6.After the wizard signs the zone, click Finish.
To sign a zone and use existing signing parameters, follow these steps:
1.In the DNS Manager console, press and hold or right-click the zone you want to secure. On the shortcut menu, select DNSSEC and then select Sign The Zone. This starts the Zone Signing Wizard. If the wizard displays a welcome page, read the Welcome text, and then tap or click Next.
2.On the Signing Options page, select Sign The Zone With Parameters Of An Existing Zone. Enter the name of an existing signed zone, such as cpandl.com, and then tap or click Next.
3.On the Key Master page, select a key master for the zone. Any authoritative server that hosts a primary copy of a zone can act as the key master. Tap or click Next twice.
4.After the wizard signs the zone, tap or click Finish.
Creating child domains within zones
By using the DNS Manager console, you can create child domains within a zone. For example, if you create the primary zone microsoft.com, you could create the subdomains hr.microsoft.com and mis.microsoft.com for the zone.
You create child domains by following these steps:
1.In the DNS Manager console, expand the Forward Lookup Zones folder for the server with which you want to work.
2.Press and hold or right-click the parent domain entry, and then tap or click New Domain.
3.Enter the name of the new domain, and then tap or click OK. For hr.microsoft.com, you would enter hr. For mis.microsoft.com, you would enter mis.
Creating child domains in separate zones
As your organization grows, you might want to organize the DNS namespace into separate zones. At your corporate headquarters, you could have a zone for the parent domain microsoft.com. At branch offices, you could have zones for each office, such as memphis.microsoft.com, newyork.microsoft.com, and la.microsoft.com.
You create child domains in separate zones by following these steps:
1.Install a DNS server in each child domain, and then create the necessary forward and reverse lookup zones for the child domain as described earlier in “Installing DNS Servers.”
2.On the authoritative DNS server for the parent domain, you delegate authority to each child domain. Delegating authority enables the child domain to resolve and respond to DNS queries from computers inside and outside the local subnet.
You delegate authority to a child domain by following these steps:
1.In the DNS Manager console, expand the Forward Lookup Zones folder for the server with which you want to work.
2.Press and hold or right-click the parent domain entry, and then tap or click New Delegation to start the New Delegation Wizard. Tap or click Next.
3.As shown in Figure 9–5, enter the name of the delegated domain, such as service, and then tap or click Next. The name you enter updates the value in the Fully Qualified Domain Name text box.
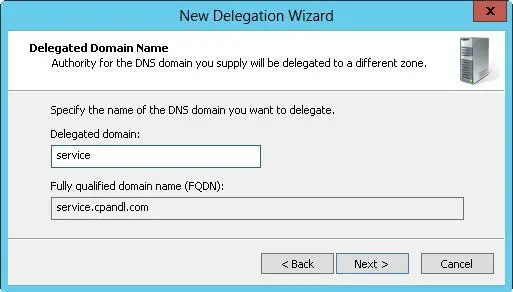
FIGURE 9–5Entering the name of the delegated domain sets the fully qualified domain name (FQDN).
4.Tap or click Add. This displays the New Name Server Record dialog box.
5.In the Server Fully Qualified Domain Name text box, type the fully qualified host name of a DNS server for the child domain, such as corpserver01.memphis.adatum.com, and then tap or click Resolve. The server then performs a lookup query and adds the resolved IP address to the IP Address list.
6.Repeat step 5 to specify additional name servers. The order of the entries determines which IP address is used first. Change the order as necessary by using the Up and Down buttons. When you are ready to continue, tap or click OK to close the New Name Server Record dialog box.
7.Tap or click Next, and then tap or click Finish.
Deleting a domain or subnet
Deleting a domain or subnet permanently removes it from the DNS server. To delete a domain or subnet, follow these steps:
1.In the DNS Manager console, press and hold or right-click the domain or subnet entry.
2.On the shortcut menu, tap or click Delete, and then confirm the action by tapping or clicking Yes.
3.If the domain or subnet is integrated with Active Directory, you’ll receive a warning prompt. Confirm that you want to delete the domain or subnet from Active Directory by tapping or clicking Yes.
NOTE Deleting a domain or subnet deletes all DNS records in a zone file but doesn’t actually delete the zone file on a primary or secondary server that isn’t integrated with Active Directory. The actual zone file remains in the %SystemRoot%\System32\Dns directory. You can delete this file after you have deleted the zones from the DNS Manager console.

After you create the necessary zone files, you can add records to the zones. Computers that need to be accessed from Active Directory and DNS domains must have DNS records. Although there are many types of DNS records, most of these record types aren’t commonly used. So rather than focus on record types you probably won’t use, let’s focus on the ones you will use:
■ A (IPv4 address)Maps a host name to an IPv4 address. When a computer has multiple adapter cards, IPv4 addresses, or both, it should have multiple address records.
■ AAAA (IPv6 address)Maps a host name to an IPv6 address. When a computer has multiple adapter cards, IPv6 addresses, or both, it should have multiple address records.
■ CNAME (canonical name)Sets an alias for a host name. For example, by using this record, zeta.microsoft.com can have an alias of www.microsoft.com.
■ MX (mail exchanger)Specifies a mail exchange server for the domain, which enables email messages to be delivered to the correct mail servers in the domain.
■ NS (name server)Specifies a name server for the domain, which enables DNS lookups within various zones. Each primary and secondary name server should be declared through this record.
■ PTR (pointer)Creates a pointer that maps an IP address to a host name for reverse lookups.
■ SOA (start of authority)Declares the host that’s the most authoritative for the zone and, as such, is the best source of DNS information for the zone. Each zone file must have an SOA record (which is created automatically when you add a zone). Also declares other information about the zone, such as the responsible person, refresh interval, retry interval, and so on.
■ SRV (service location)Locates a server providing a specific service. Active Directory uses SRV records to locate domain controllers, global catalog servers, LDAP servers, and Kerberos servers. Most SRV records are created automatically. For example, Active Directory creates an SRV record when you promote a domain controller. LDAP servers can add an SRV record to indicate they are available to handle LDAP requests in a particular zone.
Adding address and pointer records
Читать дальше








