Understanding the commands for managing users and groups is important because you'll use the information when you learn about privilege escalation later in the book. All the commands in this chapter will help you a lot in your engagements while using Kali Linux (as an OS for your pentests).
Figure 1.5summarizes all the commands related to users' management/security in Kali Linux.
Low‐privilege users must prepend commands with sudoto execute system commands (and the low‐privilege user must be in the sudogroup to execute sudo). You will be asked for your account password if you want to use the sudocommand. For example, if you want to execute the fdisksystem tool to show the Kali‐attached devices, use the following command:
root@kali:~# fdisk -l Disk /dev/sda: 80 GiB, 85899345920 bytes, 167772160 sectors Disk model: VMware Virtual S Units: sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disklabel type: dos Disk identifier: 0x7c02676c Device Boot Start End Sectors Size Id Type /dev/sda1 * 2048 165771263 165769216 79G 83 Linux /dev/sda2 165773310 167770111 1996802 975M 5 Extended /dev/sda5 165773312 167770111 1996800 975M 82 Linux swap / Solaris 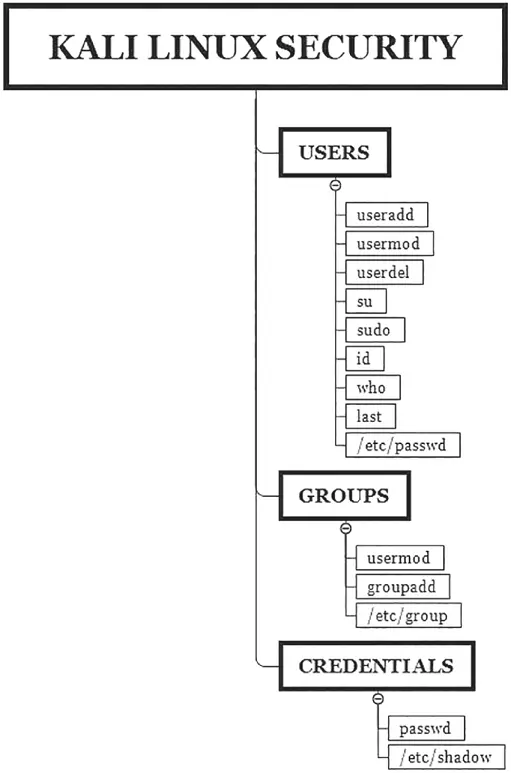
Figure 1.5Kali Linux OS Security Commands
To add a new user to Kali (in this example, Gus is going to be the user), use the useraddcommand. Along with it you need to choose the sudogroup with the ‐Goption and the shell type with the ‐soption:
$useradd -m [user name] -G [group name] -s [shell type]
For our example, it looks like this:
root@kali:~# useradd -m Gus -G sudo -s /bin/bash
Next, let's give the new user a password using the passwdcommand:
$passwd [user name - that you want to change password]
Here's how it looks in the terminal window:
root@kali:~# passwd Gus New password: Retype new password: passwd: password updated successfully
If you look closely at the top left, it's written root@kali; I know that this is confusing, but the structure of this part is in the following format:
username@hostname
To switch to the new user Gus that we created previously, we use the sucommand (pay attention to how the user has changed in the terminal window text and turned into Gus@kali):
$su [user name – that you want to switch to] root@kali:~# su Gus Gus@kali:/root$
To learn the capabilities of the current user with the sudocommand, you need to execute sudo ‐lto get the correct information:
Gus@kali:~$ sudo -l We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for Gus: Matching Defaults entries for Gus on kali: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User Gus may run the following commands on kali: (ALL : ALL) ALL
To view the current user information, use the idcommand:
Gus@kali:~$ id uid=1001(Gus) gid=1001(Gus) groups=1001(Gus),27(sudo)
To list the currently logged on users, use wor who(with fewer details):
Gus@kali:~$ w 10:44:06 up 19 min, 1 user, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT root tty7 :0 10:24 19:55 2.36s 2.36s /usr/lib/x Gus@kali:~$ who root tty7 2020-09-22 10:24 (:0)
To remove a user (the user that we will remove in this example is test), execute the userdelcommand:
$userdel [user name – that you want to delete] Gus@kali:~$ sudo userdel test
To list the last logged in users in the Kali system, use the lastcommand:
Gus@kali:~$ last root tty7 :0 Tue Sep 22 10:24 still logged in reboot system boot 5.7.0-kali1-amd6 Tue Sep 22 10:24 still running root tty8 :1 Tue Sep 22 10:21 - 10:23 (00:02) kali pts/1 tmux(1793).%0 Mon Sep 21 12:16 - 10:23 (22:07) kali pts/2 tmux(1584).%0 Mon Sep 21 11:48 - 11:48 (00:00) kali tty7 :0 Mon Sep 21 10:50 - 10:23 (23:33) reboot system boot 5.7.0-kali1-amd6 Mon Sep 21 10:50 - 10:23 (23:33) kali tty7 :0 Mon Jul 27 13:36 - 15:56 (02:20) reboot system boot 5.7.0-kali1-amd6 Mon Jul 27 13:36 - 15:57 (02:20) kali tty7 :0 Mon Jul 27 13:31 - crash (00:05) reboot system boot 5.7.0-kali1-amd6 Mon Jul 27 13:30 - 15:57 (02:26) kali tty7 :0 Mon Jul 27 13:28 - crash (00:02) reboot system boot 5.7.0-kali1-amd6 Mon Jul 27 13:28 - 15:57 (02:28) wtmp begins Mon Jul 27 13:28:09 2020
Finally, take note that all the users in Kali are stored in a configuration file, /etc/passwd. Use the catcommand to reveal its contents:
Gus@kali:~$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin
The previous command will list all the users, even the system ones (the example just shows the first three). To filter the contents and limit the results for the human users, pipe the output using |in the grepcommand:
Gus@kali:~$ cat /etc/passwd | grep "/bin/bash" root:x:0:0:root:/root:/bin/bash postgres:x:119:124:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash kali:x:1000:1000:kali,,,:/home/kali:/bin/bash Gus:x:1001:1001::/home/Gus:/bin/bash
To add a new group in Kali Linux, use the groupaddcommand:
$groupadd [new group name] Gus@kali:~$ sudo groupadd hackers
To join a user (which is Gus for this example) to the hackersgroup that we created earlier, execute the usermodcommand:
$usermod -aG [group name] [user name] Gus@kali:~$ sudo usermod -aG hackers Gus
To list all the groups created in Kali Linux, open the file /etc/group. Again, use the catcommand to get the job done (the following example shows only the first three):
Gus@kali:~$ cat /etc/group root:x:0: daemon:x:1: bin:x:2: […] hackers:x:1002:Gus
Managing Passwords in Kali
You probably want your root user back like in the old days. To get this account back, you will need to set its password first. To change a user password, you have to use the passwdcommand:
Gus@kali:~$ sudo passwd root New password: Retype new password: passwd: password updated successfully
Now to use the powerful root account, you have to use the sucommand to switch user:
Gus@kali:~$ sudo su root root@kali:/home/Gus#
From now on, on the login screen, you can choose your root account instead of your nonroot user.
Finally, to list all the user's credentials in Kali Linux, you can reveal them in the file /etc/shadow. Use the grepcommand to get the user credentials for Gus:
root@kali:/# cat /etc/shadow | grep "Gus" Gus:$6$Hb.QBfIoaCBTiqK$EUJ4ZdWmbsFqHMsPbMEz2df6FtWVf4J/tMulxCoLQmfMlVWyqpMUHBGmHFulRknYHgSrFIF.hQTANgzJ6CQM8/:18527:0:99999:7:::
Let's simplify what you need to understand from the string. The delimiter that separates each section is the colon character (:).
Second, the $6$means that the password is hashed using SHA‐512. Finally, the hashed password starts after $6$and right before the : delimiter:
Hb.QBfIoaCBTiqK$EUJ4ZdWmbsFqHMsPbMEz2df6FtWVf4J/tMulxCoLQmfMlVWyqpMUHBGmHFulRknYHgSrFIF.hQTANgzJ6CQM8/
Читать дальше













