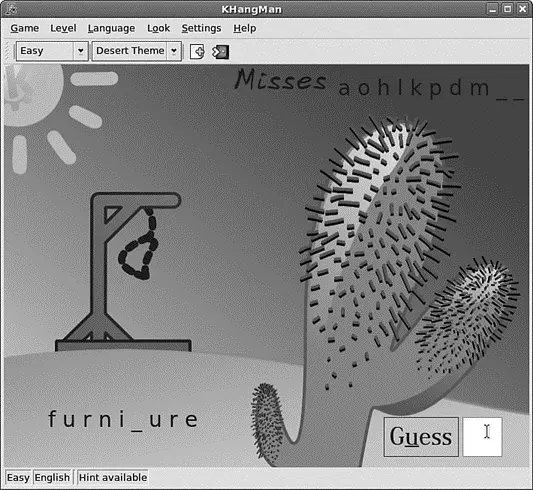
FIGURE 9.7 Enjoy a game of hangman with your kids and learn some language in this colorful part of KDEedu.
Playing Windows Games with Cedega
As mentioned earlier, the key to mass-market appeal of an operating system is in the applications available for it. A group of developers saw that the vast majority of the computing world was using Windows-based productivity and gaming software and decided to develop a way to run this software on Linux, thereby giving Linux users access to this large application base. The developers came up with a program called Wine, which has been updated regularly and forms the basis of the gaming variant called Cedega. This is a commercial product available from developers TransGaming Technologies (http://www.transgaming.com/), so you cannot retrieve it by using yum.
However, Cedega is a very popular and up-to-date product with support for recent releases such as Elder Scrolls IV and Command & Conquer 3: Tiberium Wars. Because the state of Cedega is constantly changing, TransGaming Technologies has a subscription service which means that you get updates for the code when they are released — ensuring that you are able to enjoy not only the games of today, but also those of tomorrow.
So, if you can't wait for Linux to become more popular with game developers, use Cedega as a stop-gap until they can be persuaded to support Linux directly.
TIP
The keys to successful gaming in Linux are to always read the documentation thoroughly, always investigate the Internet resources thoroughly, and always understand your system. Installing games is a great way to learn about your system because the reward of success is so much fun.
► http://www.transgaming.com/— The official TransGaming Technologies website provides details of games that are directly supported under Cedega.
► http://www.linuxgames.com/— A good source of up-to-date information about the state of Linux gaming.
► http://zerowing.idsoftware.com/linux/doom/— Includes a complete how-to and troubleshooting guide for running Doom 3 under Linux.
► http://www.unrealtournament.com/ — The official site of Unreal Tournament.
► http://www.nvnews.net/vbulletin/forumdisplay.php?f=14— The Official NVIDIA Linux driver support forum.
► http://www.nvidia.com/object/linux.html— Home page for the NVIDIA Linux drivers.
► http://tinyurl.com/3pm2v— Home page for the ATI Linux drivers (courtesy of tinyurl.com).
PART III
System Administration
CHAPTER 10
Managing Users
One of the most important things you need to learn while using Fedora is effective user administration. Whether you are setting up a system for use just by your self, sharing it among a family of five, or even working with a machine that has to handle several thousand different users, it is important that you understand how to effectively assign user permissions and lock down the areas you want to protect. Equally important is the ability to fine-tune user access rights, to enable people to do what they need to do, and not necessarily what they want to!
Managing users includes managing home directories and settings that are unique to each user. You also have to examine how much of the overall system to which you want to give the users access, as well as establish good pass word practice. This chapter covers all these tasks, as well as others that teach you how to effectively manage the users of your system. It also takes a look at the super-user account so that you can understand why it is so important and also how to let others access some, if not all, of the super-user's power.
Every Fedora installation typically contains three types of accounts: the super user, the day-to-day user, and the system user. Each type is important in its own right, and you must know what each is responsible for. If they didn't work together, Fedora would have a hard time doing anything!
All users must have accounts on the system. Fedora uses the /etc/passwdfile to hold information on user accounts. Each user, regardless of type, has a one-line entry of account information stored in the /etc/passwdtext file.
Each account entry contains a username (used for logging in), a password field containing an x(as passwords are actually contained in /etc/shadow), a user ID (UID) , and a group ID (GID) . The fifth field contains optional human ID information, such as real name, office location, phone number, and so on. The last two fields are the location of the user's home directory and the user's default login shell. See the section "The Password File" later in this chapter for more information.
Like other Linux distributions, Fedora makes use of the established UNIX file ownership and permission system. Each file (which can include directories and even devices) can be assigned one or more of read, write, and/or execute permissions. These can be assigned further to the owner, a member of a group, or anyone on the system. File security is drawn from combining ownership and permissions. The system administrator (most commonly referred to as the super user) has total responsibility to make sure that users have proper UIDs and GIDs, and to ensure that sensitive files (which can include important system files) are locked down using file permissions. You'll learn more about permissions in the section "Managing Permissions."
Regardless of how many system administrators are present on the system, there can only be one root user. This is the user who has access to everything, and can grant or take away any privileges on the system. The root user has a UID of 0 and a GID of 0, making it unique among all other users on the system. The root user can use any program, manipulate any file, go anywhere in the file system, and do anything within the Fedora system. For reasons of security, that kind of raw power should be given to only a single trusted individual.
It is often practical for that power to be delegated by the root user to other users. This delegation is referred to as an elevation of privileges, and these individuals are known as super users because they enjoy the same powers that root enjoys. This approach is normally used only on large systems in which one person cannot effectively act as the sole system administrator.
NOTE
On your Fedora system, when you log in as root, you are root or the super user. In this chapter, the terms root, super user, system administrator , and sysadmin are used interchangeably, although they need not all refer to a single person.
A regular user is someone who logs on to the system to make use of it for nonadministrative tasks such as word processing or email. These users do not need to make systemwide changes, nor do they have to manage any other users. However, they might want to be able to change settings that are specific to them (for instance, a desktop background). Of course, depending on how draconian the root user is, regular users might not even be able to do that!
The super user grants privileges to regular users by means of file and directory permissions. (Those are covered in the section entitled "Managing Permissions.") For example, if the super user does not want you to change your settings in ~/.profile(the ~is a shell shortcut representing your home directory), root can alter the permissions so that you may read from, but not write to, that file.
Читать дальше






![Andrew Radford - Linguistics An Introduction [Second Edition]](/books/397851/andrew-radford-linguistics-an-introduction-second-thumb.webp)






