Richard O. Moore, III - Cyber Intelligence-Driven Risk
Здесь есть возможность читать онлайн «Richard O. Moore, III - Cyber Intelligence-Driven Risk» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Жанр: unrecognised, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Cyber Intelligence-Driven Risk
- Автор:
- Жанр:
- Год:неизвестен
- ISBN:нет данных
- Рейтинг книги:5 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 100
- 1
- 2
- 3
- 4
- 5
Cyber Intelligence-Driven Risk: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Cyber Intelligence-Driven Risk»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Cyber Intelligence-Driven Risk
overall
Cyber Intelligence-Driven Risk — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Cyber Intelligence-Driven Risk», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
The CI-DR program objectives provide an organization with guidance to assist in building a formal charter for the program, which can build rational processes of how the cyber data enters the life cycle and how analysis processes transform raw data to become “knowledge” and produce appropriate reporting in business terms. There is a ton of reporting being done today around cyber but most of it is done reactively and at the tactical level, meaning no business decisions are being made, and the information being reported is only valuable for use by a chief information security officer (CISO) or chief information officer (CIO) and is only used to make technology risk decisions. While this type of information is still valuable to the technician, as a risk or business leader you can most likely only use these tactical-level metrics and reporting as a way to find key performance indicators. The data or information at this stage in the cyber intelligence life cycle is still raw and provides no indicators of risk or useful information to business leaders.
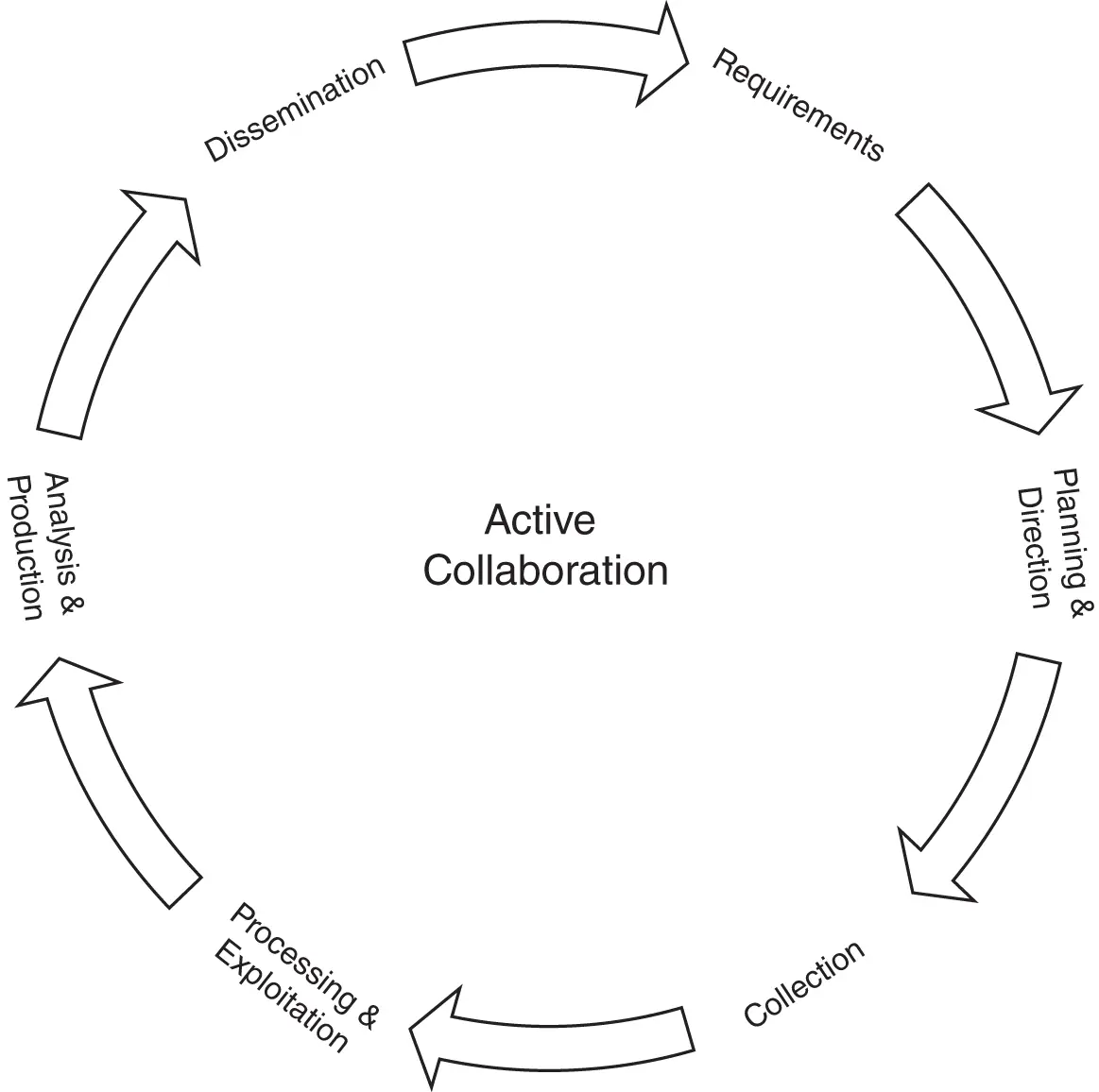
FIGURE 2.1 CI-DR™ Cyber intelligence life cycle.
We talk a lot about leveraging tradition intelligence concepts and processes within this book and our CI-DR cyber intelligence life cycle is a direct offspring of one of those concepts. Similar to traditional descriptions of the types of intelligence, the CI-DR types of cyber intelligence do not require much change to the definition or require advanced degrees in cybersecurity; it is, in fact, simplistic in nature. The two primary classes of the CI-DR cyber intelligence are “descriptive cyber intelligence” and “estimative cyber intelligence.” Descriptive cyber intelligence has two components. “Basic cyber intelligence,” which is the general background knowledge about established and relatively constant cyber conditions, is often encyclopedic in nature and often mundane. This information is easiest to gather, and is often available through open sources. 2Basic cyber intelligence is usually not decisive in nature, like providing vulnerability metrics without analysis and trends. Descriptive cyber intelligence also includes “current cyber intelligence,” which is concerned with describing the existing cyber situation. The differentiator between basic and current cyber intelligence is that current cyber intelligence describes more changeable factors. For example, if the organization has identified vulnerabilities within a certain system, but nothing yet has occurred to impact or exploit that system, this is basic cyber intelligence. However, if there is an exploit that leads to a compromise of the system from that identified vulnerability, this would be considered current cyber intelligence as the existing situation changed, and the intelligence is more time-sensitive for making a decision.
The second class of the CI-DR cyber intelligence is known as “estimative cyber intelligence,” and is focused on potential developments. Estimative cyber intelligence is the most demanding and is the most important task of creating “knowledge” from raw digital intelligence, as it seeks to anticipate a possible future or several futures. 3Just as military commanders cannot reasonably expect traditional estimative intelligence to precisely predict the future, estimative cyber intelligence deals with the realm of possibilities and probabilities. It is inherently the less reliable of the classes of intelligence because it is not based on what actually is or has been, but rather on what might occur. 4A good example of estimative cyber intelligence is described in our real-world example in the Introduction.
As we continue to describe the types of cyber intelligence used in our CI-DR framework and program, it is important for the reader to understand that efforts to provide “knowledge” and decisions are complicated by the ability to assess cyber capabilities and estimate adversarial intentions, which can become a complication during the interpretation of the information collected. To develop objective and accurate cyber intelligence, we must understand this problem. We can examine it through a discussion of signals or indicators and noise. 5Indicators or signals refer to information that can lead to valuable insight, whereas noise is simply useless information that interferes with identifying the truth. A good example of weeding through the noise can be found in the same example in our Introduction, where the QCF (Qassam Cyber Fighters) had been posting comments about their upcoming or past cyberattacks. This information was mostly false and extremely distracting, and misled or tainted much of the real intentions of their cyberattacks. Fortunately, there were clear signals and indicators that were being provided to see clearly through their many online rantings. However, the difference between true and false information is rarely easy to distinguish and the reader must take care to understand that effort must be made to differentiate.
As we continue to discuss the types of cyber intelligence and why the CI-DR uses these, we must also discuss the levels of intelligence. There are only three, to continue with simplicity, and these lead to our building cyber intelligence requirements in the upcoming chapters. The three levels of our CI-DR cyber intelligence types are strategic, operational, and tactical, in that order. Tactical cyber intelligence is the most fundamental, concerning location (i.e. geographical, networks, or internet protocols), capabilities (i.e. sophistication levels, skills, or method of delivery), and potential adversarial intent. Tactical cyber intelligence is the tactics, techniques, and procedures, or TTPs 6used in the cyber threat intelligence capability of the CI-DR program. In cyber it is wise to take care and understand that this is where most of the attention of cyber defense is focused today. While the tactical level deserves attention, the problem with a singular focus at this level means that the adversary is either already in the network, or at the door of your gateway trying to get in. Yet, if appropriate resources were expended in the previous two levels, some of this tactical activity may be precluded and have better usage by business leaders for decisions. 7The Security Operations Center (SOC) is fundamentally where tactical activities occur and will be discussed in a later chapter.
Operational cyber intelligence is the level at which campaigns and major operations are planned, conducted, and sustained. 8At the operational level, malicious actors plan their campaigns based upon what they have learned in collecting their own cyber intelligence and on what they had surmised as being necessary based upon their strategic goals. Actors build the capabilities (botnets, malware, delivery methodology [phishing], etc.) needed to support the tactical operations. They maneuver in cyberspace (hop points) to position capability where they need to in order to be effective in their tactical missions. This is the level where a hacktivist group may plan both cyber and physical world activities to support their objectives. 9Examples of operational-level cyber intelligence could be the following:
Trend analysis indicating the technical direction in which an adversary's capabilities are evolving.
Indications that an adversary has selected an avenue of approach for targeting your organization.
Indications that an adversary is building capability to exploit a particular avenue of approach.
The revelation of adversary tactics, techniques, and procedures.
Understanding of the adversary operational cycle (i.e. decision-making, acquisitions, command-and-control [C2] methods for both the technology and the personnel).
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Cyber Intelligence-Driven Risk»
Представляем Вашему вниманию похожие книги на «Cyber Intelligence-Driven Risk» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Cyber Intelligence-Driven Risk» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












