Cloud Computing provides the services of both service oriented and event driven architecture.
The given diagram represents the various services of the cloud. All services are inter-related to each other. The three main parties involved are the cloud service consumer, cloud service provider, and cloud broker shown in Figure 2.1.
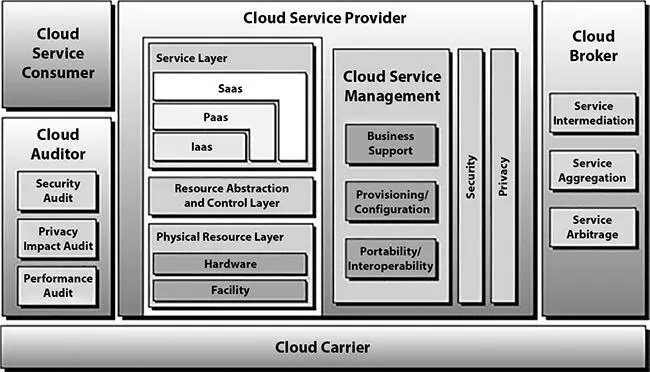
Figure 2.1 Cloud computing services [3].
In cloud service, all consumer services are provided if the consumer belongs internally or, if the consumer belongs externally, it depends on the consumer requirement. At the time of consumer requirement, the service provides, as the diagram represents, the work of a cloud auditor.
The cloud service provider provides all cloud services. Whether the type of service provided by the service provider is commercial or corporate is decided by the service provider [3].
The cloud service provider can provide all services with physical or virtual resources that provide the cloud service and create applications according the requirement of services. All groups work together as a service orchestration.
2.2.2 Concept of Multi-Tenancy
The basic concept of Multi-Tenancy is required when many tenants work together with the use of internet and data can be transferred using digital services if the tenants are in different places; the concept is to work from one place to another place. This service totally depends on the needs of the organisation. The requirement of tenants and which type or place the tenant requires is up to the organisation’s needs [4].
Basically, there are two types of tenancy in an SaaS environment: Single and Multi-Tenancy. Figure 2.2briefly discusses Multi-Tenancy’s use in real time application. In Single Tenancy, a single environment or platform is used, but in Multi-Tenancy, a common platform is used in different places or shares the platform of work and creates a known work place for a single organisation.
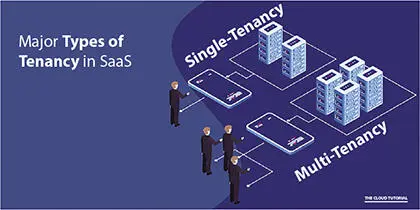
Figure 2.2 Types of tenant [4].
A Single Tenant service uses a single system (software) for a single tenant for one service. A single system service provides for a single building, but if its requirement is in a different building, the tenant needs to purchase again for the new building for the same services. In Multi-Tenancy, the client is not required to purchase a single service multiple times, which means single services can be used in different offices of a single organisation.
In a Multi-Tenancy system, it is easy to modify and make changes as required by the tenant. Multi-Tenant systems combine the work place between the client and the tenant, but the concept or logic should be separate to each other. The organisation shares the data and configurations, as well as services of management with the user and tenant [5].
There are basically three major concepts in Multi-Tenancy, as show in the Figure 2.2.
1 1. A shared database which is used to manage the Multi-Tenancy system means this facility helps make data available and manages the cost or storage area flexibility and scalability management. It reduces the complexity of managing the database and makes it easily available to each tenant and workspace.
2 2. One database and many schemas means all tenants use the same database in a different manner. Each tenant uses their requirement of data and every tenant requirement is different as the work is different. According the tenant, the services are provided to the tenant. The complexity and cost will also affect the structure used by the tenant.
3 3. Many databases and schemas means, in this type of model, that tenant data is stored in the database in different locations in a different database or that the tenant can create different databases as they are required. Accordingly, the new database will create a cost and complexity increase [6].
2.2.3 Concept of Multi-Tenancy with Cloud Computing
In the Cloud Computing system, the concept of Multi-Tenancy is very important because IT provides the facility to all tenants through shared computer resources in a cloud environment. The cloud environment has two types: a public cloud environment and a private cloud environment. The tenant chooses one of the cloud environments. All tenant data is isolated and inaccessible to each other shown in Figure 2.3.
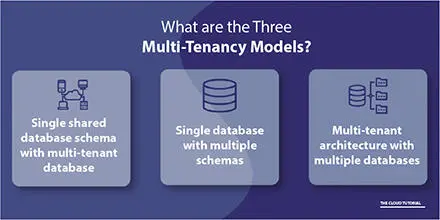
Figure 2.3 Multi-Tenancy models [5].
Multi-Tenancy cloud computing systems create a sparse work area for each tenant for storage or project data and login privacy policies. The tenant only uses their personal and secure area for work and accesses only know work or data. In the case of other requirements of data, another tenant’s permission or access key is required for access.
One type of cloud computing is in the private cloud environment and uses groups of more than two tenants belonging to a single company. They work on the same data and use resources through the cloud environment. The other type is the public cloud environment where many companies can share their data and services with different tenants. The public cloud environment is used more than the private cloud environment.
The Single Tenant Cloud Computing environment does not provide to all facilities. When compared to a Multi-Tenancy system, it provides more storage, access features, and security and privacy policies.
It provides a virtual environment for work easily, with less complexity maintaining work and hardware and no restrictions to devices or location [7].
Example of Multi-Tenancy with Cloud Computing:
Let us take a very common example of a colony. In a colony there are many houses; each house has many flats, each house is playing a role as part of a single company, each company has different departments, each department works only at their area, and each department shares common utility services (i.e. water, electricity, PNG etc.). Similar facilities are used by companies shown in Figure 2.4.
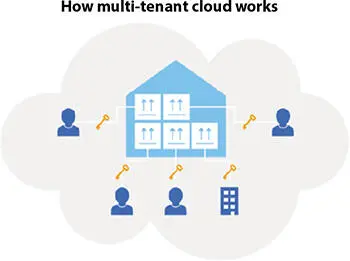
Figure 2.4 Multi-Tenant Cloud structure [6].
2.3 Privacy in Cloud Environment Using Deep Learning
In Multi-Tenant cloud based systems, security uses the Deep Learning Method to overcome all the requirements of a tenant, including privacy policies and services required. Using Deep Learning Methods for developing the privacy structure of Cloud Computing provides better services according to the requirements of a tenant. Accordingly, at the request of the tenant, resources and service availability fulfil requests and the privacy and security services are developed and maintained. In the cloud computing environment, there are public, private, single, and multi-tenant structures available to use according to the requirements of a tenant. Different structures have different needs for privacy and security services. If better services are not available, the tenant may not use the structure, therefore, using Deep Learning methods develops privacy and security services. The services are developed according to the organisation’s needs using Deep Learning [8].
Читать дальше
















