The currently available algorithms are as follows:
• Eigenfaces (createEigenFaceRecognizer())
• Local Binary Patterns Histogram (createLBPHFaceRecog-nizer())
• Fisher faces (createFisherFaceRecognizer() )
This framework is controlled by Raspberry Pi circuit. Raspberry Pi electronic board is worked on battery power supply and remote web availability by utilizing USB modem; it incorporates camera, PIR movement sensor, LCD, and an entryway, as shown in Figure 1.4. At first approved countenances get enlisted in the camera. Then, at that point, the confirmation happens. At whatever point the individual comes before the entryway, PIR sensor will detect the movement; LCD screen shows the necessary brief and the camera begins perceiving the face; it perceives the face, and on the off chance that it is enrolled, it opens the entryway; if the face is not enlisted, then it will raise a caution and snaps an image and sends it on the qualifications. This is the means by which the framework works.
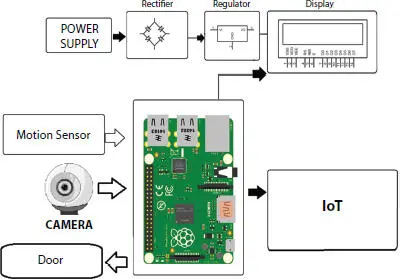
Figure 1.4 Block diagram of face recognition system.
SD card with 16GB capacity preinstalled with NOOBS.
For display and connectivity:
Any HDMI/DVI monitor or TV can be used for pi Display. HDMI cables will also be needed.
Keyboard and mouse: wireless will also work if already paired.
Power supply: USB cables can be used for this. Approximately, 2 A at 5 V will be needed to power the Raspberry Pi.
Make an account on iotgecko.com for authentication check.
If a person is unidentified, then a picture of is captured and sent to the website. All the monitoring data is sent over the website iotgecko.comso that the user can see the system status from anywhere and help boost the security.
Figure 1.5depicts the components used:
• Raspberry Pi 3 Model B+
• Camera
• Multimedia Mobile AUX System
• PCB
• 16X2 LCD Display
• DC Motor
1 1. Set up the Raspberry Pi.
2 2. Format the SD Card and install NOOBS software in it.
3 3. Now, put the SD card chip in the Raspberry Pi slot and connect it to the facility supply using an adapter.

Figure 1.5 Components of the system.
1 4. Connect the monitor to the Pi using HDMI cable, and therefore, the mode of the monitor/TV should be in HDMI.
2 5. Within the display an option would come to put in the software package. Click on Raspbian, so it will get installed after some minutes.
3 6. Perform all the language and display setting consistent with your preferences.
4 7. Now, we will start working with the software ( Figure 1.6Raspberry Pi).

Figure 1.6 Welcome to the Raspberry Pi desktop.

Figure 1.7 Setup.
1 8. Write the code on the Python3 IDE and upload it on to the Pi.
2 9. Now, make all the connections as per the circuit diagram.
3 10. Connect the full setup as per Figure 1.7.
4 11. Now, place on the whole system again and connect the chip with the code to the Pi.
5 12. In the beginning, connect your system to the net. All the prompts also will be heard and seen as we have got connected it to the Buzzer.
6 13. First, registration process will occur and that we register the authorized faces by clicking on the register option on the LCD with the assistance of keyboard as depicted in Figure 1.8.
7 14. In the display, the face registration process will be seen and therefore the images will get captured. We will also be able to input the name of the person here as depicted in Figure 1.9.
8 15. Click on start option, the method of door lock system will begin as depicted in Figure 1.10.

Figure 1.8 Options on display.

Figure 1.9 Image of registration.

Figure 1.10 LCD displaying door lock system.
1 16. For verification, when someone is available in front of the camera, the image gets captured.
2 17. If the person is registered, then the door opens, and it says welcome.
3 18. If the person is unknown, then the door remains closed, and it says invalid, gives a beep, and displays unknown face message as depicted in Figure 1.11.

Figure 1.11 Unknown face recognized.
1 19. All of these prompts are visible on the screen and the LCD display.
2 20. In case of an invalid entry the image of the individual is caught and given to the IoT geeks website for security purposes.
The face recognition technique possesses both demanding and significant technique of recognition. Among each biometrics methodology, face detection has some of the great advantages, i.e., it is totally user-friendly. In this research, all of us tried to give an introduction part for face detecting technology. We have covered the basics of this technology, the subparts of the machine learning need to be studied, the block diagram of this system, and the hardware components needed to be accumulated.
The computational models, which were executed in this undertaking, were taken after broad examination, and the fruitful testing results affirm that the decisions made by the researcher were reliable. This framework was tried under sturdy conditions in this exploratory study. The completely robotized front facing view face recognition framework showed basically wonderful precision.
The face recognition system with the latest technology is now cost effective, providing high percentage of accuracy and much more reliable system. This system possesses a high immense scope in India. This technique could be efficiently utilized in banks, universities, verification of driving license or visa and passport, in defense, and also in government as well as private sectors.
As an end, security system by using face acknowledgment got together with IoT is adequately done. The face acknowledgment can see the face and prepared to send notice to a customer when a dark being has been recognized through IoT. Of course, this endeavor is that this undertaking really has a significant room of progress to be done, especially in the viability of the image taking care of part. Due to the module used which is Raspberry Pi 3, taking care of period of the coding took a long time to measure the image taken and take an action. By using another better module, this endeavor can be improved remarkably.
Читать дальше




















