SECURITY ALERT Before you designate additional recovery agents, you should consider setting up a root certificate authority (CA) in the domain. Then you can use the Certificates snap-in to generate a personal certificate that uses the EFS Recovery Agent template. The root CA must then approve the certificate request so that the certificate can be used.
6.To delete a recovery agent, select the recovery agent’s certificate in the right pane, and then press Delete. When prompted to confirm the action, tap or click Yes to permanently and irrevocably delete the certificate. If the recovery policy is empty (meaning that it has no other designated recovery agents), EFS will be turned off so that files can no longer be encrypted; existing EFSencrypted resources won’t have a recovery agent.
Decrypting files and directories
File Explorer shows names of encrypted resources in green. If you want to decrypt a file or directory, follow these steps:
1.In File Explorer, press and hold or right-click the file or directory, and then tap or click Properties.
2.On the General tab of the Properties dialog box, tap or click Advanced. Clear the Encrypt Contents To Secure Data check box. Tap or click OK twice.
With files, Windows Server decrypts the file and restores it to its original format. With directories, Windows Server decrypts all the files within the directory. If the directory contains subfolders, you also have the option to remove encryption from the subfolders. To do this, select Apply Changes To This Folder, Subfolders, And Files when prompted, and then tap or click OK.
TIP Windows Server also provides a command-line utility called Cipher (Cipher. exe) for encrypting and decrypting your data. entering cipher at a command prompt without additional parameters shows you the encryption status of all folders in the current directory.

CHAPTER 2: Configuring storage
■Using volumes and volume sets
■Improving performance and fault tolerance with RAID
■Implementing RAID on Windows Server 2012 R2
■Managing RAID and recovering from failures
■Standards-based storage management
■Managing existing partitions and drives
Storage management and the ways in which Windows Server works with disks have changed substantially over the past few years. Although traditional storage management techniques relate to physical drives located inside the server, many servers today use attached storage and virtual disks.
Generally, when you work with internal fixed drives, you often need to perform advanced disk setup procedures, such as creating a volume set or setting up a redundant array of independent disks (RAID) array. Here, you create volumes or arrays that can span multiple drives and you know the exact physical layout of those drives.
However, when you work with attached storage, you might not know which actual physical disk or disks the volume you are working with resides on. Instead, you are presented with a virtual disk, also referred to as a logical unit number (LUN), which is a logical reference to a portion of the storage subsystem. Although the virtual disk can reside on one or more physical disks (spindles), the layout of the physical disks is controlled separately from the operating system (by the storage subsystem).
When I need to differentiate between the two storage management approaches, I refer to the former technique as traditional and the latter technique as standards-based . In this chapter, I look at traditional techniques for creating volume sets and arrays first, and then I look at standards-based techniques for creating volumes.
Whether a volume is created by using the traditional approach or the standards-based approach, you manage it by using similar techniques. For this reason, in the final section of this chapter, I discuss techniques for working with existing volumes and drives.
REAL WORLD Standards-based approaches to storage management can also be used with a server’s internal disks. When internal disks are used in this way, however, the internal disks-such as virtual disks on attached storage-are resources to be allocated by using standards-based approaches. This means you can create virtual disk volumes on the physical disks, add the physical disks to storage pools, and create Internet SCSI (iSCSI) virtual disks that can be targeted. You can also enable data deduplication on your virtual disks. You can’t, however, use the operating system’s volume set or RAID array features, because standards-based, storage management approaches rely on the storage subsystem to manage the physical disk architecture.
Using volumes and volume sets

You create volume sets and RAID arrays on dynamic drives. With a volume set, you can create a single volume that spans multiple drives. Users can access this volume as if it were a single drive, regardless of how many drives the volume is spread over. A volume that’s on a single drive is referred to as a simple volume . A volume that spans multiple drives is referred to as a spanned volume .
With a RAID array, you can protect important business data and sometimes improve the performance of drives. RAID can be implemented by using the built-in features of the operating system (a software approach) or by using hardware. Windows Server 2012 R2 supports three levels of software RAID: 0, 1, and 5. RAID arrays are implemented as mirrored, striped, and striped with parity volumes.
You create and manage volumes in much the same way in which you create and manage partitions. A volume is a drive section you can use to store data directly.
NOTE With spanned and striped volumes on basic disks, you can delete a volume but you can’t create or extend volumes. With mirrored volumes on basic disks, you can delete, repair, and resync the mirror. You can also break the mirror. For striped with parity volumes (RAID-5) on basic disks, you can delete or repair the volume, but you can’t create new volumes.
Understanding volume basics
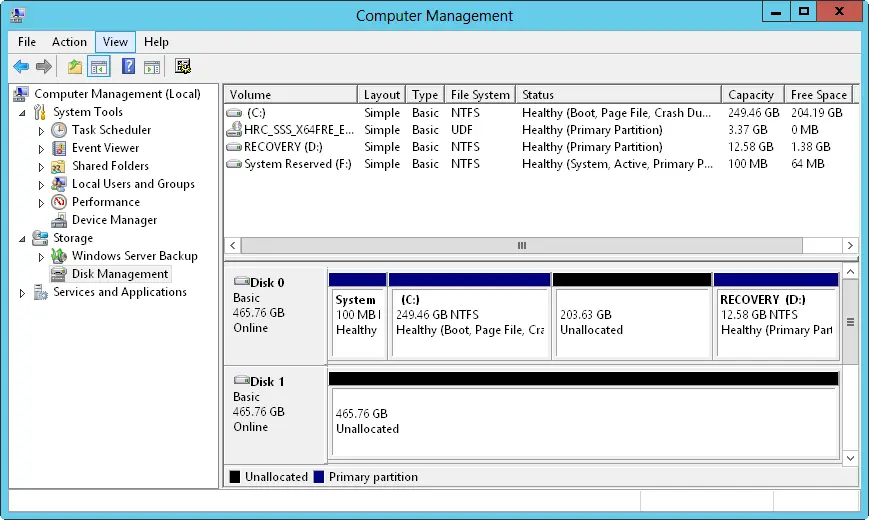
Disk Management color codes volumes by type, much like it does partitions. As Figure 2–1 shows, volumes also have the following properties:
■ LayoutVolume layouts include simple, spanned, mirrored, striped, and striped with parity.
■ TypeVolumes always have the type dynamic . Partitions always have the type basic .
■ File SystemLike partitions, each volume can have a different file system type, such as FAT or NTFS file system. Note that FAT16 is available only when the partition or volume is 2 GB or less in size.
■ StatusThe state of the drive. In Graphical View, the state is shown as Healthy, Failed Redundancy, and so on. The next section, “Understanding volume sets,” discusses volume sets and the various states you might encounter.
■ CapacityThe total storage size of the drive.
■ Free SpaceThe total amount of available space on the volume.
■ % FreeThe percentage of free space out of the total storage size of the volume.
Читать дальше









