Load tool (ETL tool) is used to avoid redundancy, save space, and filter data for data replication. Moreover, data replication is used to back up multiple copies of data at different locations.
2.4 Conclusions and Future Work
In this paper, the deep study of epidemic models and methodologies has been investigated, and hence, we proposed a new model that has not been used in the earlier studies. This model will include unsupervised algorithms in which the system will be trained in order to capture and react to influenza-like activities so that the preventive measures can be taken to get rid of the epidemic as early as possible and we have established a proposed method for identifying of differentially expressed glycans. We will extend this work in future to find bonding between glycoproteins structure and moreover how the structure of glycan will change from host to host and estimate the mathematical parameters for the molecular insight of epidemiological characteristics in pandemic H1N1 influenza virus and also find the relationship between biosecurity and glycan. Biosecurity basically defines lots of attempts that secure biological dynamism, abnormality, and future of biology. In this article, we have to take some biosecurity concerns to control arising infectious diseases and pandemic flu and also organize some biosecurity events for the swine flu pandemic. The novel H1N1 virus has been recognized within swine in various countries like as Asia and Europe. Swine producers should be responsible to save themselves, farm workers, and swines from the further develop of H1N1. They should take biosecurity precautions that are respecting to the virus. The National Pork Board is requesting farm producers and veterinarians to maintain the precautions. At first, maintain biosecurity cultures to prevent the H1N1 to take entry their swineherd and also pay attention thoroughly for swines’ health, and take some necessary precautions to reduce its spread. Farm producers need to follow up all rules to prevent spread of the H1N1 virus between human to human.
Several of the herds have been infected with the H1N1 virus that infected farm workers likely passed the virus to pigs. If producers restrict the crowd of people in their swine farm, also spread and implement bio-security rules for farm workers like as do not allow people who suffer flu-like symptoms, this way they can prevent H1N1. It is also essential that when workers will enter the pig farm, they require valveless respirators mask, gloves, and other personal protective equipment to prevent it. Before entering the pig farm, all people must clean up hands and arms with hot water and soap and produces should arrange the clothing and shoe (farm-specific) for entering within the pig farm. Cheer up farm workers to maintain all rules of biosecurity. Symptoms of the H1N1 influenza virus are basically fever, cough, body aches, and sometimes vomiting. They should provide farm workers with personal protective equipment and training. Vaccination is very important to stop human infections from stain of seasonal human influenza. Still, vaccination will decrease the amount of spreading H1N1 and virus shed if infected during outbreaks of human influenza and will give a boundary for human influenza virus infection of swines.
1. Jones, S., Nelson, S., Pillai, M.R., Evolutionary, genetic, structural characterization and its functional implications for the Influenza A (H1N1) infection outbreak in india from 2009 to 2017. Sci. Rep ., 9, 14690, 2019.
2. Rabadan, R., Levine, A.J., Knitz, M., Non-random reassortment in humaninfluenza A viruses. Influenza Other Respir. Viruses , 2, 1, 9–22, PubMed.gov, 2008, 2002.
3. Solovyov, A., Palacios, G., Briese, T., Lipkin, I.W., Rabadan, R., cluster analysis of the origins of the new Influenza A (H1N1) virus, Eurosurveillance , 2009;14(21):19224.
4. Eichelberger, M.C. and H.W., Influenza neuraminidase as a vaccine antigen. Curr. Top. Microbiol. Immunol ., 386, 275–299, 2015.
Читать дальше















