1 ...7 8 9 11 12 13 ...17 To browse a large file, use the morecommand. You need to press Enter or the spacebar on your keyboard to step forward. Pressing the B key will let you go backward. Finally, to search for text, press the /(forward slash) and the Q key to quit:
$more [file name]
lessis like the morecommand; it allows you to view the contents of a file and navigate inside it as well. The main difference between moreand lessis that the lesscommand is faster than the morecommand because it does not load the entire file at once, and it allows you to navigate inside the file using the Page Up/Down keys as well:
$less [file name]
To sort a text file, simply use the sortcommand:
$sort [file name]> [sorted file name] root@kali:~/temp# cat file1.txt 5 6 4 root@kali:~/temp# sort file1.txt>file1_sorted.txt root@kali:~/temp# cat file1_sorted.txt 4 5 6
To remove duplicates in a text file, you must use the uniqcommand:
$uniq [file name]> [no duplicates file name] root@kali:~/temp# cat file2.txt 5 6 4 4 5 5 5 root@kali:~/temp# uniq file2.txt> file2_uniq.txt root@kali:~/temp# cat file2_uniq.txt 5 6 4 5
Later in this book, you will learn how to use the sortand uniqcommands together to create a custom passwords dictionary file.
For the terminal window, we have two popular text editors, vim and nano. Most of the time, you can tackle four tasks in text editors:
Open/create the text file
Make text changes
Search for text
Save and quit
Nano is easier than vim. It's up to you to choose any of them; it's a matter of preference.
To open/create a text file, use these commands:
$vim [ text filename ]
$nano [ text filename ]
Once the text file is opened, you will need to start making your changes:
In nano, you can just enter your text freely.
In vim, you need to press I on your keyboard to enter insert mode.
If you want to search for a specific word inside your file, use these commands:
In nano, press Ctrl+W.
In vim, it depends which mode you're in.If you're in insert text mode, then hit the Esc key and then press / followed by the word that you want to search for.If you're in normal mode, then just press / followed by the word that you want to search for.
Finally, it's time to save and quit your text editor:
In nano, press Ctrl+O to save, press the Enter key to execute the save task, and then press Ctrl+X to exit.
In vim, make sure that you are in normal mode first (if you're not, then press the Esc key to go back in normal mode) and then use :wq . The w is for “write,” and the q is to quit.
Searching and Filtering Text
One more thing to learn in the world of text files is the search mechanism. There are so many ways to search and filter out text, but the popular ones are as follows:
grep
awk
cut
You've seen me using the grepcommand a lot. This filter command is structured in the following way:
$grep [options] [pattern] [file name]
Let's say you want to search for the word password in all the files starting from the root system ( /).
root@kali:/# grep -irl "password" / /boot/grub/i386-pc/zfscrypt.mod /boot/grub/i386-pc/normal.mod /boot/grub/i386-pc/legacycfg.mod
Here's what the options mean:
‐i : To ignore case and include all the uppercase/lowercase letters
‐r : To search recursively inside subfolders
‐l : To print the filenames where the filter matches
As another example, let's say you want to count the number of occurrences of the word password in the dictionary file rockyou.txt:
root@kali:/# cd /usr/share/wordlists/ root@kali:/usr/share/wordlists# grep -c "password" rockyou.txt 3959
The awkcommand is an advanced tool for filtering text files, and it uses the following pattern:
$awk /[search criteria]/ [options] [file name]
For example, let's say you want to search for the text root inside the /etc/passwdfile:
root@kali:/# awk '/root/' /etc/passwd root:x:0:0:root:/root:/bin/bash nm-openvpn:x:125:130:NetworkManager OpenVPN,,,:/var/lib/openvpn/chroot:/usr/sbin/nologin
Let's take the challenge one more step further. Let's say you want to extract the password of the root in the /etc/shadowfile (you can print the whole thing first so you can visualize the difference of before and after):
root@kali:/# awk '/root/' /etc/shadow root:$6$uf2Jy/R8HS5Tx$Vw1wHuBV7unq1hImYGTJdNrRwMwRtf0yd/aSH0zOhhdzWofAT5WUSduQTjWj8AbdmT62rLbcs6kP3xwdiLk.:18414:0:99999:7::: root@kali:/# awk -F ':' '/root/{print $2}' /etc/shadow $6$uf2Jy/R8HS5Tx$Vw1wHuBV7unq1hImYGTJdNrRwMwRtf0yd/aSH0zOhhdzWofAT5WUSduQTjWj8AbdmT62rLbcs6kP3xwdiLk.
We know that the shadow file is using the :delimiter to separate the sections, so we use ‐F ':'to get the job done. Then, we tell the tool to print only the second part of the delimiter {print $2}, which is the hashed password contents.
Another popular way to extract substrings is the cutcommand. In the following example, we use the catcommand to open the shadow file; then we use the grepcommand to filter out the root account, and finally, we use the cutcommand to extract the password:
root@kali:/# cat /etc/shadow | grep "root" | cut -d ":" -f 2 $6$uf2Jy/R8HS5Tx$Vw1wHuBV7unq1hImYGTJdNrRwMwRtf0yd/aSH0zOhhdzWofAT5WUSduQTjWj8AbdmT62rLbcs6kP3xwdiLk.
Remote Connections in Kali
There are two common ways to connect remotely to other operating systems. For Windows, it is the Remote Desktop Protocol (RDP), and for Linux, it's the Secure Shell (SSH). In the next sections, I will explain how to use each protocol to connect remotely to an OS (Windows or Linux).
RDP is used to connect remotely to a Windows OS. Let's suppose that during your engagement you encountered a remote desktop port 3389 open on a Windows host (e.g., during your port scanning phase). Then, you will need to try to connect to it with some basic credentials (e.g., a username of Administrator and a password of password123). There are many times during your engagements where you want to connect remotely to a Windows system to get the job done (from Kali Linux). In this case, you will need to use the rdesktopcommand.
$rdesktop [Windows host IP address] -u [username in windows] -p [password in windows]
You can also omit the password and enter it later. See the example in Figure 1.9.
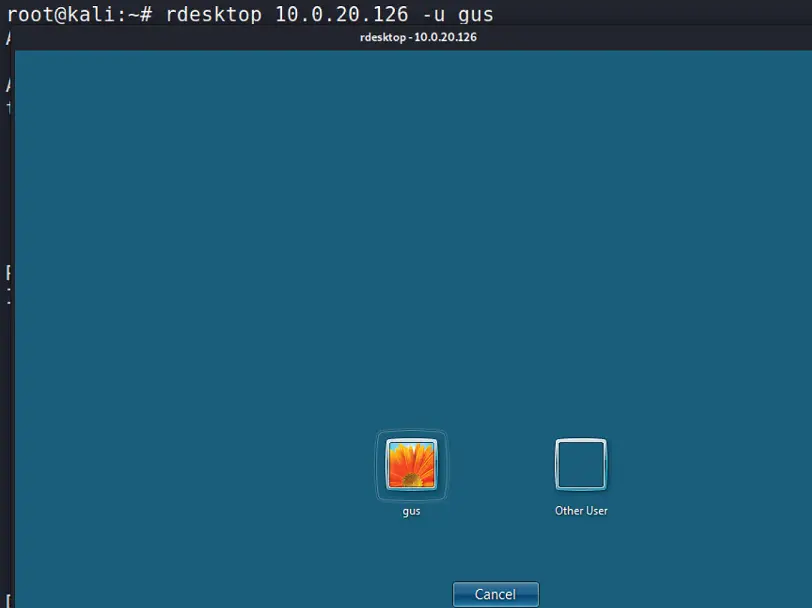
Figure 1.9“Windows Login”
The SSH protocol is a secure connection that allows you to execute commands remotely on a Linux host (in this case, Kali). By default, the SSH is a TCP protocol that works on port 22 by default. There are two ways to connect to a remote SSH server:
Using a username/password credentials
Using public/private keys (passwordless)
Let's start first with the method that uses the password. By default, all the user accounts except the root account can log in remotely to SSH:
$ssh username@kaliIP
Figure 1.10shows a root user who is not allowed to log in to Kali Linux remotely as well as a regular user ( kali) who is able to log in remotely using SSH. In Figure 1.10, I'm using MobaXterm on Windows OS to connect remotely using SSH to the Kali VM.
Читать дальше













