The process of quantitative risk analysis starts with asset valuation and threat identification (which can be performed in any order). This results in asset-threat pairings that need to have estimations of harm potential/severity and frequency/likelihood assigned or determined. This information is then used to calculate various cost functions that are used to evaluate safeguards.
The major steps or phases in quantitative risk analysis are as follows (see Figure 2.3, with terms and concepts defined after this list of steps):
1 Inventory assets, and assign a value (asset value [AV]).
2 Research each asset, and produce a list of all possible threats to each individual asset. This results in asset-threat pairings.
3 For each asset-threat pairing, calculate the exposure factor (EF).
4 Calculate the single loss expectancy (SLE) for each asset-threat pairing.
5 Perform a threat analysis to calculate the likelihood of each threat being realized within a single year—that is, the annualized rate of occurrence (ARO).
6 Derive the overall loss potential per threat by calculating the annualized loss expectancy (ALE).
7 Research countermeasures for each threat, and then calculate the changes to ARO, EF, and ALE based on an applied countermeasure.
8 Perform a cost/benefit analysis of each countermeasure for each threat for each asset. Select the most appropriate response to each threat.
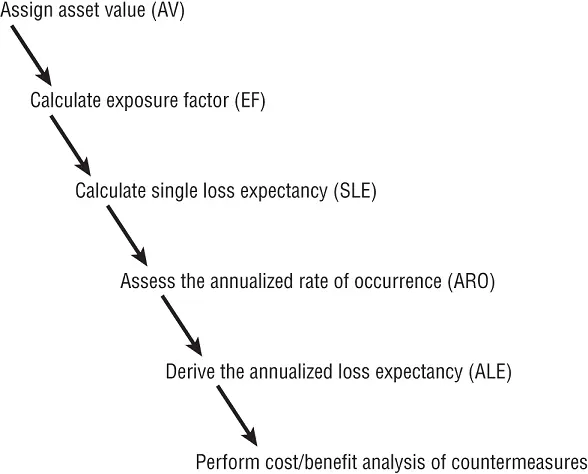
FIGURE 2.3The six major elements of quantitative risk analysis
The cost functions associated with quantitative risk analysis include the following:
Exposure Factor The exposure factor (EF) represents the percentage of loss that an organization would experience if a specific asset were violated by a realized risk. The EF can also be called the loss potential. In most cases, a realized risk does not result in the total loss of an asset. The EF simply indicates the expected overall asset value loss because of a single realized risk. The EF is usually small for assets that are easily replaceable, such as hardware. It can be very large for assets that are irreplaceable or proprietary, such as product designs or a database of customers. The EF is expressed as a percentage. The EF is determined by using historical internal data, performing statistical analysis, consulting public or subscription risk ledgers/registers, working with consultants, or using a risk management software solution.
Single-Loss Expectancy The single-loss expectancy (SLE) is the potential loss associated with a single realized threat against a specific asset. It indicates the potential amount of loss an organization would or could experience if an asset were harmed by a specific threat occurring.The SLE is calculated using the following formula:SLE = asset value (AV) * exposure factor (EF)or more simply:SLE = AV * EFThe SLE is expressed in a dollar value. For example, if an asset is valued at $200,000 and it has an EF of 45 percent for a specific threat, then the SLE of the threat for that asset is $90,000. It is not always necessary to calculate an SLE, as the ALE is the most commonly needed value in determining criticality prioritization. Thus, sometimes during risk calculation, SLE may be skipped entirely.
Annualized Rate of Occurrence The annualized rate of occurrence (ARO) is the expected frequency with which a specific threat or risk will occur (that is, become realized) within a single year. The ARO can range from a value of 0.0 (zero), indicating that the threat or risk will never be realized, to a very large number, indicating that the threat or risk occurs often. Calculating the ARO can be complicated. It can be derived by reviewing historical internal data, performing statistical analysis, consulting public or subscription risk ledgers/registers, working with consultants, or using a risk management software solution. The ARO for some threats or risks is calculated by multiplying the likelihood of a single occurrence by the number of users who could initiate the threat. ARO is also known as a probability determination. Here's an example: the ARO of an earthquake in Tulsa may be .00001, whereas the ARO of an earthquake in San Francisco may be .03 (for a 6.7+ magnitude), or you can compare the ARO of an earthquake in Tulsa of .00001 to the ARO of an email virus in an office in Tulsa of 10,000,000.
Annualized Loss Expectancy The annualized loss expectancy (ALE) is the possible yearly loss of all instances of a specific realized threat against a specific asset. The ALE is calculated using the following formula:ALE = single loss expectancy (SLE) * annualized rate of occurrence (ARO)orALE = asset value (AV) * exposure factor (EF) * annualized rate of occurrence (ARO)or more simply:ALE = SLE * AROorALE = AV * EF * AROFor example, if the SLE of an asset is $90,000 and the ARO for a specific threat (such as total power loss) is .5, then the ALE is $45,000. If the ARO for a specific threat (such as compromised user account) is 15 for the same asset, then the ALE would be $1,350,000.
The task of calculating EF, SLE, ARO, and ALE for every asset and every threat/risk is a daunting one. Fortunately, quantitative risk assessment software tools can simplify and automate much of this process. These tools produce an asset inventory with valuations and then, using predefined AROs along with some customizing options (industry, geography, IT components, and so on), produce risk analysis reports.
Once an ALE is calculated for each asset-threat pairing, then the entire collection should be sorted from largest ALE to smallest. Although the actual number of the ALE is not an absolute number (it is an amalgamation of intangible and tangible value multiplied by a future prediction of loss multiplied by a future prediction of likelihood), it does have relative value. The largest ALE is the biggest problem the organization is facing and thus the first risk to be addressed in risk response.
The “Cost vs. Benefit of Security Controls” section, later in this chapter, discusses the various formulas associated with quantitative risk analysis that you should be familiar with.
Both the quantitative and qualitative risk analysis mechanisms offer useful results. However, each technique involves a unique method of evaluating the same set of assets and risks. Prudent due care requires that both methods be employed in order to obtain a balanced perspective on risk. Table 2.1describes the benefits and disadvantages of these two systems.
TABLE 2.1Comparison of quantitative and qualitative risk analysis
| Characteristic |
Qualitative |
Quantitative |
| Employs math functions |
No |
Yes |
| Uses cost/benefit analysis |
May |
Yes |
| Requires estimation |
Yes |
Some |
| Supports automation |
No |
Yes |
| Involves a high volume of information |
No |
Yes |
| Is objective |
Less so |
More so |
| Relies substantially on opinion |
Yes |
No |
| Requires significant time and effort |
Sometimes |
Yes |
| Offers useful and meaningful results |
Yes |
Yes |
At this point, the risk management process shifts from risk assessment to risk response. Risk assessment is used to identify the risks and set criticality priorities, and then risk response is used to determine the best defense for each identified risk.
Whether a quantitative or qualitative risk assessment was performed, there are many elements of risk response that apply equally to both approaches. Once the risk analysis is complete, management must address each specific risk. There are several possible responses to risk:
Читать дальше













