Chris McCain - Mastering VMware® Infrastructure3
Здесь есть возможность читать онлайн «Chris McCain - Mastering VMware® Infrastructure3» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Город: Indianapolis, Год выпуска: 2008, ISBN: 2008, Издательство: WILEY Wiley Publishing, Inc., Жанр: Программы, ОС и Сети, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Mastering VMware® Infrastructure3
- Автор:
- Издательство:WILEY Wiley Publishing, Inc.
- Жанр:
- Год:2008
- Город:Indianapolis
- ISBN:978-0-470-18313-7
- Рейтинг книги:5 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 100
- 1
- 2
- 3
- 4
- 5
Mastering VMware® Infrastructure3: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Mastering VMware® Infrastructure3»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Mastering VMware® Infrastructure3 — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Mastering VMware® Infrastructure3», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
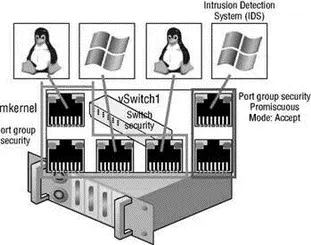
Figure 3.37Promiscuous mode, though a reduction in security, is required when using an intrusion detection system.
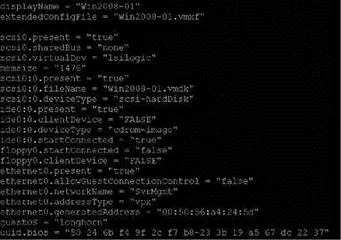
Figure 3.38A virtual machine's initial MAC address is automatically generated and listed in the configuration file for the virtual machine.
Manually configuring a MAC address in the configuration file of a virtual machine will not work unless the first three bytes are VMware-provided prefixes and the last three bytes are unique. If a non-VMware MAC prefix is entered in the configuration file, the virtual machine will not power on.
All virtual machines have two MAC addresses: the initial MAC and the effective MAC. The initial MAC address is the MAC discussed in the previous paragraph that is generated automatically and that resides in the configuration file. The guest operating system has no control over the initial MAC address. The effective MAC address is the MAC address configured by the guest operating system that is used during communication with other systems. The effective MAC address is included in network communication as the source MAC of the virtual machine. By default, these two addresses are identical. To force a non-VMware-assigned MAC address to a guest operating system, change the effective MAC address from within the guest operating system, as shown in Figure 3.39.
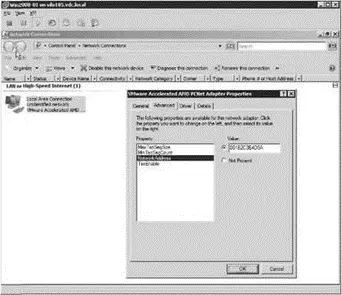
Figure 3.39A virtual machine's source MAC address is the effective MAC address, which by default matches the initial MAC address configured in the VMX file. The effective MAC, however, can be changed in the guest operating system.
The ability to alter the effective MAC address cannot be removed from the guest operating system. However, the ability to let the system function with this altered MAC address is easily addressable through the security policy of a vSwitch. The remaining two settings of a virtual switch security policy are MAC Address Changes and Forged Transmits. Both of these security policies are concerned with allowing or denying differences between the initial MAC address in the configuration file and the effective MAC address in the guest operating system. As noted earlier, the default virtual switch security is to accept the differences and process traffic as needed.
The difference between the MAC Address Changes and Forged Transmits security settings involves the direction of the traffic. MAC Address Changes is concerned with the integrity of incoming traffic, while Forged Transmits oversees the integrity of outgoing traffic. If the MAC Address Changes option is set to Reject, traffic will not be passed through the vSwitch to the virtual machine (incoming) if the initial and the effective MAC addresses do not match. If the Forged Transmits option is set to Reject, traffic will not be passed from the virtual machine to the vSwitch (outgoing) if the initial and the effective MAC addresses do not match. Figure 3.40 highlights the security restrictions implemented when MAC Address Changes and Forged Transmits are set to Reject.
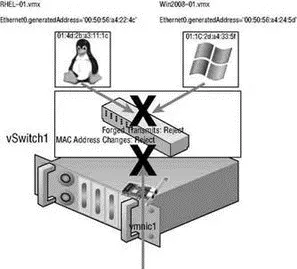
Figure 3.40The MAC Address Changes and Forged Transmits security options deal with incoming and outgoing traffic respectively.
For the highest level of security, VMware recommends setting MAC Address Changes, Forged Transmits, and Promiscuous Mode on each vSwitch to Reject. When warranted or necessary, use port groups to loosen the security for a subset of virtual machines to connect to the port group.
Real World Scenario
As with anything, there are, of course, exceptions. For virtual machines that will be configured as part of a Microsoft network load balancing (NLB) cluster set in Unicast mode, the virtual machine port group must allow MAC Address Changes and Forged Transmits. Systems that are part of an NLB cluster will share a common IP address and virtual MAC address, as shown here:
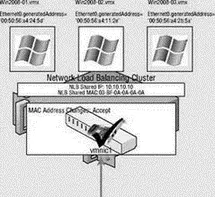
The shared virtual MAC address is generated by using an algorithm that includes a static component based on the NLB cluster's configuration of Unicast or Multicast mode plus a hexadecimal representation of the four octets that make up the IP address. This shared MAC address will certainly differ from the MAC address defined in the VMX file of the virtual machine. If the virtual machine port group does not allow for differences between the MAC addresses in the VMX and guest operating system, NLB will not function as expected. VMware recommends running NLB clusters in Multicast mode due to these issues with NLB clusters in Unicast mode.
Perform the following steps to edit the security profile of a vSwitch:
1. Use the VI Client to establish a connection to a VirtualCenter server or an ESX Server host.
2. Click the hostname in the inventory panel on the left, select the Configuration tab from the details pane on the right, and then select Networking from the Hardware menu list.
3. Click the Properties link for the virtual switch.
4. Click the name of the virtual switch under the Configuration list and then click the Edit button.
5. Click the Security tab and make the necessary adjustments.
6. Click OK and then click Close.
Follow these steps to edit the security profile of a port group:
1. Use the VI Client to establish a connection to a VirtualCenter server or an ESX Server host.
2. Click the hostname in the inventory panel on the left, select the Configuration tab from the details pane on the right, and then select Networking from the Hardware menu list.
3. Click the Properties link for the virtual switch.
4. Click the name of the port group under the Configuration list and then click the Edit button.
5. Click the Security tab and make the necessary adjustments.
6. Click OK and then click Close.
Managing the security of a virtual network architecture is much the same as managing the security for any other portion of your information systems. Security policy should dictate that settings be configured as secure as possible to err on the side of caution. Only with proper authorization, documentation, and change management processes should security be reduced. In addition, the reduction in security should be as controlled as possible to affect the least number of systems if not just the systems requiring the adjustments.
The Bottom Line
Identify the components of virtual networking. Virtual networking is made up of a combination of relationships that exist between the logical networking components created in the VMkernel of ESX Server and the physical network devices. The virtual machines are configured on vSwitches bound to physical network adapters that are connected to physical switches.
Create virtual switches and virtual switch port groups. Virtual switches, ports, and port groups are the cornerstone of the virtual networking architecture. These virtual components provide the tools for connecting to the physical network components to allow communication between the virtual and physical environments.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Mastering VMware® Infrastructure3»
Представляем Вашему вниманию похожие книги на «Mastering VMware® Infrastructure3» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Mastering VMware® Infrastructure3» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












