You should create at least one user for your server in addition to the root operator. This is for security purposes and to avoid logging in as root, either through the keyboard at the server or remotely over the network. The default shell and home directory settings should remain set at the defaults, which are the Bourne Again SHell ( bash) and the /homedirectory.
See Chapter 4, "Command-Line Quick Start," for how to become the root user or run root commands as a regular user. See Chapter 10 for details on managing users.
TIP
Good passwords are essential for system security. However, some people still rely on passwords as simple as admin. This is asking for trouble, and we would encourage you to create a strong password made up of letters, numbers, and even punctuation. It can be difficult to create a password that is easily memorable and that includes punctuation, but it can be simpler than you think. For instance, George Nedeff may want to use his full name as a password, but that would be easy to crack. What he could do is use punctuation and numbers to replace similar letters in his name, such as G30rg3n3defF. This is a very strong password, and not easily broken, but at the same time it is very easy to remember.
Software Selection and Installation
Fedora enables you to select three predefined options for the installation package manifest. For this example, we're just going to use Office and Productivity, but if you are going to explore the chapters in the latter third of this book, you will need Software Development, and you will definitely need Web Server if you are going to use what you learn in Chapter 17. This screen is shown in Figure 1.21.
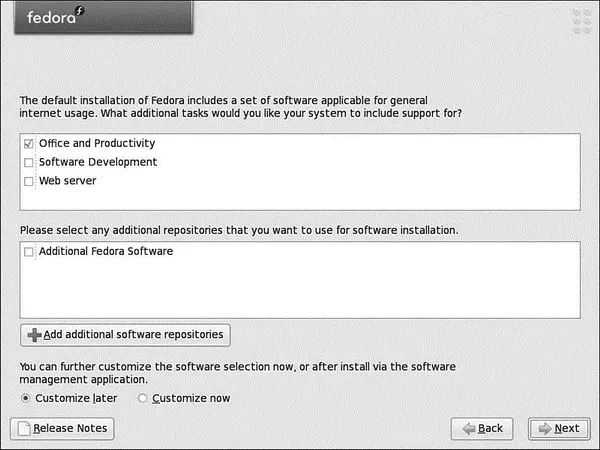
FIGURE 1.21 Fedora's new and simplified package selection screen.
What Happened to Install Everything?
In previous versions of Fedora and Red Hat Linux, there was an option to install every thing available. This has now been removed from Fedora for a number of reasons. First of all, installing all the packages can create dependency nightmares when upgrading and installing new packages. Second, there can be too many packages for new users to handle. Third, and perhaps most important, it can pose a huge security risk to your system. The more software you have installed, the greater the risk that someone could find a vulnerable entry point into your system.
NOTE
Fedora can enter your own repositories at install time. Fedora takes these new repositories into account when you go through the Customize Packages screens. All you have to do is provide a name for the repository, as well as the FTP or HTTP server and path details to the repomd.xmlfile. Just click the Add Repository button to do this.
You are also able to specify whether you want to customize your package selection further by selecting the Customize Now button and clicking Next to go to Figure 1.22. Otherwise, just click Next to land at the final screen.
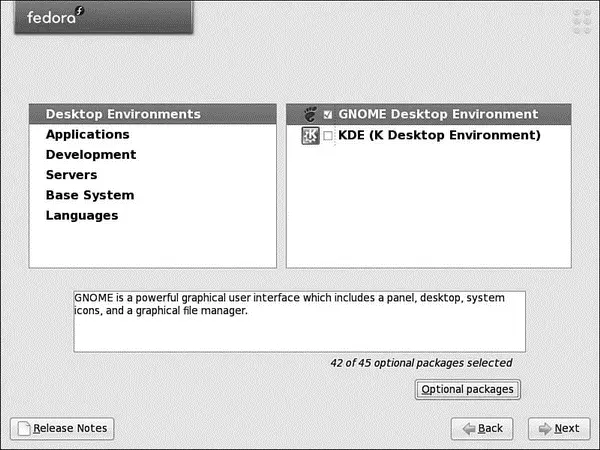
FIGURE 1.22 Specify the exact packages you want for your installation.
If you decided to customize your package choice, you will see a screen similar to Figure 1.22. On the left side are the generic categories that contain software. As you click each category, a new set of package groups appears on the right side. Mark the check box against each package group to install the default packages associated with that group. If you want to specify additional packages within the group, click the optional packages button to see all the other packages available for the group, shown in Figure 1.23. Select the ones that you require and click close to add them to your package list. After you finish selecting your packages, click Next to allow Fedora to scan for any dependency problems.
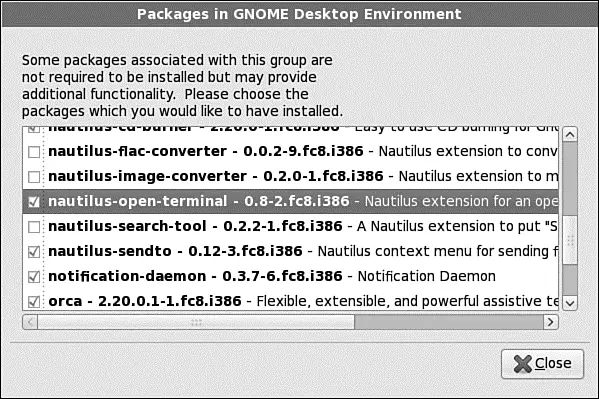
FIGURE 1.23 Fine-tune your installation by selecting only the packages that you really need.
You finally arrive at the last screen before Fedora actually starts to install anything, so it is a good idea to take a deep breath and think about anything you might have forgotten. It is easy to go back to any stage of the installation process by clicking the Back button until you reach where you want to go.
When you are happy, click Next to allow Fedora to install the system. Now is a good time to make a cup of coffee because it can take up to an hour to install Fedora, depending on the options that you have chosen. As Fedora is installed, it tells you which package it is currently working on, as shown in Figure 1.24.
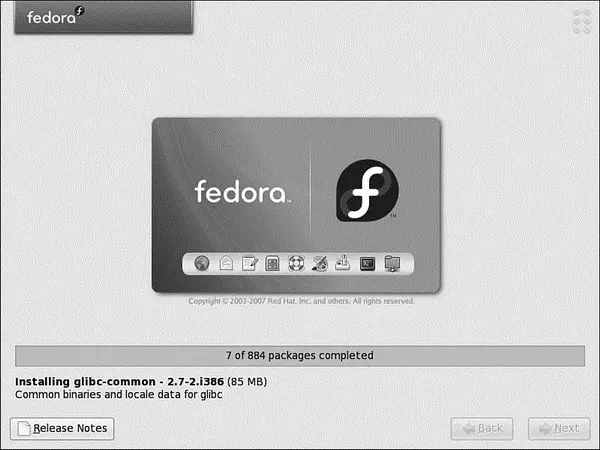
FIGURE 1.24 The Fedora installer formats your drive, and then installs selected software package groups.
If you are installing over a network or by DVD, take a break; the install proceeds unattended through the software installation.
You are finished! Click the Exit button, and the installer ejects any inserted media and reboots. The GRUB boot loader presents a boot prompt, as shown in Figure 1.25.
FIGURE 1.25 Boot Fedora with GRUB by pressing the Enter key or waiting 5 seconds.
If you have set a GRUB password, press P , type your password, and press Enter. If you do nothing for five seconds, or press Enter, either boot loader boots Linux.
NOTE
After installation, you can edit the file /boot/grub/grub.confand change the timeout=setting to change the boot time to a value other than 5 seconds.
Although the vast majority of configuration is done during the actual installation, Fedora allows you to choose some more options before you log in for the first time. When you boot Fedora, it loads firstboot, which is the utility responsible for personalizing your computer. It asks you a few straightforward questions and the end result is that you are able to log in to Fedora.
The first screen welcomes you to firstbootand you should click Next to start. The next screen asks whether you accept the conditions under which Fedora is released. If you agree with what is said, click the Yes button and then click Next.
NOTE
To read the end-user licensing agreement for Fedora, go to http://fedoraproject.org/wiki/Legal/Licenses/EULA.
Firewall configuration is up next (see Figure 1.26), and you should always have your fire wall enabled. Sensibly, Fedora defaults to this, but it also asks you whether you want to allow access to specific ports to allow services to run. Depending on your requirements, you might want to select one or more of the boxes. You can also enter in specific ports and the protocol (TCP or UDP), although you should be aware that the more services or ports you allow access to, the less secure your system becomes as it opens up more opportunities for attack.
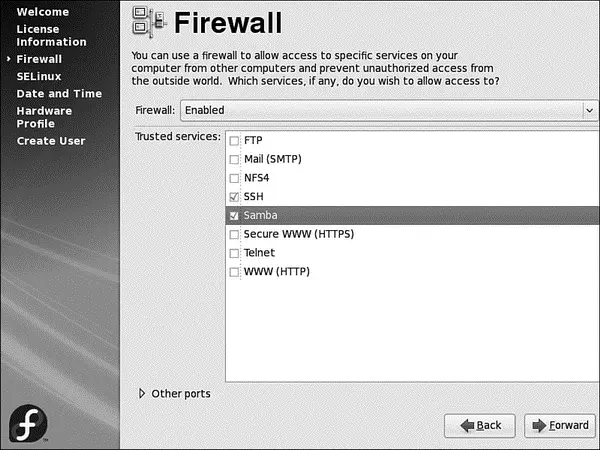
FIGURE 1.26 The firewall is a key part of your defense against would-be crackers. When you are happy with your selection, click the Next button to start configuring SELinux.
Читать дальше











![Andrew Radford - Linguistics An Introduction [Second Edition]](/books/397851/andrew-radford-linguistics-an-introduction-second-thumb.webp)






