Attack An attack is the intentional attempted exploitation of a vulnerability by a threat agent to cause damage, loss, or disclosure of assets. An attack can also be viewed as any violation or failure to adhere to an organization's security policy. A malicious event does not need to succeed in violating security to be considered an attack.
Breach A breach, intrusion, or penetration is the occurrence of a security mechanism being bypassed or thwarted by a threat agent. A breach is a successful attack.
Some of these risk terms and elements are clearly related, as shown in Figure 2.2. Threats exploit vulnerabilities, which results in exposure. Exposure is risk, and risk is mitigated by safeguards. Safeguards protect assets that are endangered by threats.
There are many approaches to risk assessment. Some are initiated by evaluating threats, whereas others focus first on assets. Whether a risk assessment starts with inventorying threats, then looks for assets that could be harmed, or starts with inventorying assets, then looks for threats that could cause harm, both approaches result in asset-threat pairings that then need to be risk evaluated. Both approaches have merit, and organizations should shift or alternate their risk assessment processes between these methods. When focusing first on threats, a broader range of harmful issues may be considered, without being limited to the context of the assets. But this may result in the collection of information about threats that the organization does not need to worry about as they don't have the assets or vulnerabilities that the threat focuses on. When focusing first on assets, the entirety of organizational resources can be discovered without being limited to the context of the threat list. But this may result in spending time evaluating assets of very low value and low risk (which would or will be defined as acceptable risk), which may increase the overall time involved in risk assessment.
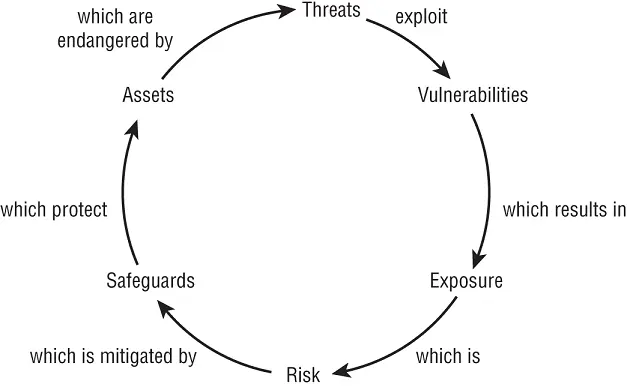
FIGURE 2.2The cyclical relationships of risk elements
The general idea of a threat-based risk assessment was discussed in Chapter 1. The discussion of risk assessment in this chapter will focus on an asset-based risk assessment approach.
An asset-based or asset-initiated risk analysis starts with inventorying all organizational assets. Once that inventory is complete, a valuation needs to be assigned to each asset. The evaluation or appraisal of each asset helps establish its importance or criticality to the business operations. If an asset has no value, there is no need to provide protection for it. A primary goal of risk analysis is to ensure that only cost-effective safeguards are deployed. It makes no sense to spend $100,000 protecting an asset that is worth only $1,000. Therefore, the value of an asset directly affects and guides the level of safeguards and security deployed to protect it. As a rule, the annual costs of safeguards should not exceed the potential annual cost of asset value loss.
When the cost of an asset is evaluated, there are many aspects to consider. The goal of asset valuation is to assign to an asset a specific dollar value that encompasses tangible costs as well as intangible ones. Determining an exact value of an asset is often difficult if not impossible, but nevertheless, a specific value must be established in order to perform quantitative mathematical calculations. (Note that the discussion of qualitative versus quantitative risk analysis later in this chapter may clarify this issue; see the “Risk Assessment/Analysis” section.) Improperly assigning value to assets can result in failing to properly protect an asset or implementing financially infeasible safeguards. The following list includes tangible and intangible issues that contribute to the valuation of assets:
Purchase cost
Development cost
Administrative or management cost
Maintenance or upkeep cost
Cost in acquiring asset
Cost to protect or sustain asset
Value to owners and users
Value to competitors
Intellectual property or equity value
Market valuation (sustainable price)
Replacement cost
Productivity enhancement or degradation
Operational costs of asset presence and loss
Liability of asset loss
Usefulness
Relationship to research and development
Assigning or determining the value of assets to an organization can fulfill numerous requirements by
Serving as the foundation for performing a cost/benefit analysis of asset protection when performing safeguard selection
Serving as a means for evaluating the cost-effectiveness of safeguards and countermeasures
Providing values for insurance purposes and establishing an overall net worth or net value for the organization
Helping senior management understand exactly what is at risk within the organization
Preventing negligence of due care/due diligence and encouraging compliance with legal requirements, industry regulations, and internal security policies
If a threat-based or threat-initiated risk analysis is being performed, then after the organization inventories threats and identifies vulnerable assets to those threats, asset valuation takes place.
Identify Threats and Vulnerabilities
An essential part of risk management is identifying and examining threats. This involves creating an exhaustive list of all possible threats for the organization's identified assets. The list should include threat agents as well as threat events. Keep in mind that threats can come from anywhere. Threats to IT are not limited to IT sources or concepts. When compiling a list of threats, be sure to consider threats from a wide range of sources.
For an expansive and formal list of threat examples, concepts, and categories, consult National Institute of Standards and Technology (NIST) Special Publication (SP) 800-30r1 Appendix D, “Threat sources,” and Appendix E, “Threat events.” For coverage of threat modeling, see Chapter 1.
In most cases, a team rather than a single individual should perform risk assessment and analysis. Also, the team members should be from various departments within the organization. It is not usually a requirement that all team members be security professionals or even network/system administrators. The diversity of the team based on the demographics of the organization will help exhaustively identify and address all possible threats and risks.
Risk assessment is a highly involved, detailed, complex, and lengthy process. Often risk analysis cannot be properly handled by existing employees because of the size, scope, or liability of the risk; thus, many organizations bring in risk management consultants to perform this work. This provides a high level of expertise, does not bog down employees, and can be a more reliable measurement of real-world risk. But even risk management consultants do not perform risk assessment and analysis on paper only; they typically employ risk assessment software. This software streamlines the overall task, provides more reliable results, and produces standardized reports that are acceptable to insurance companies, boards of directors, and so on.
Risk management is primarily the responsibility of upper management. However, upper management typically assigns the actual task of risk analyses and risk response modeling to a team from the IT and security departments. The results of their work will be submitted as a proposal to upper management, who will make the final decisions as to which responses are implemented by the organization.
Читать дальше













