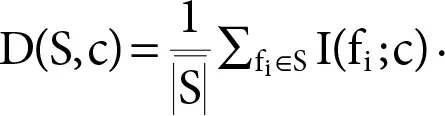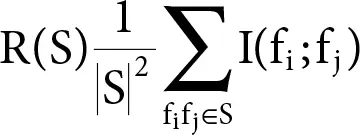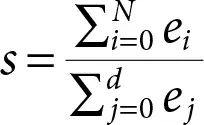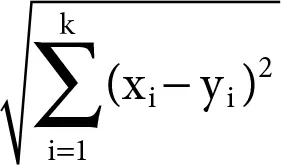Feature Selection selects the most relevant attributes by identifying the most pertinent characteristics and eliminating redundant information. A small size feature vector is used to reduce computational complexity, basic for online individual acknowledgment. Determination of effective features also helps increase precision [11]. Traditionally, large dimensions of feature vectors can be reduced using Principal Component Analysis (PCA) and Linear Discriminant Analysis (LDA).
The importance of a feature set S, for class c, is characterized by the normal estimation of all common data values between the individual feature f iand class c as follows:
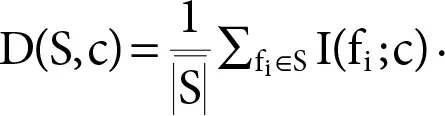
The repetition of all features in set S is the normal estimation of all common data values between feature f iand feature f j:
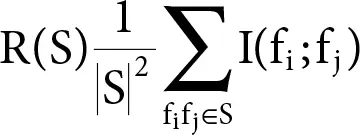
Feature extraction extracts distinct features from samples represented in a feature vector. Thus, alteration of attributes takes place in this method, whereas predictive significance criteria is used to rank the current attributes in feature selection technique. The altered features or attributes are linear aggregations of the original attributes. Since data is described by a lesser number of meaningful features, we obtain a higher quality model based on such derived attributes [12].
Feature extraction helps in data visualization by reducing a complex data set to 2 or 3 dimensions. It can improve the speed and efficiency of supervised learning. Feature extraction can also be used to enhance the speed and effectiveness of supervised learning. It has applications in data compression, data decomposition and projection, latent semantic analysis, and pattern recognition.
The information is extended onto the largest Eigen Vectors in order to reduce the dimensionality.
Let V = matrix with columns having the largest Eigen Vectors and
D = original data with columns of different observations.
Then, the projected data D′ is derived as D′ = V T D .
In the event when just N Eigen Vectors are kept and e1...eN represents the related Eigen Values, the amount of variance left after projecting the original d -dimensional data can be determined as:
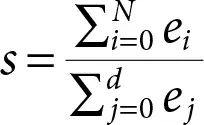
Facial land marking and facial feature detection are significant activities that influence ensuing assignments concentrated on the face, for example, gaze detection, coding, face acknowledgment, and demeanor, as well as understanding of gestures, face tracking, and so on and so forth.
Face landmarks like the nose tip, eye corners, end points of the eyebrow curves, jaw line, nostril corners, and ear projections can serve as anchor points on a face chart. A few Landmarks that are less influenced by expressions are more reliable can be termed as fiducially points. In imaging systems, fiducially points are treated as imprints intentionally positioned in the scene to function as a point of reference shown in Figure 1.2[13].
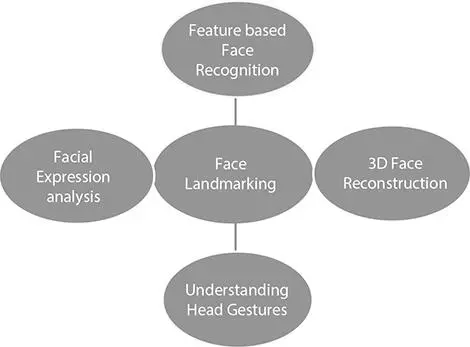
Figure 1.2 Applications of Face-Land marking [4].
Applications of Face-Land Marking
• Expression Understanding: Facial expressions can be analyzed by means of temporal dynamics and spatial arrangements of landmarks.
• Face Tracking: Number of facial factors are depicted on the face graph model. Face tracking is acknowledged by letting the model chart advance as per shape of face parameters, facial segments, and their mathematical relations.
• Face Recognition: Locating the region of the eye and extracting holistic features from the windows fixated on different focal points.
1.3.4 Nearest Neighbor Approach
KNN Algorithm: A non-parametric regression and classification algorithm based on the model structure generated from data without any assumptions of its own.
KNN is used for measuring similarities by vector representation and comparison using an acceptable distance metric in various domains of data processing, pattern recognition, and intrusion detection. KNN is called memory-based or lazy learning in light of the fact that the manner in which it learns is simply storing representations of the training examples. An object is classified depending on the majority votes of its neighbors in the training set. The new model item will be ascribed to the class with its most comparable K-Closest Neighbors.
For facial acknowledgment, we can select the face descriptors and use the K-Nearest Neighbors (KNN) calculation to train our classifier.
Euclidean Distance Function of K-Nearest Neighbor can be used for feature extraction:
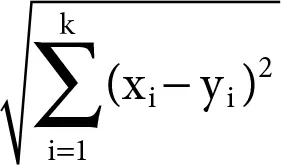
1.4 Related Work, A Review
P M Rubesh Anand (2018), along with other researchers, in his study, have done a complete analysis of the cloud environment and summed up the prevailing security threats in the cloud, conceivable outcomes, and alleviation in cloud administration with accentuation on access supervision, identity management, and services. Their research evaluates various facets with their commonly used techniques or mechanisms.
A K Jain (2012), in his research, sheds some light on the vulnerabilities of the biometric systems, the intrinsic limitations of the similarity of the any two biometrics, and its adversary effects. Unlike traditional authentication systems based on passwords, biometric authentications does not fully guarantee security.
A Patil (2018) in his paper discusses the security concerns of the cloud computing. Since cloud computing is a technology that delivers real time services, it is vulnerable to various kinds of data breaches. They discuss end to end communication through encryption, which would safeguard stolen information as the content would be encrypted and require security credentials [14].
To minimize, and ultimately beat, the dangers incorporated in the usage of customary strategies of authentication using PINs and passwords, a biometric framework for validation claimed to be more effective in controlling data breaches in cloud computing. In their research, they utilized an AES (Advanced Encryption Standard) algorithm for encrypting the data received from users at the time of enrollment and have devised another algorithm for the correlation of the user information with that of the layouts in the information database during authentication.
C S Vorugunti (2014) in his paper provides a simple and secure authentication system based on the SAAS model. It involves enrollment and verification as two steps of authentication. In the enrollment process, the biometric data is converted into a binary form. The feature extractor then converts the binary string into a set of features. In the verification process, the same feature will be processed when the user logins to the cloud. The process then verifies the cryptographic encryption and decryption operation on the users’ biometric data.
Читать дальше