and your [PC] will stop functioning normally…
You are strictly prohibited from sharing [this product] with others…”
Just like today, most people didn't read software license agreements. Normally it's not a problem, but in this case not reading the license agreement with its unusual dire warning would take on special importance. In the late 1980's, a large percentage of users also didn't pay for any commercial software they were not forced to pay for. Software was routinely illegally copied and traded. It was incredibly common for people to copy disks for their friends or even sell (even if they hadn't paid the original developer). Local computer clubs held monthly disk swaps. If you didn't have to pay for software, you didn't. In response, some developers created “copy protection” routines that prevented easy, standard disk copying.
The author has seen other malicious programs and sites include similar “fair warnings” in their licensing information. It never hurts to read your end-user license agreements instead of simply trying your best to ignore and quickly get by them.
Dr. Popp either didn't know how to do legitimate copy protection or he counted singularly on his peculiar ransom enforcement for people who ignored his licensing instructions. Maybe he got the idea from an earlier malware program. In 1986, the first IBM PC-compatible computer virus, Pakistani Brain ( https://en.wikipedia.org/wiki/Brain_(computer_virus)), was created as a copy prevention mechanism. Its Pakistani creators were tired of people illegally copying without paying for disks they had themselves often illegally copied. You can't make this stuff up. It caused boot problems and indirectly might have caused some people to pay money to the inventors to resolve. The malware, however, did not encrypt anything nor directly ask for a ransom.
There is a chance that Dr. Popp saw his ransomware program as simply a way to legally enforce his copyright and software license. There were warnings in at least two places clearly visible to users who used his software. In comparison, today's ransomware programs never give any warning. So perhaps, in only that way, Dr. Popp's creation was a slight bit more ethical than today's ransomware programs. But being a slight bit more ethical criminal among more unethical criminals is not a particularly high standard that anyone should want to be measured against.
Either way, the first time Dr. Popp's program was run by a user, it would install itself on the local hard drive (C:) and modify the autoexec.batfile to use as a boot counter. After the involved PC was booted 90 or so times, the program would encrypt/obfuscate the user's files and folders. It would then display the message shown in Figure I.3.
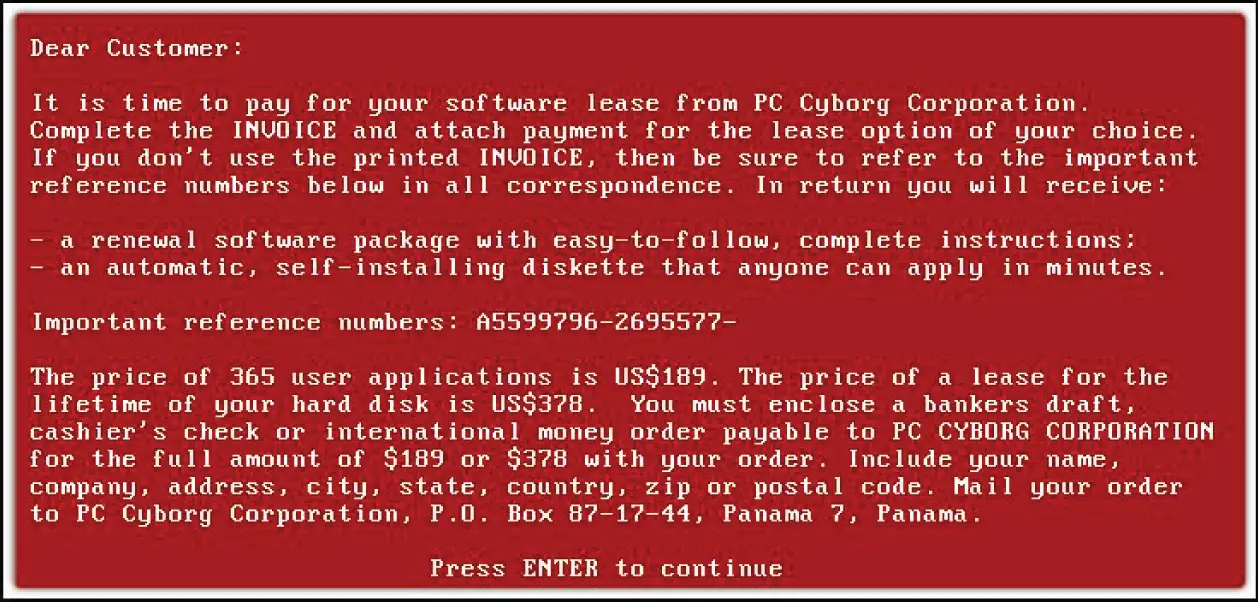
Figure I.3Picture of AIDS PC Cyborg Trojan ransomware screen instructions
Courtesy Wikipedia
No one knows why Dr. Popp put his trigger counter at 90. Perhaps he estimated that most people booted their PCs about once a day during the work week, and 90 workdays was more than enough time for someone to send payment for their program and for him to return a “block the lock” executable disk.
Dr. Popp had created a company with the name of PC Cyborg, which would lead to the naming of the virus. The name was shown in the original license and in the after-the-fact ransomware warning, along with asking for $189 for an annual “license” or $389 for a “lifetime license” to be sent to a Panama post-office box. It was this information that led to his quick identification and arrest. Today's ransomware purveyors use hard-to-identify-true-ownership cryptocurrencies to avoid the same easy identification and detection by authorities.
Dr. Popp had clearly tried to hide his identity and original involvement with his creation. As is still true today, it is common for unethical people trying to hide their identity and financial gains to use offshore corporations and accounts. At that time, Panama was popularly used as a financial and tax avoidance safe haven much as the Cayman Islands and other offshore islands are used today.
When the trojan's program payload ran, before the ransom instructions were shown, it did some rudimentary symmetric encryption to the files and folders. It would move all the existing files and subdirectories into a new set of subdirectories under the root directory, rename them, and enable DOS' “hidden” attribute features on each file and folder, which made them seem to disappear. All the files and folders would also be renamed using “high-order” extended ASCII control characters, which made everything appear as being invisible. Even if the DOS hidden attribute was discovered and turned off, the file and folder names looked corrupted. If the impacted user tried to do some common exploratory commands to see what happened, the malicious code brought back a fake DOS screen with fake results to confuse the user.
The main set of malicious subdirectories were created using extended ASCII character 255, which is a control code that looks like a space even though it is not. But like a space, it would not display on the screen or when printed. For all intents and purposes, all the files and folders appeared, to most users, to have disappeared or at least badly corrupted. But, importantly, none of the files were actually encrypted (unlike today's ransomware programs). The names of the files and folders were just renamed and moved.
The ransomware program created a conversion table that could be used to reverse the moving and renaming. If you found the table and understood what the trojan program did, you could convert everything back to the original file and folder names and locations. Several individuals figured this out and wrote “fix-it” programs, including early computer virus expert Jim Bates.
Bates created a free 40-page analysis report of the trojan that he would send to anyone who requested it, and he published a shorter, but still great, analysis in the premier antivirus journal Virus Bulletin ( https://www.virusbulletin.com/uploads/pdf/magazine/1990/199001.pdf.) in January 1990. Bates revealed the many dubious routines of the program including the multiple steps it took to fake what the user saw when investigating. It was a great example of the antivirus and online community coming together to defeat a common foe without thinking about profit.
The PC Cyborg ransomware encryption routine used what cryptographers called simple character substitution for the encryption component. This is the absolute simplest type of encryption possible, and because of that, it's probably more accurate to call Dr. Popp's encryption routine obfuscation instead. It certainly wasn't anything close to as secure as how most digital encryption had been accomplished on computers for at least a decade before Dr. Popp's program, and much less sophisticated compared to encryption in today's ransomware variants. But the point is mostly semantic. To most victims, their data was gone and their computers were unusable.
Along with his detailed analysis, Bates created a free trojan removal program called AIDSOUT and a free AIDSCLEAR program that would restore any renamed and moved files to their original locations and names. The late John McAfee, of McAfee Antivirus fame, gained some early national media attention in the United States by talking about the ransomware program and by saying he went around rescuing people's locked-up PCs.
It was the publicity surrounding John McAfee's computer virus recoveries during that time that led this author to disassembling DOS computer viruses for John McAfee later that year and largely led to the author's lifetime career in cybersecurity.
Читать дальше













