$apt remove [package name]
How do we find a package name? Let's say you want to install something that is not already installed on Kali. Then you can search the repository packages using the following command:
$apt-cache search keyword
Finally, if you want to install a package and you're not sure if the name exists in the repository, then you can use the apt‐cache showcommand:
$apt-cache show [software name] root@kali:/# apt-cache show filezilla Package: filezilla Version: 3.49.1-1 Installed-Size: 6997 Maintainer: Adrien Cunin Architecture: amd64 […]
One of my favorite terminal window tools to list all the running processes on Kali is called htop. By default, it's not installed on Kali, so to install it, we use the apt installcommand:
root@kali:/# apt install htop -y Reading package lists… Done Building dependency tree Reading state information… Done
Once it's installed, you can run the htopcommand:
$htop
As you can see in Figure 1.15, we're running Nmap in another terminal window, and it has a process ID (PID) equal to 1338.
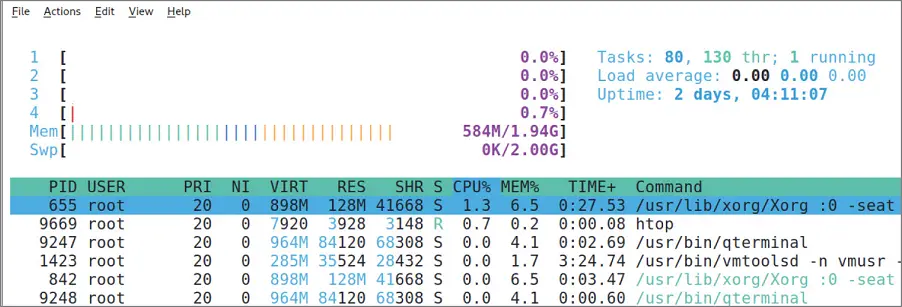
Figure 1.15HTOP
Another way to get the list of currently running processes is by using the pscommand:
$ps -Au -A: To select all the processes (if you want to list only the processes that belongs to the current user then use the -x option instead) -u: shows more info (e.g., CPU, MEM, etc) than the default output
To kill a process, you will need to identify its PID first; then you can use the killcommand to get the job done:
$kill [PID]
If the system doesn't allow you to kill it, then you must force it to close using the ‐9switch:
$kill -9 [PID]
In this section, you will get the chance to understand the basics of networking in Kali Linux. Later in the book we will come back to more advanced topics regarding networking, so make sure to understand and grasp the contents in this section.

Figure 1.16 Kali Networking Commands
You must be a pro in networking to survive in the penetration testing career. It's one of the pillars of the job if you're going to execute network infrastructure penetration tests.
PC hosts have internal IP addresses to connect with the network, and they have a public IP address to communicate with the outside world. The latter is the mission of your home router, and you don't manage it locally on your localhost. On the other hand, you must maintain the internal network IP addresses, which are either static (you define it) or automatically assigned by a DHCP server (which is generally your home router).
IPv4 Private Address Ranges
Internal IP addresses (aka private IP addresses) for IPv4 have multiple ranges: classes A, B, and C.
Class A: 10.0.0.0 to 10.255.255.255 or 10.0.0.0/8 (up to 16,777,214 hosts)
Class B: 172.16.0.0 to 172.31.255.255 or 172.16.0.0/12 (up to 1,048,574 hosts)
Class C: 192.168.0.0 to 192.168.255.255 or 192.168.0.0/24 (up to 254 hosts)
The biggest range is class A for corporations, but you can use it at home. (No one will stop you from doing that, and guess what? I use it myself for my home network.) The second, class B, is for small/midrange/big companies (depending on the number of hosts). The third is class C; this range is limited but is suitable for home users and small office/home office (SOHO) environments.
Let's take a quick look at our Kali host IP address. To get the information about our network interface, execute the popular ifconfigcommand (take note that there has been a shift to use the ip addrcommand lately instead of ifconfig).
According to Figure 1.17, we have two network interfaces. The first one on the top, eth0, is the Ethernet adapter that connects my Kali host with the internal network. If we had a second Ethernet adapter, it would be eth1. (Take note that if you're using a wireless adapter on your host, then you will see wlan0, wlan1, etc.)
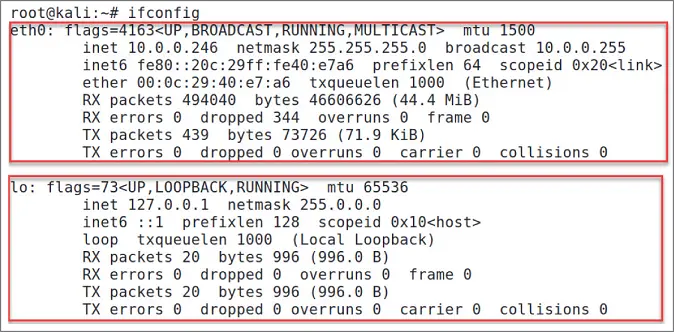
Figure 1.17Kali Network Interfaces
There are two important facts to understand about our Ethernet adapter eth0. First, inet 10.0.0.246represents the Kali host IP address that was assigned automatically by the DHCP server. The second part is the netmask, which means that we're using a /24 subnet; in other words, we only need 254 hosts to be assigned on this IP range.
The second interface is lo, which represents a local loopback; you will never touch this since the network infrastructure will need it to operate correctly.
There are two common other interfaces that you will encounter; the first one is the wireless interface if you're connected wirelessly instead of the wire. The second is the VPN interface, if you're connected to a remote VPN server.
If you want to assign a fixed IP address to your Kali host, you will need to edit the configuration file /etc/network/interfaces. In the following new configuration, shown in Figure 1.18, add these three main components:
Static IP address (it's going to be 10.0.0.20 in my case; in your case, it has to match your private IP address range)
Subnetmask or CIDR (/24 means 255.255.255.0)
Router/gateway IP address (my router IP address is 10.0.0.1; yours could be different)
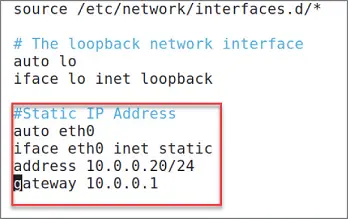
Figure 1.18Static IP Configs
After you save your changes, make sure to reboot your Kali machine to get this new fixed IP address up and running. To test the connectivity to the outside world (after rebooting), try to ping the popular Google's DNS server on 8.8.8.8 (if for any reason you want to reverse your changes, just go back to the config file and remove/comment the new lines), as shown in Figure 1.19.
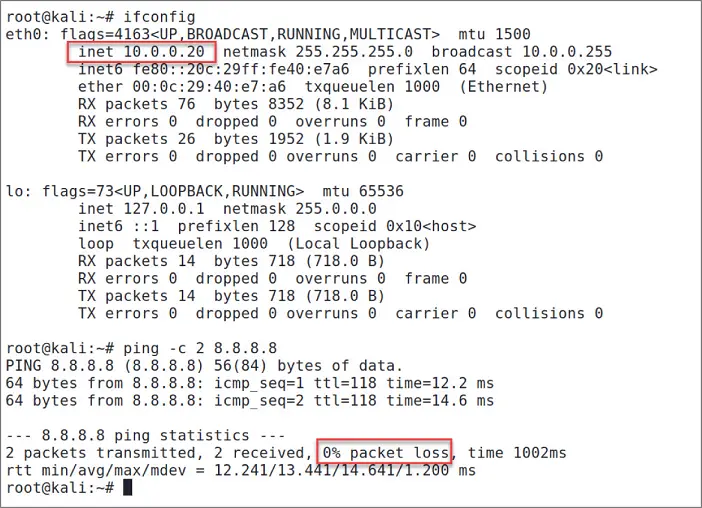
Figure 1.19Testing Internet Connection
Take note that we're using 10.0.0.0 network as our main VLAN (virtual network). In fact, we have multiple VLANs in our home network. For example, we have a VLAN for IoT devices, but why? It's because we want IoT devices to be on a separate network (10.0.50.0/24) without interfering with my main production hosts.
Another example is the Guests VLAN. This network is for people who connect to the wireless guest access point, and they will be assigned in the 10.0.20.0 address range.
Companies implement the same concept. Ideally, they have a development environment that is different than the production environment network VLAN.
The Domain Name System (DNS) translates domain names into IP addresses. For example, instead of typing https://172.217.13.132, you simply type https://google.com. The question is, how did I come up with the IP address? Use the hostcommand on your terminal window:
Читать дальше

















