1 Cover
2 Title Page Applied Smart Health Care Informatics A Computational Intelligence Perspective Edited by Sourav De Cooch Behar Govt. Engineering College, Cooch Behar, West Bengal, India Rik Das Xavier Institute of Social Service, Ranchi, Bihar, India Siddhartha Bhattacharyya CHRIST (Deemed to be University), Bengaluru, India Ujjwal Maulik Jadavpur University, Kolkata, West Bengal, India
3 Copyright
4 Dedication
5 Preface
6 About the Editors
7 List of Contributors
8 1 An Overview of Applied Smart Health Care Informatics in the Context of Computational Intelligence 1.1 Introduction 1.2 Big Data Analytics in Healthcare 1.3 AI in Healthcare 1.4 Cloud Computing in Healthcare 1.5 IoT in Healthcare 1.6 Conclusion References Note
9 2 A Review on Deep Learning Method for Lung Cancer Stage Classification Using PET‐CT 2.1 Introduction 2.2 Related Works 2.3 Methods 2.4 Results and Discussion 2.5 Conclusion References Note
10 3 Formal Methods for the Security of Medical Devices 1 3.1 Introduction 3.2 Background: Cardiac Pacemakers 3.3 State of the Art, Formal Verification Techniques 3.4 Formal Runtime‐Based Approaches for Medical Device Security 3.5 Summary References Notes
11 4 Integrating Two Deep Learning Models to Identify Gene Signatures in Head and Neck Cancer from Multi‐Omics Data 4.1 Introduction 4.2 Related Work 4.3 Materials and Methods 4.4 Results 4.5 Discussion Acknowledgments References Note
12 5 A Review of Computational Learning and IoT Applications to High‐Throughput Array‐Based Sequencing and Medical Imaging Data in Drug Discovery and Other Health Care Systems 5.1 Introduction 5.2 Biological Terms 5.3 Single‐Cell Sequencing (scRNA‐seq) Data 5.4 Methods of Multi‐Omic Data Integration 5.5 AI Drug Discovery 5.6 Medical Imaging Data Analysis 5.7 Applying IoT (Internet of Things) to Biomedical Research 5.8 Conclusions Acknowledgments References Note
13 6 Association Rule Mining Based on Ethnic Groups and Classification using Super Learning 1 6.1 Introduction 6.2 Background 6.3 Motivation and Contribution 6.4 Data Analysis 6.5 Methodology 6.6 Experiments and Results 6.7 Conclusion and Future Work References Notes
14 7 Neuro‐Rough Hybridization for Recognition of Virus Particles from TEM Images 1 7.1 Introduction 7.2 Existing Approaches for Virus Particle Classification 7.3 Proposed Algorithm 7.4 Experimental Results and Discussion 7.5 Conclusion References Notes
15 8 Neural Network Optimizers for Brain Tumor Image Detection 8.1 Introduction 8.2 Related Works 8.3 Background 8.4 Case Study ‐ Brain Tumor Detection 8.5 Conclusion References Note
16 9 Abnormal Slice Classification from MRI Volumes using the Bilateral Symmetry of Human Head Scans 9.1 Introduction 9.2 Literature Review 9.3 Methodology 9.4 Materials and Metrics 9.5 Results and Discussion 9.6 Conclusion References Note
17 10 Conclusion References Note
18 Index
19 End User License Agreement
1 Chapter 2 Table 2.1 Training setup for AlexNet.Table 2.2 Performance evaluation of classification accuracy.Table 2.3 Comparative analysis of existing methods and the proposed method.Table 2.4 Comparative analysis of the existing methods and the proposed meth...
2 Chapter 3Table 3.1 Example behavior of an RV monitor for property 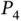 .
.
3 Chapter 4Table 4.1 The performance (test‐accuracy) of the proposed capsule and basic ...
4 Chapter 5Table 5.1 Methods for cell clustering and visualization.Table 5.2 Methods for the bifurcation/branch identification ordering of cell...Table 5.3 Gene‐level analysis tools (identifying differentially expressed ge...Table 5.4 Unsupervised data integration methods.Table 5.5 Supervised data integration tools.Table 5.6 Semi‐supervised data integration tools.Table 5.7 List of AI‐based computational tools for drug discovery.
5 Chapter 6Table 6.1 Distribution of breast cancer patients based on race or ethnicity.Table 6.2 Training data obtained by applying SMOTE and ENN.Table 6.3 Default parameter values for corresponding base learners.Table 6.4 Discovered rules using the class association rule method (conseque...Table 6.5 Extracted rules using the class association rule technique (conseq...Table 6.6 Rules generated using the class association rule technique (conseq...Table 6.7 Performance (accuracy, precision, recall/sensitivity, specificity)...Table 6.8 Performance (AUC, F1, and G‐mean) of the SL and three ML algorithm...
6 Chapter 7Table 7.1 Classification accuracy (%) obtained by the proposed method and it...Table 7.2 Performance analysis of different local descriptors and proposed m...Table 7.3 Performance analysis of the proposed method and several deep archi...
7 Chapter 8Table 8.1 Accuracy of artificial neural network models for differing optimiz...Table 8.2 Performance analysis of neural network optimizers using early stop...Table 8.3 Comparison of the proposed method with state‐of‐the‐art methods.
8 Chapter 9Table 9.1 Histogram‐based image features.Table 9.2 GLCM‐based image features.Table 9.3 GLRLM‐based image features.Table 9.4 Correlation of the selected features with the class label.Table 9.5 Test phase predictions for the selected volumes from the IBSR‐18 a...
1 Chapter 2 Figure 2.1 AlexNet architecture. Figure 2.2 Metastasis‐PET image. Figure 2.3 Lymph node‐fused PET‐CT image. Figure 2.4 Classification results of the primary tumor (T). Figure 2.5 Classification accuracy of the primary tumor (T). Figure 2.6 Loss function for the primary tumor (T). Figure 2.7 Confusion matrix for the primary tumor (T). Figure 2.8 Classification results of the metastasis (M). Figure 2.9 Classification accuracy of metastasis (M). Figure 2.10 Loss function for the metastasis (M). Figure 2.11 Confusion matrix for the metastasis (M). Figure 2.12 Classification results of the lymph node (N). Figure 2.13 Classification accuracy of the lymph node (N). Figure 2.14 Loss function for the lymph node (N). Figure 2.15 Confusion matrix for the lymph node (N).
2 Chapter 3Figure 3.1 The heart‐pacemaker system shows leads connected to the right atr...Figure 3.2 Timing diagram for a DDD mode pacemaker (adapted from Pinisetty e...Figure 3.3 Timing information of electrocardiogram signals.Figure 3.4 Model checking.Figure 3.5 Conformance testing with formal methods.Figure 3.6 Verification monitor.Figure 3.7 Enforcement mechanism.Figure 3.8 Overview of the RV monitoring approach (from Pinisetty et al. (20...Figure 3.9 Timed automaton defining property 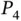 in 3.4.2 (from Pinisetty et a...Figure 3.10 Architecture of the RV monitor (from Pinisetty et al. (2018)).Figure 3.11 Pacemaker with runtime enforcer (from Pearce et al. (2019b)).Figure 3.12 Simplified DTA for policy
in 3.4.2 (from Pinisetty et a...Figure 3.10 Architecture of the RV monitor (from Pinisetty et al. (2018)).Figure 3.11 Pacemaker with runtime enforcer (from Pearce et al. (2019b)).Figure 3.12 Simplified DTA for policy 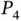 ,
, 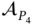 (from Pearce et al. (2019b)).Figure 3.13 System composition (from Pearce et al. (2019b)).Figure 3.14 Generalized enforcer hardware (from Pearce et al. (2019b)).
(from Pearce et al. (2019b)).Figure 3.13 System composition (from Pearce et al. (2019b)).Figure 3.14 Generalized enforcer hardware (from Pearce et al. (2019b)).
3 Chapter 4Figure 4.1 Schematic of autoencoder architecture.A representation of the phy...Figure 4.2 Integrative analysis of multiomics data through an autoencoder mo...Figure 4.3 Proposed capsule network architecture.The details of the multiple...Figure 4.4 The training and validation accuracy of the proposed model.Figure 4.5 Box plots of coupling coefficient values between primary‐ and typ...
Читать дальше

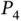 .
.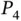 in 3.4.2 (from Pinisetty et a...Figure 3.10 Architecture of the RV monitor (from Pinisetty et al. (2018)).Figure 3.11 Pacemaker with runtime enforcer (from Pearce et al. (2019b)).Figure 3.12 Simplified DTA for policy
in 3.4.2 (from Pinisetty et a...Figure 3.10 Architecture of the RV monitor (from Pinisetty et al. (2018)).Figure 3.11 Pacemaker with runtime enforcer (from Pearce et al. (2019b)).Figure 3.12 Simplified DTA for policy 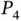 ,
, 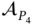 (from Pearce et al. (2019b)).Figure 3.13 System composition (from Pearce et al. (2019b)).Figure 3.14 Generalized enforcer hardware (from Pearce et al. (2019b)).
(from Pearce et al. (2019b)).Figure 3.13 System composition (from Pearce et al. (2019b)).Figure 3.14 Generalized enforcer hardware (from Pearce et al. (2019b)).










