How it will work?
For communication, we will combine the CrANS with the MANETs, WANETs, FANETs, and Wi-Fi to transfer the data from one area to other. We will use the presence networks to make a crowd for the transfer of data
To define the routing protocol for a network, we have to study the routing classification. We have to choose the best route discovery, protocol operation and network organization. In network organization, we chose location-based protocol. In route discovery, we use hybrid base protocol. In the protocol operation, we selected the negotiate-based protocol.
We can send data directly or through different nodes. In this case, if one node will miss the data, information will be lost. In the single-hop transmission, time will be high and there is always the risk of link loss during the transmission as depicted in Figure 6.11.
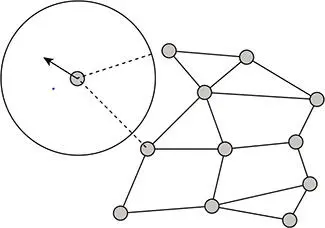
Figure 6.11 Single hop.
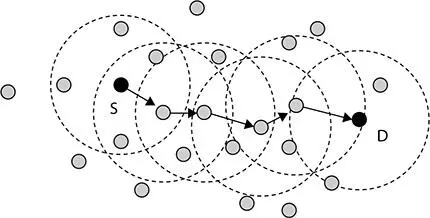
Figure 6.12 Multihop.
In the case of multiple-hop network, we can send to the different nodes at the same time. If the information is lost by the one node other node can perform the task without the delay in transmission. With the multiple-hop system, we can make the small path by using available nodes in the network. The transmission will be fast and reliable as presented in Figure 6.12.
6.3.3 Classification of Routing Protocol
6.3.3.1 Location Base Protocol
Pro-active protocols contain the routing table which contains information of all the nodes present in the network. To send the data one looks up to the table for transmission and sends the data.
We are defining a protocol in which we can access one’s location without network availability. To do so, we are taking a Geocast location routing base protocol. Geocast protocol is used for specific region/location. Geocast protocol uses the GPRS to detect the location of sender and receiver for data transformation. Geocast routing protocol uses the features of both unicast and multicast location protocol. By using this feature, we can send the information to a single and multiple destinations. It can propagate the information to the nearest target and within the target.
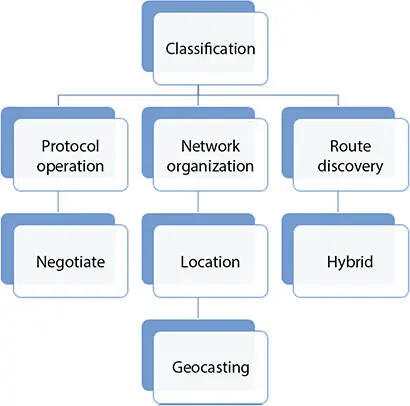
Figure 6.13 Protocol operation.
In reactive approach, if we want to transfer the data, then find the route. Discovery of the route is immediately found and then transmission of data happens. After discovery, table is updated and data packets delivered accordingly.
While in pro-active, table is already prepared and contains all the information of node. To find the route, discovery in the case of missing link causes delay to produce.
For CrANs, we will use the hybrid base protocol for the transmission of data. It is the combination of pro-active and reactive base route discovery. We can send data to a channel/person by asking for permission by the receiver and can directly send it to the receiver without permission. By using these features, we can make a network more efficient.
6.3.3.3 Protocol Operation
Pro-active and reactive classes combine to form a hybrid operation. These protocols have table and change the table on demand for routing protocol. We use negotiate base protocol for transmission of data from sender to receiver shown in Figure 6.13.
To design a protocol, we will face a lot of challenges which includes latency, reliability, energy consumption, power saving, and dynamic network and safety.
Another important feature is to describe network performance. Duration of time transfer data from one node to other is known as latency. Delays decrease the latency factor. To decrease the latency retransmission of data packet, change in topology. The more delay less latency. CrANs has high latency factor.
It is most important parameter to check the designing of routing protocol. It is the successful transmission of data from source to sink node. CrANs are highly reliable as they have more mobile nodes and frequently change of topology. CrANs are highly dynamic network due to the infrastructure-less feature.
CrANs can be used for security purpose in any developing country. But it can be a high risk for anyone. Simple protocols are easy to hijack by connecting a powerful receiver. Somebody can block a network or send false information to the people.
6.3.4.4 Power Consumption
It depends on a lot of factors like size of network, clusters, overheads, traffic load, and again transmission of data packet. It is important issue in the network. Complex network are not easy to operate.
Energy consumption is important factor to define a network life time. If the transmission increases collision, delay time and packet loss increases. We can decrease the energy consumption by various techniques of delay and increasing throughput.
In the developing countries like Pakistan, we need such type of network in which we have minimum communication gap. We can use this network in different aspects of daily life. It can be used for safety, supervision, data acquisition, control application, monitoring, and research and security purpose.
In CrANs, we can monitor the traffic in the developing countries. By doing this, we can use this network to check the traffic flow of a city. For medical emergencies, we can use CrANs network to check traffic jam, and for such situation, use another road.
6.3.5.2 Control and Automation
For developing countries, we can control the traffic and crowd by using CrANs. In the case of accident and VIP protocol, it can easily control the traffic. It can be used to guide the ambulance, police cars, or any other emergency vehicles. In an otherwise catastrophic condition, the security force can have the overall control of the situation using this network.
We can use it in army where information needing to be transferred is sensitive; in the presence of jammers, we can use CrANs to provide the network to send and receive important messages. It can transfer nodes in the absence of a network implying the information cannot be tracked or hacked. In Pakistan, on 9 thand 10 thMoharam, there is traffic jam in every city of Pakistan. There are security threats due to the recent terrorist attacks. In these days, signals are jammed and due to the absence of all networks nobody can contact to each other. For the transfer of important information, we can use non dedicated agents of CrANs to connect the next person through the VANETs and FANETs.
6.3.5.4 Nuclear Power Plants
Читать дальше















