CAUTION
Because of the potential for making a catastrophic error as the super user (using the command rm -rf /*is the classic example, but do not ever try it!), always use your system as a regular user and become root only temporarily to do sysadmin duties. While you are on a multiuser system, consider this advice an absolute rule; if root were to delete the wrong file or kill the wrong process, the results could be disastrous for the business. On your home system, you can do as you please and running as root makes many things easier, but less safe. In any setting, however, the risks of running as root full time are significant. (In case you're wondering, the above command would completely wipe your entire file system, leaving you with nothing but a red face!)
The third type of user is the system user. The system user is not a person, but rather an administrative account that the system uses during day-to-day running of various services. For example, the system user named apacheowns the Apache Web Server and all the associated files. Only it and root can have access to these files — no one else can access or make changes to these files. System users do not have a home directory or password, nor do they permit access to the system through a login prompt.
You will find a list of all the users on a system in the /etc/passwdfile. Fedora refers to these users as the standard users because they are found on every Fedora computer as the default set of system (or logical) users provided during the initial installation. This "standard" set differs among Linux distributions.
The command-line approach to adding any user is actually quite simple and can be accomplished on a single line. In the example shown here, the sysadmin uses the useraddcommand to add the new user bernice.The command adduser(a variant found on some UNIX systems) is a symbolic link to useradd,so both commands work the same. In this example, we use the -poption to set the password the user requested; we use the -soption to set his special shell, and the -uoption to specify his UID. (If we created a user with the default settings, we would not need to use these options.) All we want to do can be accomplished on one line:
# useradd bernice -p sTitcher -s /bin/bash -u 507
The sysadmin can also use the graphical interface that Fedora provides, as shown in Figure 10.1. It is accessed as the Users and Groups item from the System Settings menu item. Here, the sysadmin is adding a new user to the system where user berniceuses the bash command shell.
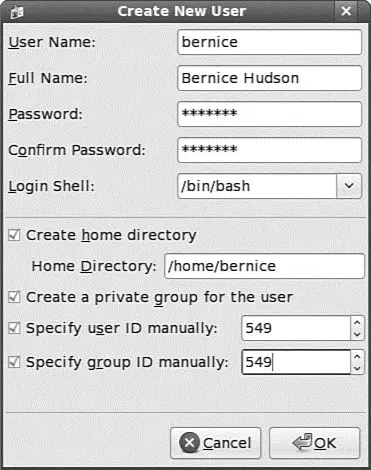
FIGURE 10.1 Adding a new user is simple. The GUI provides a more complete set of commands for user management than for group management.
These are the steps we used to add the same account as shown in the preceding command, but using the graphical User Manager graphical interface:
1. Launch the Fedora User Manager graphical interface by clicking the Users and Groups menu item found in the System, Administration.
2. Click the Add User button to bring up the Add User dialog window.
3. Fill in the form with the appropriate information, as described in the first paragraph in this section.
4. Click the drop-down Login Shell menu to select the bashshell.
5. Check the Specify User ID box to permit access to the UID dialog.
6. Using the arrows found in the UID dialog, increment the UID to 5413.
7. Click OK to save the settings.
Note that the user is being manually assigned the UID of 549because that is her UID on another system machine that will be connected to this machine. Because the system only knows her as 549and not as bernice,the two machines would not recognize berniceas the same user if two different UIDs were assigned.
NOTE
A Linux username can be any alphanumeric combination that does not begin with a special character reserved for shell script use (see Chapter 11, "Automating Tasks," for disallowed characters, mostly punctuation characters). Usernames are typically the user's first name plus the first initial of her last name, something that is a common practice on larger systems with many users because it makes life simpler for the sysadmin, but is neither a rule nor a requirement.
A computer is, by its very nature, a number-oriented machine. It identifies users and groups by numbers known as the user ID (UID) and group ID (GID) . The alphabetic names displayed on your screen are there exclusively for your ease of use.
As was already mentioned, the root user is UID 0. Numbers from 1through 499and 65,534are the system, or logical, users. Regular users have UIDs beginning with 500; Fedora assigns them sequentially beginning with this number.
With only a few exceptions, the GID is the same as the UID. Those exceptions are system users who need to act with root permissions: sync, shutdown, halt, and operator.
Fedora creates a private GID for every UID of 500 and greater. The system administrator can add other users to a GID or create a totally new group and add users to it. Unlike Windows NT and some UNIX variants, a group cannot be a member of another group in Linux.
CAUTION
If you intend to make use of NFS, it is extremely important that you use the same UID for the user on the host and guest machines; otherwise, you will not be able to connect!
User Stereotypes
As is the case in many professions, exaggerated characterizations (stereotypes or caricatures) have emerged for users and system administrators. Many stereotypes contain elements of truth mixed with generous amounts of hyperbole and humor and serve to assist us in understanding the characteristics of and differences in the stereotyped subjects. The stereotypes of the "luser" and the "BOFH" (users and administrators, respectively) also serve as cautionary tales describing what behavior is acceptable and unacceptable in the computing community.
Understanding these stereotypes allows you to better define the appropriate and inappropriate roles of system administrators, users, and others. The canonical reference to these terms is found in the alt.sysadmin.recovery FAQ found at http://www.ctrl-c.liu.se/~ingvar/asr/.
Groups can make managing users a lot easier. Instead of having to assign individual permissions to every user, you can use groups to grant or revoke permissions to a large number of users quickly and easily. Setting group permissions allows you to set up work spaces for collaborative working and also to control what devices can be used, such as external drives or DVD writers. This approach also represents a secure method of limiting access to system resources to only those users who need them. As an example, the sysadmin could put the users andrew, paul, scott, derek, mark, and vanessain a new group named unleashed.Those users could each create files intended for their group work and chgrpthose files to unleashed.
Now, everyone in the unleashedgroup — but no one else except root — can work with those files. The sysadmin would probably create a directory owned by that group so its members could have an easily accessed place to store those files. The sysadmin could also add other users such as berniceand ildikoto the group and remove existing users when their part of the work is done. The sysadmin could make the user andrewthe group administrator so that andrewcould decide how group membership should be changed. You could also put restrictions on the DVD writer so that only andrewcould burn DVDs, thus protecting sensitive material from falling into the wrong hands.
Читать дальше






![Andrew Radford - Linguistics An Introduction [Second Edition]](/books/397851/andrew-radford-linguistics-an-introduction-second-thumb.webp)






