S. Ziyad (2014) proposes in a study an authentication that is secured by the amalgamation of biometrics and cryptography. Their system structure involves three phases, namely, the initialization phase, registration phase, and verification phase. At the time of registration, biometric data is obtained from the users, encrypted, and stored in a smart card. Each smart card contains an authentication number along with palm vein biometric data and other related information. During the verification phase, the data from the smart card is verified with template data in the database and if the data is verified and matched, then the connection with the server is established and the user can access the system [15].
Traditional systems apply the authentication process in one or various modes. A single-sign-on is a strategy that utilizes customary techniques for the user to access the system just a single time upon entering their identity, however, they can access different services at different levels. S. Bawaskar (2016), in her research paper, proposes an upgraded SSO based authentication framework based on a multi-factor concept. The authors suggest a continuous bit sequence of the oriented certificates utilizing greater management schemes. Accordingly, the framework is totally secured, taking into account the need of protection from malicious activities.
Facial acknowledgment is a classification of biometric programming that maps a person’s facial features mathematically and stores the information as a face print.
Here, we propose a model for application in criminal justice systems. The model suggests the capacity to perform face identification in a group continuously or post-occasion, for open security, in urban communities, air terminals, at fringes, or other sensitive spots like religious congregations. It can help law enforcement agencies in better identification of possible suspects.
First of all, facial detection technique is used to confirm whether the image given as input is a face or not. On being detected as a face, facial marking is done using fiducially point analysis.
We will access the database from the cloud and the personal recognition will use the feature vectors from the training images to train or learn the classification algorithm. Data mining algorithms will be used for further processing and evaluation of data. Feature selection and feature extraction techniques can be used for improved accuracy shown in Figure 1.3.
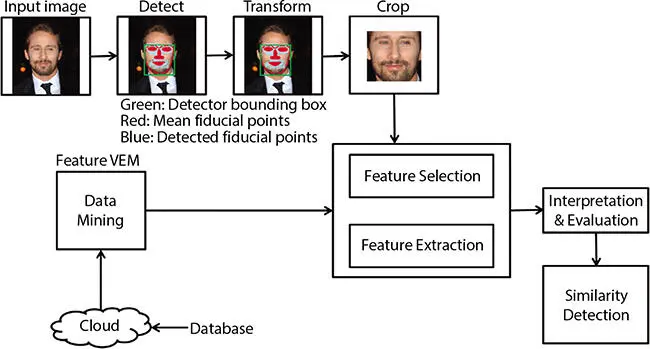
Figure 1.3 System architecture.
In the end, similarity detection is achieved by using the Nearest Neighbor Approach where the classifiers can be trained using a suitable algorithm like K-Nearest Neighbor.
STEPS:
1 1. An image captured is used as input.
2 2. Detect the image using fiducially points.
3 3. Transform the image by cropping the subsequent markers.
4 4. Apply Feature Selection and Feature Extraction for improved accuracy.
5 5. Use the Feature Vector Extraction method requiring features offloaded from the criminal database on the cloud.
6 6. Interpret and evaluate by comparing the two data sets.
7 7. Use the Nearest Neighbor Approach to identify the similarities between two or more images.
Facial Recognition Technology is intended to operate at a distance, without the knowledge of the target, so that it becomes hard to prevent the face from being captured. Along these lines, it allows for targeting of multiple persons one after another. Moreover, it is a non-consensual and clandestine reconnaissance innovation. The proposed model, when brought to realization, could act as an effective tool for criminal identification by comparing a live capture or digital image to the stored face print in order to confirm an individual’s identity.
Biometrics pose danger to individual rights and privacy since technologies like facial recognition allow identification of citizens without their acknowledgement. Moreover, when consent is backed into the design of the technology, the privacy concerns regarding biometrics could be addressed [16].
Any modern technology is laden with concealed threats with no claim of infallibility either by the software maker, person selling it, or the one who advocates its deployment. In the context of criminal justice administration research, it indicates that images captured with default camera settings preferably expose fair complexion rather than dark, affecting results of Facial Recognition Technology across racial groups. One methodology might be to utilize a technology-neutral regulatory framework that identifies degrees of damages.
Biometric technologies have wide-ranging applications. They are being increasingly used every day for phone security, banks, and governments looking towards these technologies as security measures for verifying transactions. Important government organizations are using facial recognition technology to create databases using driver’s license and passport details for effective administration, socio-economic development, and law enforcement. The thought that refined innovation implies more prominent proficiency should be fundamentally dissected. As these technologies penetrate more and more into our everyday lives, it is imperative to know and be educated about them. A reasonable strategy with ample safeguards for data protection and privacy is the need of the hour.
1. A.K. Jain and K. Nandakumar, “Biometric Authentication: System Security and User Privacy, “IEEE Published by the IEEE Computer Society, 00189162/12, Nov 2012.
2. Abhishek Kumar & Jyotir Moy Chatterjee & Pramod Singh Rathore, 2020. “Smartphone Confrontational Applications and Security Issues,” International Journal of Risk and Contingency Management (IJRCM), IGI Global, vol. 9(2), pages 1-18, April.
3. Bhargava, N., Bhargava, R., Rathore, P. S., & Kumar, A. (2020). Texture Recognition Using Gabor Filter for Extracting Feature Vectors With the Regression Mining Algorithm. International Journal of Risk and Contingency Management (IJRCM), 9(3), 31-44. doi:10.4018/IJRCM.2020070103.
4. Chandra Shekharv Vorugunti, “A Secure and efficient Biometric Authentication as a service for cloud computing,” 1 IEEE, October 09-11, 2014.
5. G.R Mettu and A. Patil, “Data Breaches as top Security concerns in Cloud Computing”, International Journal of Pure and Applied Mathematics, 119(14):19-27,2018.
6. Haryatibinti Jaafar, Nordianabinti, Mukahar, Dzati Athiarbinti Ramli “A Methodology of Nearest Neighbor: Design and Comparison of Biometric Image Database” IEEE Student Conference on Research and Development, 2016.
7. Indu, P.M Rubesh Anand and V.Bhaskar, “Identity and Access management in Cloud Environment :Mechanisms and Challenges,” Elsevier Engineering Science and Technology, an International Journal 21 (2018) 574-588, 2018.
8. K Sarat Chand and Dr. B Kezia. Rani, “Biometric Authentication using SaaS in Cloud Computing,” International Research Journal of Engineering and Technology (IRJET), Volume: 05 Issue: 02, Feb-2018.
9. Kumar, A., Chatterjee, J. M., & Díaz, V. G. (2020). A novel hybrid approach of svm combined with nlp and probabilistic neural network for email phishing. International Journal of Electrical and Computer Engineering, 10(1), 486
10. N. Bhargava, S. Dayma, A. Kumar and P. Singh, “An approach for classification using simple CART algorithm in WEKA,” 2017 11th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, 2017, pp. 212–216, doi: 10.1109/ISCO.2017.7855983.
Читать дальше













