Chris McCain - Mastering VMware® Infrastructure3
Здесь есть возможность читать онлайн «Chris McCain - Mastering VMware® Infrastructure3» — ознакомительный отрывок электронной книги совершенно бесплатно, а после прочтения отрывка купить полную версию. В некоторых случаях можно слушать аудио, скачать через торрент в формате fb2 и присутствует краткое содержание. Город: Indianapolis, Год выпуска: 2008, ISBN: 2008, Издательство: WILEY Wiley Publishing, Inc., Жанр: Программы, ОС и Сети, на английском языке. Описание произведения, (предисловие) а так же отзывы посетителей доступны на портале библиотеки ЛибКат.
- Название:Mastering VMware® Infrastructure3
- Автор:
- Издательство:WILEY Wiley Publishing, Inc.
- Жанр:
- Год:2008
- Город:Indianapolis
- ISBN:978-0-470-18313-7
- Рейтинг книги:5 / 5. Голосов: 1
-
Избранное:Добавить в избранное
- Отзывы:
-
Ваша оценка:
- 100
- 1
- 2
- 3
- 4
- 5
Mastering VMware® Infrastructure3: краткое содержание, описание и аннотация
Предлагаем к чтению аннотацию, описание, краткое содержание или предисловие (зависит от того, что написал сам автор книги «Mastering VMware® Infrastructure3»). Если вы не нашли необходимую информацию о книге — напишите в комментариях, мы постараемся отыскать её.
Mastering VMware® Infrastructure3 — читать онлайн ознакомительный отрывок
Ниже представлен текст книги, разбитый по страницам. Система сохранения места последней прочитанной страницы, позволяет с удобством читать онлайн бесплатно книгу «Mastering VMware® Infrastructure3», без необходимости каждый раз заново искать на чём Вы остановились. Поставьте закладку, и сможете в любой момент перейти на страницу, на которой закончили чтение.
Интервал:
Закладка:
♦ Disable Spanning Tree Protocol (STP)
VMware recommends configuring Cisco devices to use PortFast mode for access interfaces or PortFast trunk mode for trunking interfaces.
Creating and Managing VLANs
To vLAN or not to vLAN? That is the question. As defined in the first section, a virtual LAN (vLAN) is a logical LAN configured on a virtual or physical switch port that provides efficient traffic segmentation, security, and efficient bandwidth utilization by providing traffic only to the ports configured for a respective vLAN. In addition to the security and segmentation advantages, vLANs allow network administrators to exceed the physical distance limitations of standard cabling. Using vLANs is advantageous when an ESX Server host has a limited number of physical network adapters.
Figure 3.32 shows a typical vLAN configuration across physical switches.
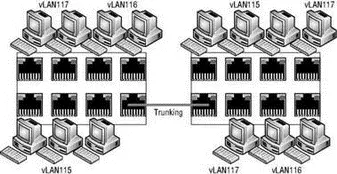
Figure 3.32Virtual LANs provide secure traffic segmentation without the cost of additional hardware.
Virtual switches in the VMkernel do not need vLANs if an ESX Server host has enough physical network adapters to connect to each of the vLAN subnets.
Blade servers provide an excellent example of when vLANs offer tremendous benefit, because the blade servers offer limited expansion slots for physical network adapters due to the small form factor of the blade casing. Figure 3.33 shows a vSwitch architecture with vLANs as it integrates with a physical architecture also using vLANs. For a vSwitch to successfully send and receive packets tagged as one vLAN or another, a trunk port must be configured on the physical switch port to which the physical network adapter assigned to the vSwitch is connected.
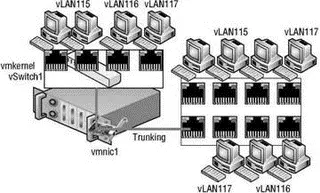
Figure 3.33The physical switch port to which a vSwitch's assigned physical network adapter is connected must be configured as a trunk port for vLAN tagging to work between virtual and physical switches.
Follow these steps to configure a vSwitch with a virtual machine port group with a vLAN using an ID of VLAN 117:
1. Use the VI Client to establish a connection to a VirtualCenter server or an ESX Server host.
2. Click the hostname in the inventory panel on the left, select the Configuration tab from the details pane on the right, and then select Networking from the Hardware menu list.
3. Click the Properties link for the vSwitch where the new vLAN should be created.
4. Click the Add button, select the Virtual Machine radio button option, and then click Next.
5. Type the name of the virtual machine port group in the Network Label text box. In this case, vLAN117would be appropriate.
6. Type 117in the VLAN ID (Optional) text box, as shown in Figure 3.34.
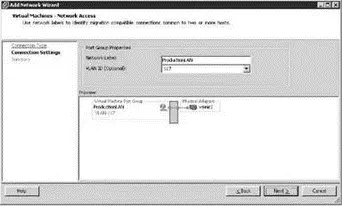
Figure 3.34The vLAN tagging support of vSwitches simplifies integration with existing physical hardware configured with vLANs.
7. Click Next to review the vSwitch configuration and then click Finish.
Although vLANs reduce the costs of constructing multiple logical subnets, keep in mind that the contention through physical switches and network adapters is still present. For bandwidth-intensive network operations, the disadvantage of the shared physical network might outweigh the scalability and cost savings of the vLAN.
Configuring Virtual Switch Security
Even though the vSwitches created in the VMkernel are considered to be “dumb switches”, they can be configured with vSwitch security policies to enhance or ensure Layer 2 security. Security policies can be applied at the vSwitch or at the lower-level connection types configured on a vSwitch and include the following three security options:
♦ Promiscuous Mode
♦ MAC Address Changes
♦ Forged Transmits
Applying a security policy to the vSwitch is effective, by default, for all connection types within the switch. However, if a connection type, or port group, is configured with a competing security policy, it will override the policy set at the vSwitch. As in the example in Figure 3.35, if a vSwitch is configured with a security policy that rejects the use of MAC address changes but a virtual machine port group on the switch is configured to accept MAC address changes, then any virtual machines connected to that port group will be allowed to communicate even though it is using a MAC address that differs from what is configured in its VMX file.
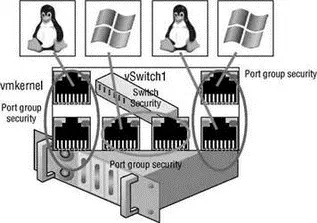
Figure 3.35 Security policies at the switch level are effective by default for all connection types on the switch. Security policies at the connection type (port group) level override the policy set at the virtual switch.
The default security profile for a vSwitch, shown in Figure 3.36, is set to reject Promiscuous mode and to accept MAC address changes and Forged transmits.
Promiscuous Mode
The Promiscuous Mode option is set to Reject by default to prevent virtual network adapters from observing any of the traffic submitted through the vSwitch. For enhanced security, allowing Promiscuous mode is not recommended because it is an insecure mode of operation that allows virtual adapters to access traffic other than its own. Despite the security concerns, there are valid reasons for permitting a switch to operate in Promiscuous mode. An intrusion detection system (IDS) requires the ability to identify all traffic to scan for anomalies and malicious patterns of traffic. To support the use of the IDS without overextending the reduced security of Promiscuous mode, you can create a dedicated virtual machine port group for use with the IDS. As shown in Figure 3.37, the virtual switch security policy will remain at the default setting of Reject for the Promiscuous Mode option, while the virtual machine port group for the IDS will be set to Accept. This setting will override the virtual switch, allowing the IDS to monitor all switch traffic.
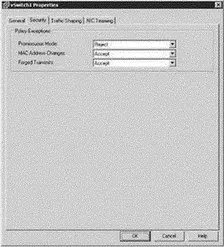
Figure 3.36The default security profile for a virtual switch prevents Promiscuous Mode but allows MAC Address Changes and Forged transmits.
MAC Address Changes and Forged Transmits
When a virtual machine is created with one or more virtual network adapters, a MAC address is generated for each virtual adapter. Just as Intel, Broadcom, and others manufacture network adapters and include unique MAC address strings, VMware is also a network adapter manufacturer that has its own MAC prefix to ensure uniqueness. Of course, VMware doesn't actually manufacture anything, since the product exists as a virtual NIC in a virtual machine. The six-byte, randomly generated MAC addresses for a virtual machine can be seen in the configuration file (.vmx) of the virtual machine, as shown in Figure 3.38. A VMware-assigned MAC address begins with the prefix 00:50:56 or 00:0C:29. The value of the fourth set (XX) cannot exceed 3F to prevent conflicts with other VMware products, while the fifth and sixth sets (YY:ZZ) are generated randomly based on the Universally Unique Identifier (UUID) of the virtual machine that is tied to the location of the virtual machine. For this reason, when a virtual machine location is changed a prompt will appear prior to successful boot. The prompt will inquire about keeping the UUID or generating a new UUID, which helps prevent MAC address conflicts.
Читать дальшеИнтервал:
Закладка:
Похожие книги на «Mastering VMware® Infrastructure3»
Представляем Вашему вниманию похожие книги на «Mastering VMware® Infrastructure3» списком для выбора. Мы отобрали схожую по названию и смыслу литературу в надежде предоставить читателям больше вариантов отыскать новые, интересные, ещё непрочитанные произведения.
Обсуждение, отзывы о книге «Mastering VMware® Infrastructure3» и просто собственные мнения читателей. Оставьте ваши комментарии, напишите, что Вы думаете о произведении, его смысле или главных героях. Укажите что конкретно понравилось, а что нет, и почему Вы так считаете.












