■ Domain ControllersAn OU for your organization’s domain controllers. This OU is created automatically in a domain.
■ High-Security Member ServersAn OU for servers that require higher than usual security configurations.
■ Member ServersAn OU for servers that require standard server security configurations.
■ Laptop and Mobile DevicesAn OU for laptops and mobile devices, which are inherently less secure and might require enhanced security configurations.
■ High-Security User WorkstationsAn OU for workstations that require higher than usual security configurations.
■ User WorkstationsAn OU for workstations that require standard workstation security configurations.
■ Remote Access ComputersAn OU for computers that remotely access the organization’s network.
■ Restricted ComputersAn OU for computers that require restrictive security configurations, such as computers that are used in labs or kiosks.
REAL WORLD You need to be extra careful when you deploy security templates through GPOs. If you haven’t done this before, practice in a test environment first, and be sure to also practice recovering computers to their original security settings. If you create a GPO and link the GPO to the appropriate level in the Active Directory structure, you can recover the computers to their original state by removing the link to the GPO. This is why it’s extremely important to create and link a new GPO rather than use an existing GPO.
To deploy a security template to a computer GPO, follow these steps:
1.After you configure a security template and have tested it to ensure that it is appropriate, open the GPO you previously created and linked to the appropriate level of your Active Directory structure. In the Group Policy Management editor, open Computer Configuration\Windows Settings\Security Settings.
2.Press and hold or right-click Security Settings, and then tap or click Import Policy.
3.In the Import Policy From dialog box, select the security template to import, and then tap or click Open. Security templates end with the.inf file extension.
4.Check the configuration state of the security settings to verify that the settings were imported as expected, and then close the policy editor. Repeat this process for each security template and computer GPO you’ve configured. In the default configuration of Group Policy, it will take 90 to 120 minutes for the settings to be pushed out to computers in the organization.
Using the Security Configuration Wizard

The Security Configuration Wizard can help you create and apply a comprehensive security policy. A security policy is an XML file you can use to configure services, network security, registry values, and audit policies. Because security policies are role-based and feature-based, you generally need to create a separate policy for each of your standard server configurations. For example, if your organization uses domain controllers, file servers, and print servers, you might want to create a separate policy for each of these server types. If your organization has mail servers, database servers, and combined file/print servers in addition to domain controllers, you should create separate policies tailored to these server types.
You can use the Security Configuration Wizard to do the following:
■Create a security policy
■Edit a security policy
■Apply a security policy
■Roll back the last-applied security policy
Security policies can incorporate one or more security templates. Much like you can with security templates, you can apply a security policy to the currently loggedon computer by using the Security Configuration Wizard. Through Group Policy, you can also apply a security policy to multiple computers. By default, security policies created with the Security Configuration Wizard are saved in the %SystemRoot%\security\msscw\Policies folder.
The command-line counterpart to the graphical wizard is the Scwcmd (Scwcmd.exe) utility. At an elevated administrator prompt, you can use Scwcmd Analyze to determine whether a computer is in compliance with a security policy and Scwcmd Configure to apply a security policy.
Creating security policies
The Security Configuration Wizard allows you to configure policies only for roles and features that are installed on a computer when you run the wizard. The precise step-by-step process for creating security policies depends on the server roles and features available on the computer that is currently logged on. That said, the general configuration sections presented in the wizard are the same regardless of the computer configuration.
The Security Configuration Wizard has the following configuration sections:
■ Role-Based Service Confi urationConfigures the startup mode of system services based on a server’s installed roles, installed features, installed options, and required services.
■ Network SecurityConfigures inbound and outbound security rules for Windows Firewall With Advanced Security based on installed roles and installed options.
■ Registry SettingsConfigures protocols used to communicate with other computers based on installed roles and installed options.
■ Audit PolicyConfigures auditing on the selected server based on your preferences.
■ Save Security PolicyAllows you to save and view the security policy. You can also include one or more security templates.
With the fact that the step-by-step process can vary in mind, you can create a security policy by following these steps:
1.Start the Security Configuration Wizard in Server Manager by tapping or clicking Tools, Security Configuration Wizard. On the Welcome page of the wizard, tap or click Next.
2.On the Configuration Action page, review the actions you can perform. (See Figure 5-11.) Create A New Security Policy is selected by default. Tap or click Next.
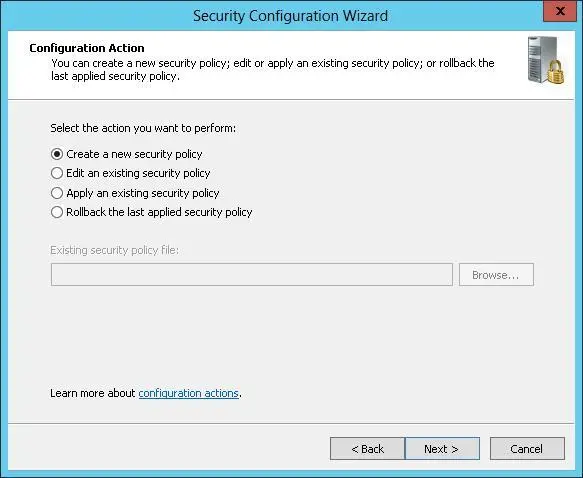
FIGURE 5-11Review the actions you can perform.
3.On the Select Server page, select the server you want to use as a baseline for this security policy. The baseline server is the server on which the roles, features, and options with which you want to work are installed. The computer that is logged on is selected by default. To choose a different computer, tap or click Browse. In the Select Computer dialog box, enter the name of the computer, and then tap or click Check Names. Select the computer account you want to use, and then tap or click OK.
4.When you tap or click Next, the wizard collects the security configuration and stores it in a security configuration database. On the Processing Security Configuration Database page, tap or click View Configuration Database to view the settings in the database. After you review the settings in the SCW Viewer, return to the wizard and tap or click Next to continue.
5.Each configuration section has an introductory page. The first introductory page is the one for Role-Based Service Configuration. Tap or click Next.
6.The Select Server Roles page, shown in Figure 5-12, lists the installed server roles. Select each role that should be enabled. Clear the check box for each role that should be disabled. Selecting a role enables services, inbound ports, and settings required for that role. Clearing a role disables services, inbound ports, and settings required for that role, provided that they aren’t required by an enabled role. Tap or click Next.
Читать дальше








